基于helm的方式在k8s集群中部署gitlab - 部署(一)
文章目录
- 1. 背景说明
- 2. 你可以学到什么?
- 3. 前置条件
- 4. 安装docker服务(所有节点)
- 5. 部署k8s集群
- 5.1 系统配置(所有节点)
- 5.2 安装kubelet组件(所有节点)
- 5.2.1 编写kubelet源
- 5.2.2 安装kubelet
- 5.2.3 启动kubelet
- 5.3 集群初始化(master节点)
- 5.4 从节点加入到集群中
- 5.5 安装k8s网络插件
- 5.6 安装ingress网络
- 5.7 配置StorageClass
- 6. helm安装gitlab
- 6.1 添加gitlab的helm源
- 6.2 创建证书密钥
- 6.3 创建集成smtp和ldap的密钥
- 6.4 拉取并修改gitlab的values文件
- 6.5 部署gilab
- 6.6 修改gitlab-nginx-ingress
- 方法1: 修改gitlab-nginx-ingress的暴露type(upgrade后会失效)
- 方法2: 修改gitlab的values文件
- 6.7 修改gitlab-shell的端口
- 7. 部署runner
- 7.1 部署nginx代理
- 7.2 配置runner
- 7.3 更新gitlab
- 7.4 测试runner
- 8. minio功能验证
- 9. ldap功能验证
1. 背景说明
客户之前的gitlab服务在k8s集群中部署的,为了整合现有的硬件资源,计划将gitlab服务迁移到虚拟机上。
先在测试环境进行如下模拟操作:
- 基于kubeadm部署一套k8s集群,在集群上部署gitlab服务;
- 将数据备份到对象存储中;
- 最终将数据恢复在另外一台gitlab单实例上,实现gitlab在k8s和单实例ominibus之前迁移的一个完整闭环。
2. 你可以学到什么?
- k8s集群部署
- K8s 暴露服务的类型
- K8s storageclass、configmap、secret
- helm部署gitlab(配置smtp、ldap、runner)
- gitlab配置对象存储
3. 前置条件
- helm 安装
- K8s 集群版本 1.23 (两台 8C16G OS为7.9)
- Docker 版本 20.10.23
- 证书在阿里云上申请免费ssl证书即可或者通过let’s encry 申请免费的泛域名证书
4. 安装docker服务(所有节点)
参考 docker安装(二进制&yum)
5. 部署k8s集群
参考k8s1.15安装详细精华版
也可以通过如下命令快捷安装
5.1 系统配置(所有节点)
修改内核参数 - /etc/sysctl.conf
# 转发
net.ipv4.ip_forward = 1
# iptables网络
net.bridge.bridge-nf-call-ip6tables = 1
net.bridge.bridge-nf-call-iptables = 1
#加在生效
sysctl -p
5.2 安装kubelet组件(所有节点)
5.2.1 编写kubelet源
编辑/etc/yum.repos.d/kubernetes.repo
[kubernetes]
name=Kubernetes
baseurl=https://mirrors.aliyun.com/kubernetes/yum/repos/kubernetes-el7-x86_64
enabled=1
gpgcheck=0
repo_gpgcheck=0
gpgkey=https://mirrors.aliyun.com/kubernetes/yum/doc/yum-key.gpg https://mirrors.aliyun.com/kubernetes/yum/doc/rpm-package-key.gpg
yum repolist
5.2.2 安装kubelet
yum install -y kubelet-1.23.0 kubeadm-1.23.0 kubectl-1.23.0
5.2.3 启动kubelet
# 启动
systemctl start kubelet.service
# 开启自启
systemctl enable kubelet.service
5.3 集群初始化(master节点)
主节点上执行如下命令
# 命令解析
kubeadm init \
--apiserver-advertise-address=10.100.0.14 \ # 通常为主节点的ip地址
--image-repository registry.aliyuncs.com/google_containers \ # 指定基础镜像拉取的仓库
--kubernetes-version v1.23.0 \ # 指定k8s的组件版本
--service-cidr=10.92.0.0/12 \ # k8s集群svc的子网
--pod-network-cidr=10.220.0.0/16 \ # k8s集群pod的子网
--ignore-preflight-errors=all # 忽略运行时的错误
# 一条初始化命令如下:
kubeadm init --apiserver-advertise-address=10.100.0.14 --image-repository registry.aliyuncs.com/google_containers --kubernetes-version v1.23.0 --service-cidr=10.92.0.0/12 --pod-network-cidr=10.220.0.0/16 --ignore-preflight-errors=all
5.4 从节点加入到集群中
从节点上执行如下命令
kubeadm join 10.100.0.14:6443 \
--token saleos.q26gm2rbtgrwvdla \
