hyperledger fabric2.4测试网络添加组织数量
!!!修改内容比较繁琐,预期未来提供模板修改
修改初始配置文件,初始添加3个组织
organizations文件夹
/cryptogen文件夹下创建文件crypto-config-org3.yaml,内容如下:
PeerOrgs:
# ---------------------------------------------------------------------------
# Org3
# ---------------------------------------------------------------------------
- Name: Org3
Domain: org3.example.com
EnableNodeOUs: true
Template:
Count: 1
SANS:
- localhost
Users:
Count: 1
在/fabric-ca/org3文件夹中创建fabric-ca-server-config.yaml,内容如下:
version: 1.2.0
port: 11054
debug: false
crlsizelimit: 512000
tls:
enabled: true
certfile:
keyfile:
clientauth:
type: noclientcert
certfiles:
ca:
name: Org3CA
keyfile:
certfile:
chainfile:
crl:
expiry: 24h
registry:
maxenrollments: -1
identities:
- name: admin
pass: adminpw
type: client
affiliation: ""
attrs:
hf.Registrar.Roles: "*"
hf.Registrar.DelegateRoles: "*"
hf.Revoker: true
hf.IntermediateCA: true
hf.GenCRL: true
hf.Registrar.Attributes: "*"
hf.AffiliationMgr: true
db:
type: sqlite3
datasource: fabric-ca-server.db
tls:
enabled: false
certfiles:
client:
certfile:
keyfile:
ldap:
enabled: false
url: ldap://<adminDN>:<adminPassword>@<host>:<port>/<base>
tls:
certfiles:
client:
certfile:
keyfile:
attribute:
names: ['uid','member']
converters:
- name:
value:
maps:
groups:
- name:
value:
affiliations:
org1:
- department1
- department2
org2:
- department1
signing:
default:
usage:
- digital signature
expiry: 8760h
profiles:
ca:
usage:
- cert sign
- crl sign
expiry: 43800h
caconstraint:
isca: true
maxpathlen: 0
tls:
usage:
- signing
- key encipherment
- server auth
- client auth
- key agreement
expiry: 8760h
csr:
cn: ca.org3.example.com
names:
- C: US
ST: "North Carolina"
L: "Raleigh"
O: org3.example.com
OU:
hosts:
- localhost
- org3.example.com
ca:
expiry: 131400h
pathlength: 1
bccsp:
default: SW
sw:
hash: SHA2
security: 256
filekeystore:
keystore: msp/keystore
cacount:
cafiles:
intermediate:
parentserver:
url:
caname:
enrollment:
hosts:
profile:
label:
tls:
certfiles:
client:
certfile:
keyfile:
修改/fabric-ca中的registerEnroll.sh,添加如下内容:
function createOrg3() {
infoln "Enrolling the CA admin"
mkdir -p organizations/peerOrganizations/org3.example.com/
export FABRIC_CA_CLIENT_HOME=${PWD}/organizations/peerOrganizations/org3.example.com/
set -x
fabric-ca-client enroll -u https://admin:adminpw@localhost:11054 --caname ca-org3 --tls.certfiles "${PWD}/organizations/fabric-ca/org3/ca-cert.pem"
{ set +x; } 2>/dev/null
echo 'NodeOUs:
Enable: true
ClientOUIdentifier:
Certificate: cacerts/localhost-11054-ca-org3.pem
OrganizationalUnitIdentifier: client
PeerOUIdentifier:
Certificate: cacerts/localhost-11054-ca-org3.pem
OrganizationalUnitIdentifier: peer
AdminOUIdentifier:
Certificate: cacerts/localhost-11054-ca-org3.pem
OrganizationalUnitIdentifier: admin
OrdererOUIdentifier:
Certificate: cacerts/localhost-11054-ca-org3.pem
OrganizationalUnitIdentifier: orderer' > "${PWD}/organizations/peerOrganizations/org3.example.com/msp/config.yaml"
# Since the CA serves as both the organization CA and TLS CA, copy the org's root cert that was generated by CA startup into the org level ca and tlsca directories
# Copy org3's CA cert to org3's /msp/tlscacerts directory (for use in the channel MSP definition)
mkdir -p "${PWD}/organizations/peerOrganizations/org3.example.com/msp/tlscacerts"