--discovery-token-ca-cert-hash sha256:5058ac78bd8f7879e14bae262d359b2b499d55a2d54796e3d103a27208f06d93
5.5 安装k8s网络插件
# 参考 https://github.com/flannel-io/flannel#deploying-flannel-with-kubectl
kubectl apply -f https://github.com/flannel-io/flannel/releases/latest/download/kube-flannel.yml
5.6 安装ingress网络
# 参考 https://github.com/kubernetes/ingress-nginx/tree/controller-v1.1.1#support-versions-table
# 参考 https://github.com/kubernetes/ingress-nginx/blob/controller-v1.1.1/deploy/static/provider/cloud/deploy.yaml
# 下载
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.1.1/deploy/static/provider/cloud/deploy.yaml
# 如果有问题 可以下一下crd的网络和你的svc的crd一样即可,将LoadBalancer改成NodePort
5.7 配置StorageClass
参考 安装并配置StorageClass
6. helm安装gitlab
6.1 添加gitlab的helm源
# 添加helm源
helm repo add gitlab-jh https://charts.gitlab.cn
# 更新helm源
helm repo update
6.2 创建证书密钥
# 创建gitlab服务运行的命名空间
kubectl create ns jihulab
# 创建证书sa(将证书上传到主节点机器上的某个目录下,然后切换到该目录即可)
kubectl create secret tls gitlab-jihulab-cn-ssl --cert=kube.bdeet.top.pem --key=kube.bdeet.top.key -n jihulab
kubectl create secret tls registry-jihulab-cn-ssl --cert=registry.bdeet.top.pem --key=registry.bdeet.top.key -n jihulab
kubectl create secret tls minio-jihulab-cn-ssl --cert=minio.bdeet.top.pem --key=minio.bdeet.top.key -n jihulab
6.3 创建集成smtp和ldap的密钥
kubectl create secret generic ldap-admin --from-literal=password='Jh@2022' -n jihulab
kubectl create secret generic smtp-gitlab --from-literal=password='wqfhqohixshrnnnh' -n jihulab
6.4 拉取并修改gitlab的values文件
拉取gitlab 15.8.0的charts,编辑values文件
...
...
## 域名配置
hosts:
domain: bdeet.top
hostSuffix:
externalIP:
ssh:
gitlab:
name: kube.bdeet.top
https: true
minio:
name: minio.bdeet.top
https: true
registry:
name: registry.bdeet.top
https: true
...
...
## ldap集成
ldap:
preventSignin: false
servers:
main:
label: 'LDAP'
host: '129.226.208.223'
port: 389
uid: 'uid'
bind_dn: 'cn=ldap,dc=wkx,dc=cn'
base: 'dc=wkx,dc=cn'
password:
secret: ldap-admin
key: password
encryption: 'plain'
...
...
## 配置邮箱
smtp:
enabled: true
address: smtp.gmail.com
port: 587
user_name: "kxw12108@gmail.com"
## https://docs.gitlab.com/charts/installation/secrets#smtp-password
password:
secret: "smtp-gitlab"
key: password
# domain:
authentication: "login"
starttls_auto: true
openssl_verify_mode: "peer"
pool: false
## https://docs.gitlab.com/charts/charts/globals#outgoing-email
## Email persona used in email sent by GitLab
email:
from: "kxw12108@gmail.com"
display_name: "GitLab Administrator"
reply_to: "kxw12108@gmail.com"
subject_suffix: "GitLab"
smime:
enabled: false
secretName: ""
keyName: "tls.key"
certName: "tls.crt"
...
...