cp "${PWD}/organizations/fabric-ca/org3/ca-cert.pem" "${PWD}/organizations/peerOrganizations/org3.example.com/msp/tlscacerts/ca.crt"
# Copy org3's CA cert to org3's /tlsca directory (for use by clients)
mkdir -p "${PWD}/organizations/peerOrganizations/org3.example.com/tlsca"
cp "${PWD}/organizations/fabric-ca/org3/ca-cert.pem" "${PWD}/organizations/peerOrganizations/org3.example.com/tlsca/tlsca.org3.example.com-cert.pem"
# Copy org3's CA cert to org3's /ca directory (for use by clients)
mkdir -p "${PWD}/organizations/peerOrganizations/org3.example.com/ca"
cp "${PWD}/organizations/fabric-ca/org3/ca-cert.pem" "${PWD}/organizations/peerOrganizations/org3.example.com/ca/ca.org3.example.com-cert.pem"
infoln "Registering peer0"
set -x
fabric-ca-client register --caname ca-org3 --id.name peer0 --id.secret peer0pw --id.type peer --tls.certfiles "${PWD}/organizations/fabric-ca/org3/ca-cert.pem"
{ set +x; } 2>/dev/null
infoln "Registering user"
set -x
fabric-ca-client register --caname ca-org3 --id.name user1 --id.secret user1pw --id.type client --tls.certfiles "${PWD}/organizations/fabric-ca/org3/ca-cert.pem"
{ set +x; } 2>/dev/null
infoln "Registering the org admin"
set -x
fabric-ca-client register --caname ca-org3 --id.name org3admin --id.secret org3adminpw --id.type admin --tls.certfiles "${PWD}/organizations/fabric-ca/org3/ca-cert.pem"
{ set +x; } 2>/dev/null
infoln "Generating the peer0 msp"
set -x
fabric-ca-client enroll -u https://peer0:peer0pw@localhost:11054 --caname ca-org3 -M "${PWD}/organizations/peerOrganizations/org3.example.com/peers/peer0.org3.example.com/msp" --tls.certfiles "${PWD}/organizations/fabric-ca/org3/ca-cert.pem"
{ set +x; } 2>/dev/null
cp "${PWD}/organizations/peerOrganizations/org3.example.com/msp/config.yaml" "${PWD}/organizations/peerOrganizations/org3.example.com/peers/peer0.org3.example.com/msp/config.yaml"
infoln "Generating the peer0-tls certificates, use --csr.hosts to specify Subject Alternative Names"
set -x
fabric-ca-client enroll -u https://peer0:peer0pw@localhost:11054 --caname ca-org3 -M "${PWD}/organizations/peerOrganizations/org3.example.com/peers/peer0.org3.example.com/tls" --enrollment.profile tls --csr.hosts peer0.org3.example.com --csr.hosts localhost --tls.certfiles "${PWD}/organizations/fabric-ca/org3/ca-cert.pem"
{ set +x; } 2>/dev/null
# Copy the tls CA cert, server cert, server keystore to well known file names in the peer's tls directory that are referenced by peer startup config
cp "${PWD}/organizations/peerOrganizations/org3.example.com/peers/peer0.org3.example.com/tls/tlscacerts/"* "${PWD}/organizations/peerOrganizations/org3.example.com/peers/peer0.org3.example.com/tls/ca.crt"
cp "${PWD}/organizations/peerOrganizations/org3.example.com/peers/peer0.org3.example.com/tls/signcerts/"* "${PWD}/organizations/peerOrganizations/org3.example.com/peers/peer0.org3.example.com/tls/server.crt"