6.5 部署gilab
# 创建gitlab运行的命名空间
kubectl create ns jihulab
# 安装gitlab
helm install gitlab gitlab-jh/gitlab \
--version 6.8.0 \
--timeout 600s \
--set certmanager.install=false \
--set global.ingress.configureCertmanager=false \
--set global.ingress.tls.enabled=true \
--set gitlab.webservice.ingress.tls.secretName=gitlab-jihulab-cn-ssl \
--set registry.ingress.tls.secretName=registry-jihulab-cn-ssl \
--set minio.ingress.tls.secretName=minio-jihulab-cn-ssl \
--values values.yaml -n jihulab
6.6 修改gitlab-nginx-ingress
方法1: 修改gitlab-nginx-ingress的暴露type(upgrade后会失效)
kubectl edit svc -n jihulab gitlab-nginx-ingress-controller
# 将type: LoadBalancer 改成 type: NodePort,保存退出后,会看到gitlab-shell
方法2: 修改gitlab的values文件
...
...
nginx-ingress:
enabled: true
...
...
service:
externalTrafficPolicy: "Local"
type: "NodePort" # 添加ingress的svc的type
...
...
问题说明
由于我们的自建k8s集群 gitlab的ingress的svc没有使用LoadBalancer而是NodePort,因为之前将minio、registry、gitlab的域名解析到该节点上后肯定是无法访问的,还必须需要在域名后添加nodeport的端口才可以。
kube.bdeet.top ---> kube.bdeet.top:nodeport
registry.bdeet.top ---> registry.bdeet.top:nodeport
minio.bdeet.top ---> minio.bdeet.top:nodeport
6.7 修改gitlab-shell的端口
由于将gitlab-nginx-ingress-controller的暴露端口的方式修改成了NodePort,因为ssh的端口也需要调整(查看下gitlab-nginx-ingress-controller ssh的暴露端口),否则会无法克隆。修改gitlab-shell
...
...
global:
shell:
port: 31475
...
...
更新gitlab
# 更新
helm upgrade gitlab gitlab-jh/gitlab \
--version 6.8.0 \
--timeout 600s \
--set certmanager.install=false \
--set global.ingress.configureCertmanager=false \
--set global.ingress.tls.enabled=true \
--set gitlab.webservice.ingress.tls.secretName=gitlab-jihulab-cn-ssl \
--set registry.ingress.tls.secretName=registry-jihulab-cn-ssl \
--set minio.ingress.tls.secretName=minio-jihulab-cn-ssl \
--set nginx-ingress.service.type=NodePort \
--set global.shell.port=31475 \
--values values.yaml -n jihulab
7. 部署runner
这样的runner存在一个问题就是由于使用的是nodeport的暴露方式,因为runner中的gitlaburl需要加端口,同时在runner进行克隆的时候也需要加端口,因为在部署一个nginx,作为一个转发。
7.1 部署nginx代理
# 安装nginx
yum -y install nginx
# 配置nginx
# cat /etc/nginx/nginx.conf
...
...
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name kube.bdeet.top;
ssl_certificate "/root/cert/kube.bdeet.top.pem";
ssl_certificate_key "/root/cert/kube.bdeet.top.key";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass https://kube.bdeet.top:31501;
}
error_page 404 /404.html;
location = /40x.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
}
...
...
7.2 配置runner
修改values文件
...
...
runner:
registrationToken:
secret: gitlab-gitlab-runner-secret # gitlab-runner的secret
...
...
gitlab-runner:
install: true
gitlabUrl: https://kube.bdeet.top #修改gitlab的域名
rbac:
create: true
runners:
privileged: true #开启特权
locked: false
config: |
[[runners]]
[runners.kubernetes]
image = "ubuntu:18.04"
{{- if .Values.global.minio.enabled }}
[runners.cache]
Type = "s3"
Path = "gitlab-runner"
Shared = true
[runners.cache.s3]
#ServerAddress = {{ include "gitlab-runner.cache-tpl.s3ServerAddress" . }}
ServerAddress = "https://minio.bdeet.top:31501" #接入对象存储
BucketName = "runner-cache"
BucketLocation = "us-east-1"
Insecure = false
...
...