cp "${PWD}/organizations/peerOrganizations/org3.example.com/peers/peer0.org3.example.com/tls/keystore/"* "${PWD}/organizations/peerOrganizations/org3.example.com/peers/peer0.org3.example.com/tls/server.key"
infoln "Generating the user msp"
set -x
fabric-ca-client enroll -u https://user1:user1pw@localhost:11054 --caname ca-org3 -M "${PWD}/organizations/peerOrganizations/org3.example.com/users/User1@org3.example.com/msp" --tls.certfiles "${PWD}/organizations/fabric-ca/org3/ca-cert.pem"
{ set +x; } 2>/dev/null
cp "${PWD}/organizations/peerOrganizations/org3.example.com/msp/config.yaml" "${PWD}/organizations/peerOrganizations/org3.example.com/users/User1@org3.example.com/msp/config.yaml"
infoln "Generating the org admin msp"
set -x
fabric-ca-client enroll -u https://org3admin:org3adminpw@localhost:11054 --caname ca-org3 -M "${PWD}/organizations/peerOrganizations/org3.example.com/users/Admin@org3.example.com/msp" --tls.certfiles "${PWD}/organizations/fabric-ca/org3/ca-cert.pem"
{ set +x; } 2>/dev/null
cp "${PWD}/organizations/peerOrganizations/org3.example.com/msp/config.yaml" "${PWD}/organizations/peerOrganizations/org3.example.com/users/Admin@org3.example.com/msp/config.yaml"
}
ccp-generate.sh中添加如下代码
ORG=3
P0PORT=11051
CAPORT=11054
PEERPEM=organizations/peerOrganizations/org3.example.com/tlsca/tlsca.org3.example.com-cert.pem
CAPEM=organizations/peerOrganizations/org3.example.com/ca/ca.org3.example.com-cert.pem
echo "$(json_ccp $ORG $P0PORT $CAPORT $PEERPEM $CAPEM)" > organizations/peerOrganizations/org3.example.com/connection-org3.json
echo "$(yaml_ccp $ORG $P0PORT $CAPORT $PEERPEM $CAPEM)" > organizations/peerOrganizations/org3.example.com/connection-org3.yaml
test-network文件夹
在setOrgEnv.sh中添加如下内容
elif [[ ${ORG,,} == "org3" ]]; then
CORE_PEER_LOCALMSPID=Org3MSP
CORE_PEER_MSPCONFIGPATH=${DIR}/test-network/organizations/peerOrganizations/org3.example.com/users/Admin@org3.example.com/msp
CORE_PEER_ADDRESS=localhost:11051
CORE_PEER_TLS_ROOTCERT_FILE=${DIR}/test-network/organizations/peerOrganizations/org3.example.com/tlsca/tlsca.org3.example.com-cert.pem
compose文件夹
compose-ca.yaml添加如下内容:
ca_org3:
image: hyperledger/fabric-ca:latest
labels:
service: hyperledger-fabric
environment:
- FABRIC_CA_HOME=/etc/hyperledger/fabric-ca-server
- FABRIC_CA_SERVER_CA_NAME=ca-org3
- FABRIC_CA_SERVER_TLS_ENABLED=true
- FABRIC_CA_SERVER_PORT=11054
- FABRIC_CA_SERVER_OPERATIONS_LISTENADDRESS=0.0.0.0:19054
ports:
- "11054:11054"
- "19054:19054"
command: sh -c 'fabric-ca-server start -b admin:adminpw -d'
volumes:
- ../organizations/fabric-ca/org3:/etc/hyperledger/fabric-ca-server
container_name: ca_org3
networks:
- test
compose-couch.yaml添加如下内容
couchdb2:
container_name: couchdb2
image: couchdb:3.2.2
labels:
service: hyperledger-fabric
# Populate the COUCHDB_USER and COUCHDB_PASSWORD to set an admin user and password
# for CouchDB. This will prevent CouchDB from operating in an "Admin Party" mode.
environment:
- COUCHDB_USER=admin
- COUCHDB_PASSWORD=adminpw
# Comment/Uncomment the port mapping if you want to hide/expose the CouchDB service,
# for example map it to utilize Fauxton User Interface in dev environments.
ports:
- "9984:5984"
networks:
- test
peer0.org3.example.com:
environment:
- CORE_LEDGER_STATE_STATEDATABASE=CouchDB
- CORE_LEDGER_STATE_COUCHDBCONFIG_COUCHDBADDRESS=couchdb4:5984
# The CORE_LEDGER_STATE_COUCHDBCONFIG_USERNAME and CORE_LEDGER_STATE_COUCHDBCONFIG_PASSWORD
# provide the credentials for ledger to connect to CouchDB. The username and password must
# match the username and password set for the associated CouchDB.
- CORE_LEDGER_STATE_COUCHDBCONFIG_USERNAME=admin
- CORE_LEDGER_STATE_COUCHDBCONFIG_PASSWORD=adminpw
depends_on:
- couchdb2
compose-test-net.yaml修改以及添加如下内容
volumes:
orderer.example.com:
peer0.org1.example.com:
peer0.org2.example.com:
peer0.org3.example.com:
peer0.org3.example.com:
container_name: peer0.org3.example.com
image: hyperledger/fabric-peer:latest
labels:
service: hyperledger-fabric
environment:
- FABRIC_CFG_PATH=/etc/hyperledger/peercfg
- FABRIC_LOGGING_SPEC=INFO
#- FABRIC_LOGGING_SPEC=DEBUG
- CORE_PEER_TLS_ENABLED=true
- CORE_PEER_PROFILE_ENABLED=false
- CORE_PEER_TLS_CERT_FILE=/etc/hyperledger/fabric/tls/server.crt
- CORE_PEER_TLS_KEY_FILE=/etc/hyperledger/fabric/tls/server.key
- CORE_PEER_TLS_ROOTCERT_FILE=/etc/hyperledger/fabric/tls/ca.crt
# Peer specific variables
- CORE_PEER_ID=peer0.org3.example.com
- CORE_PEER_ADDRESS=peer0.org3.example.com:11051
- CORE_PEER_LISTENADDRESS=0.0.0.0:11051
- CORE_PEER_CHAINCODEADDRESS=peer0.org3.example.com:11052
- CORE_PEER_CHAINCODELISTENADDRESS=0.0.0.0:11052
- CORE_PEER_GOSSIP_EXTERNALENDPOINT=peer0.org3.example.com:11051
- CORE_PEER_GOSSIP_BOOTSTRAP=peer0.org3.example.com:11051
- CORE_PEER_LOCALMSPID=Org3MSP
- CORE_PEER_MSPCONFIGPATH=/etc/hyperledger/fabric/msp
- CORE_OPERATIONS_LISTENADDRESS=peer0.org3.example.com:9446
- CORE_METRICS_PROVIDER=prometheus
- CHAINCODE_AS_A_SERVICE_BUILDER_CONFIG={"peername":"peer0org3"}
- CORE_CHAINCODE_EXECUTETIMEOUT=300s
volumes:
- ../organizations/peerOrganizations/org3.example.com/peers/peer0.org3.example.com:/etc/hyperledger/fabric
- peer0.org3.example.com:/var/hyperledger/production
working_dir: /root
command: peer node start
ports:
- 11051:11051
- 9446:9446
networks:
- test
测试
启动测试网络
sudo ./network.sh up
创建通道
sudo ./network.sh createChannel
安装链码
sudo chmod -R 777 ../test-network
./network.sh deployCC -ccn basic -ccp ../asset-transfer-basic/chaincode-go -ccl go
之后按照我这篇博客:小白也能读懂的Fabric测试网络运行以及链码部署进行测试.