7.3 更新gitlab
Upgrade 更新gitlab
helm upgrade gitlab gitlab-jh/gitlab \
--version 6.8.0 \
--timeout 600s \
--set certmanager.install=false \
--set global.ingress.configureCertmanager=false \
--set global.ingress.tls.enabled=true \
--set gitlab.webservice.ingress.tls.secretName=gitlab-jihulab-cn-ssl \
--set registry.ingress.tls.secretName=registry-jihulab-cn-ssl \
--set minio.ingress.tls.secretName=minio-jihulab-cn-ssl \
--set nginx-ingress.service.type=NodePort \
--set global.shell.port=31475 \
--values values.yaml -n jihulab
7.4 测试runner
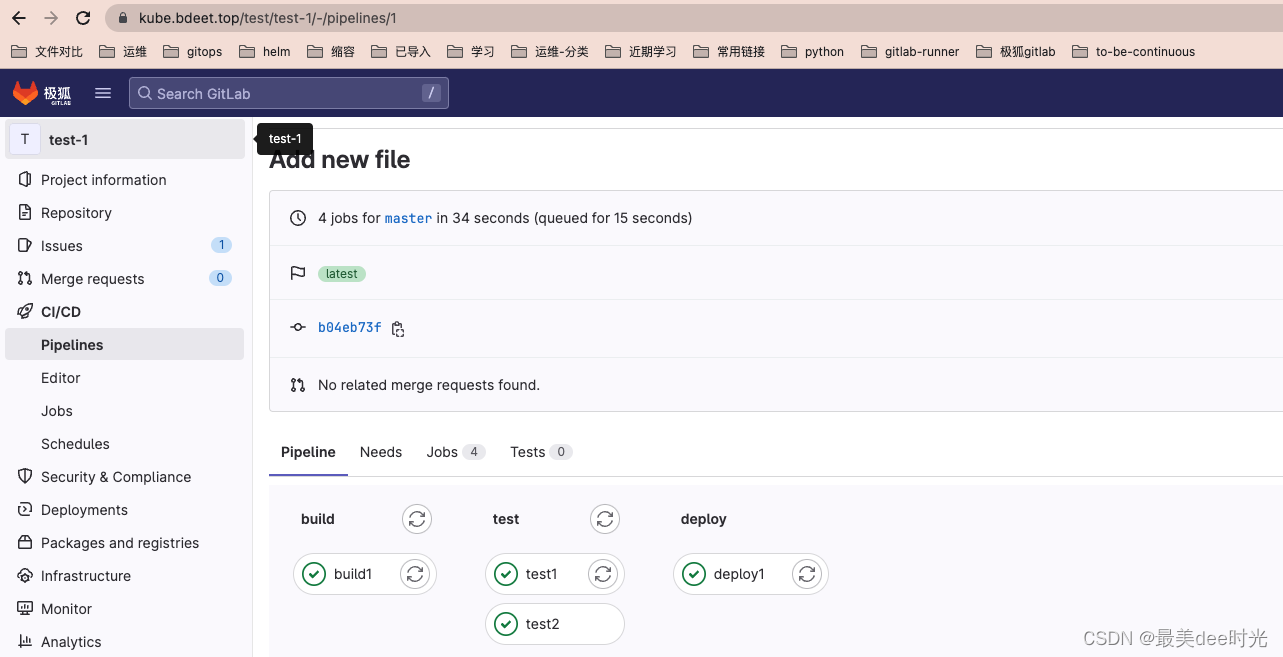