可以看到完整结果如下:
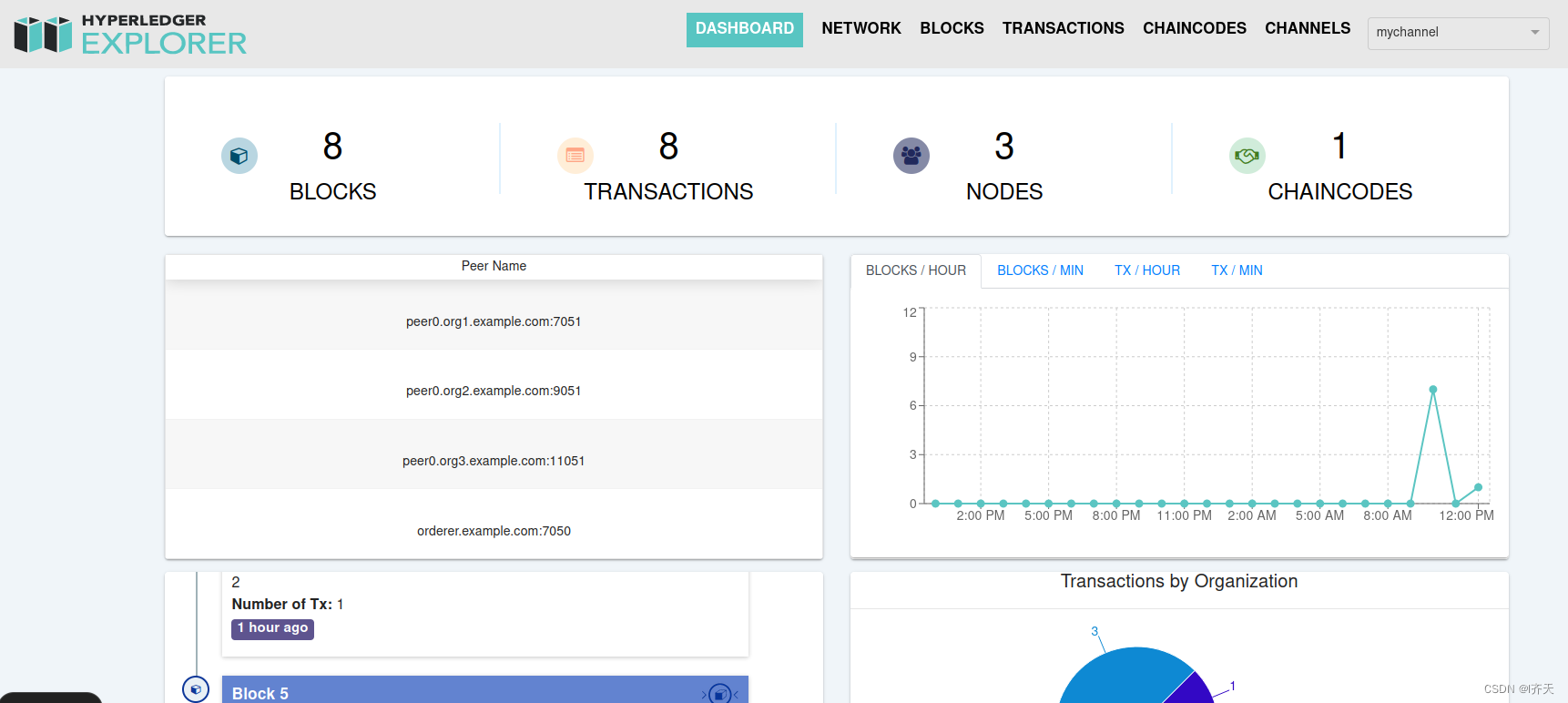
链码部署文件修改
/script 中的deployCC.sh修改的地方比较零散,用下面的内容进行覆盖:
#!/bin/bash
source scripts/utils.sh
CHANNEL_NAME=${1:-"mychannel"}
CC_NAME=${2}
CC_SRC_PATH=${3}
CC_SRC_LANGUAGE=${4}
CC_VERSION=${5:-"1.0"}
CC_SEQUENCE=${6:-"1"}
CC_INIT_FCN=${7:-"NA"}
CC_END_POLICY=${8:-"NA"}
CC_COLL_CONFIG=${9:-"NA"}
DELAY=${10:-"3"}
MAX_RETRY=${11:-"5"}
VERBOSE=${12:-"false"}
println "executing with the following"
println "- CHANNEL_NAME: ${C_GREEN}${CHANNEL_NAME}${C_RESET}"
println "- CC_NAME: ${C_GREEN}${CC_NAME}${C_RESET}"
println "- CC_SRC_PATH: ${C_GREEN}${CC_SRC_PATH}${C_RESET}"
println "- CC_SRC_LANGUAGE: ${C_GREEN}${CC_SRC_LANGUAGE}${C_RESET}"
println "- CC_VERSION: ${C_GREEN}${CC_VERSION}${C_RESET}"
println "- CC_SEQUENCE: ${C_GREEN}${CC_SEQUENCE}${C_RESET}"
println "- CC_END_POLICY: ${C_GREEN}${CC_END_POLICY}${C_RESET}"
println "- CC_COLL_CONFIG: ${C_GREEN}${CC_COLL_CONFIG}${C_RESET}"
println "- CC_INIT_FCN: ${C_GREEN}${CC_INIT_FCN}${C_RESET}"
println "- DELAY: ${C_GREEN}${DELAY}${C_RESET}"
println "- MAX_RETRY: ${C_GREEN}${MAX_RETRY}${C_RESET}"
println "- VERBOSE: ${C_GREEN}${VERBOSE}${C_RESET}"
FABRIC_CFG_PATH=$PWD/../config/
#User has not provided a name
if [ -z "$CC_NAME" ] || [ "$CC_NAME" = "NA" ]; then
fatalln "No chaincode name was provided. Valid call example: ./network.sh deployCC -ccn basic -ccp ../asset-transfer-basic/chaincode-go -ccl go"
# User has not provided a path
elif [ -z "$CC_SRC_PATH" ] || [ "$CC_SRC_PATH" = "NA" ]; then
fatalln "No chaincode path was provided. Valid call example: ./network.sh deployCC -ccn basic -ccp ../asset-transfer-basic/chaincode-go -ccl go"
# User has not provided a language
elif [ -z "$CC_SRC_LANGUAGE" ] || [ "$CC_SRC_LANGUAGE" = "NA" ]; then
fatalln "No chaincode language was provided. Valid call example: ./network.sh deployCC -ccn basic -ccp ../asset-transfer-basic/chaincode-go -ccl go"
## Make sure that the path to the chaincode exists
elif [ ! -d "$CC_SRC_PATH" ] && [ ! -f "$CC_SRC_PATH" ]; then
fatalln "Path to chaincode does not exist. Please provide different path."
fi
CC_SRC_LANGUAGE=$(echo "$CC_SRC_LANGUAGE" | tr [:upper:] [:lower:])
# do some language specific preparation to the chaincode before packaging
if [ "$CC_SRC_LANGUAGE" = "go" ]; then
CC_RUNTIME_LANGUAGE=golang
infoln "Vendoring Go dependencies at $CC_SRC_PATH"
pushd $CC_SRC_PATH
GO111MODULE=on go mod vendor
popd
successln "Finished vendoring Go dependencies"
elif [ "$CC_SRC_LANGUAGE" = "java" ]; then
CC_RUNTIME_LANGUAGE=java
rm -rf $CC_SRC_PATH/build/install/
infoln "Compiling Java code..."
pushd $CC_SRC_PATH
./gradlew installDist
popd
successln "Finished compiling Java code"
CC_SRC_PATH=$CC_SRC_PATH/build/install/$CC_NAME
elif [ "$CC_SRC_LANGUAGE" = "javascript" ]; then
CC_RUNTIME_LANGUAGE=node
elif [ "$CC_SRC_LANGUAGE" = "typescript" ]; then
CC_RUNTIME_LANGUAGE=node
infoln "Compiling TypeScript code into JavaScript..."
pushd $CC_SRC_PATH
npm install
npm run build
popd
successln "Finished compiling TypeScript code into JavaScript"
else
fatalln "The chaincode language ${CC_SRC_LANGUAGE} is not supported by this script. Supported chaincode languages are: go, java, javascript, and typescript"
exit 1
fi
INIT_REQUIRED="--init-required"
# check if the init fcn should be called
if [ "$CC_INIT_FCN" = "NA" ]; then
INIT_REQUIRED=""
fi
if [ "$CC_END_POLICY" = "NA" ]; then
CC_END_POLICY=""
else
CC_END_POLICY="--signature-policy $CC_END_POLICY"
fi
if [ "$CC_COLL_CONFIG" = "NA" ]; then
CC_COLL_CONFIG=""
else
CC_COLL_CONFIG="--collections-config $CC_COLL_CONFIG"
fi
# import utils
. scripts/envVar.sh
. scripts/ccutils.sh
packageChaincode() {
set -x
peer lifecycle chaincode package ${CC_NAME}.tar.gz --path ${CC_SRC_PATH} --lang ${CC_RUNTIME_LANGUAGE} --label ${CC_NAME}_${CC_VERSION} >&log.txt
res=$?
PACKAGE_ID=$(peer lifecycle chaincode calculatepackageid ${CC_NAME}.tar.gz)
{ set +x; } 2>/dev/null
cat log.txt
verifyResult $res "Chaincode packaging has failed"
successln "Chaincode is packaged"
}
function checkPrereqs() {
jq --version > /dev/null 2>&1
if [[ $? -ne 0 ]]; then
errorln "jq command not found..."
errorln
errorln "Follow the instructions in the Fabric docs to install the prereqs"
errorln "https://hyperledger-fabric.readthedocs.io/en/latest/prereqs.html"
exit 1
fi
}
#check for prerequisites
checkPrereqs
## package the chaincode
packageChaincode
## Install chaincode on peer0.org1 and peer0.org2
infoln "Installing chaincode on peer0.org1..."
installChaincode 1
infoln "Install chaincode on peer0.org2..."
installChaincode 2
infoln "Install chaincode on peer0.org3..."
installChaincode 3
## query whether the chaincode is installed
queryInstalled 1
## approve the definition for org1
approveForMyOrg 1
## check whether the chaincode definition is ready to be committed
## expect org1 to have approved and org2 not to
checkCommitReadiness 1 "\"Org1MSP\": true" "\"Org2MSP\": false" "\"Org3MSP\": false"
checkCommitReadiness 2 "\"Org1MSP\": true" "\"Org2MSP\": false" "\"Org3MSP\": false"
checkCommitReadiness 3 "\"Org1MSP\": true" "\"Org2MSP\": false" "\"Org3MSP\": false"
## now approve also for org2
approveForMyOrg 2
## check whether the chaincode definition is ready to be committed
## expect them both to have approved
checkCommitReadiness 1 "\"Org1MSP\": true" "\"Org2MSP\": true" "\"Org3MSP\": false"
checkCommitReadiness 2 "\"Org1MSP\": true" "\"Org2MSP\": true" "\"Org3MSP\": false"
checkCommitReadiness 3 "\"Org1MSP\": true" "\"Org2MSP\": true" "\"Org3MSP\": false"
## now approve also for org2
approveForMyOrg 3
checkCommitReadiness 3 "\"Org1MSP\": true" "\"Org2MSP\": true" "\"Org3MSP\": false"
## now that we know for sure both orgs have approved, commit the definition
commitChaincodeDefinition 1 2 3
## query on both orgs to see that the definition committed successfully
queryCommitted 1
queryCommitted 2
queryCommitted 3
## Invoke the chaincode - this does require that the chaincode have the 'initLedger'
## method defined
if [ "$CC_INIT_FCN" = "NA" ]; then
infoln "Chaincode initialization is not required"
else
chaincodeInvokeInit 1 2 3
fi
exit 0
运行
修改上述文件之后再重新启动网络,查看输出结果,可以看到3个组织都同意了.
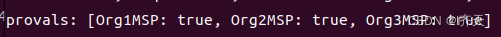
初始化4个节点,添加addorg5
根据之前的内容定义第四个组织
此处不在赘述
添加org5
之后的博客再写.