gitlab上创建一个pipeline项目,然后commit提交后触发。
.gitlab-ci.yml文件如下
image: busybox:latest
before_script:
- echo "Before script section"
- echo "For example you might run an update here or install a build dependency"
- echo "Or perhaps you might print out some debugging details"
after_script:
- echo "After script section"
- echo "For example you might do some cleanup here"
build1:
stage: build
script:
- echo "Do your build here"
test1:
stage: test
script:
- echo "Do a test here"
- echo "For example run a test suite"
- echo 1 > index.html
artifacts:
paths:
- index.html
test2:
stage: test
script:
- echo "Do another parallel test here"
- echo "For example run a lint test"
deploy1:
stage: deploy
script:
- echo "Do your deploy here"
environment: production
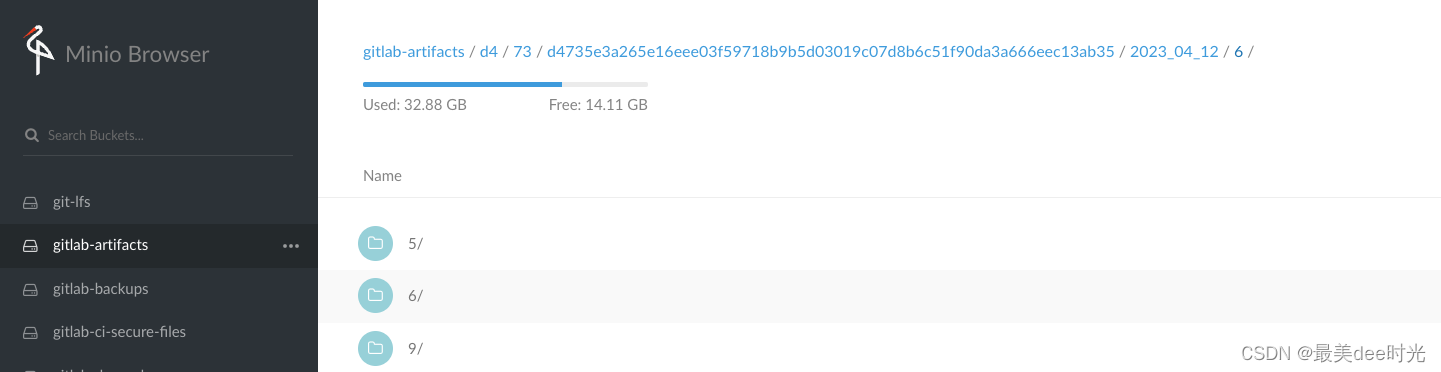
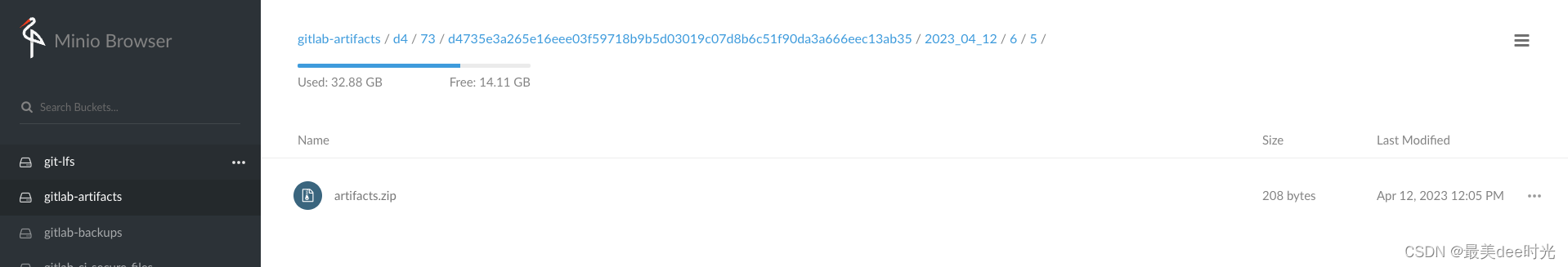
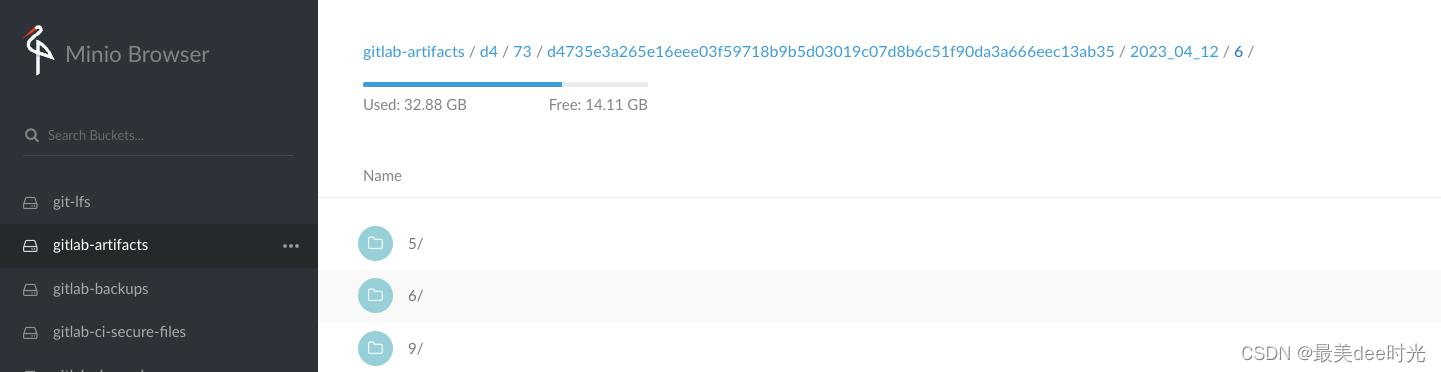
可以发现minio上有artifacts文件(5/6/9 分别是job的artifacts文件、meta元数据、日志)
 ## 8. 邮箱验证
## 8. 邮箱验证
可以验证项目创建、提交代码、pipeline测试、runner测试、minio测试
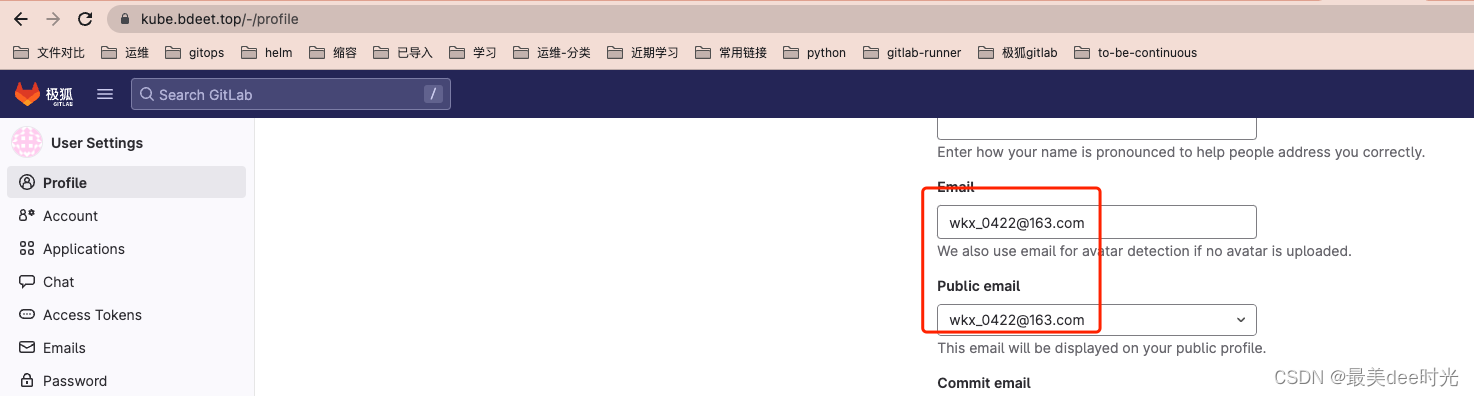
修改个人邮箱
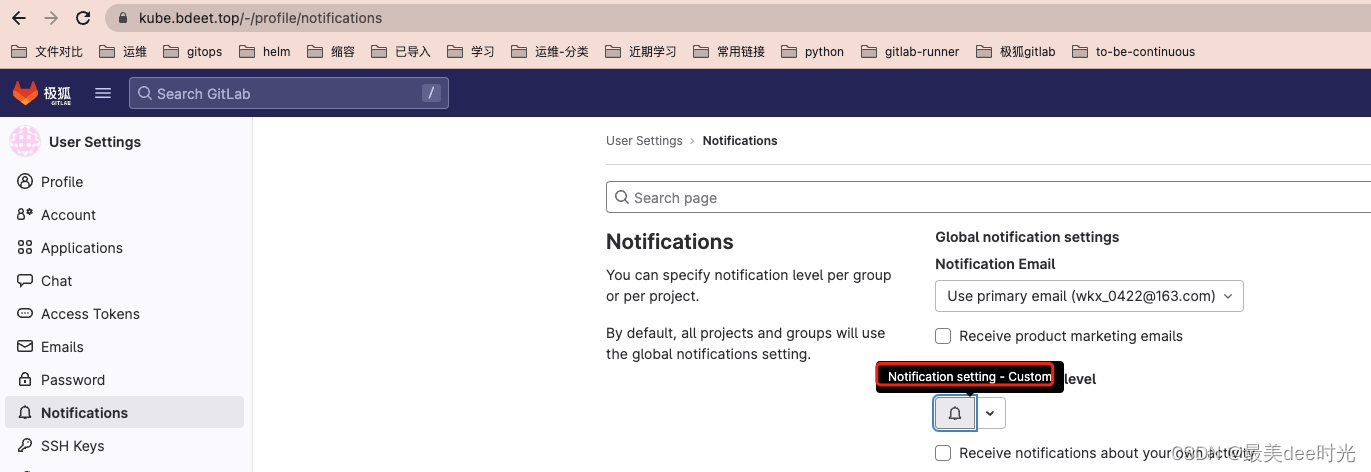
设置通知 - 自定义全部勾选
运行pipeline
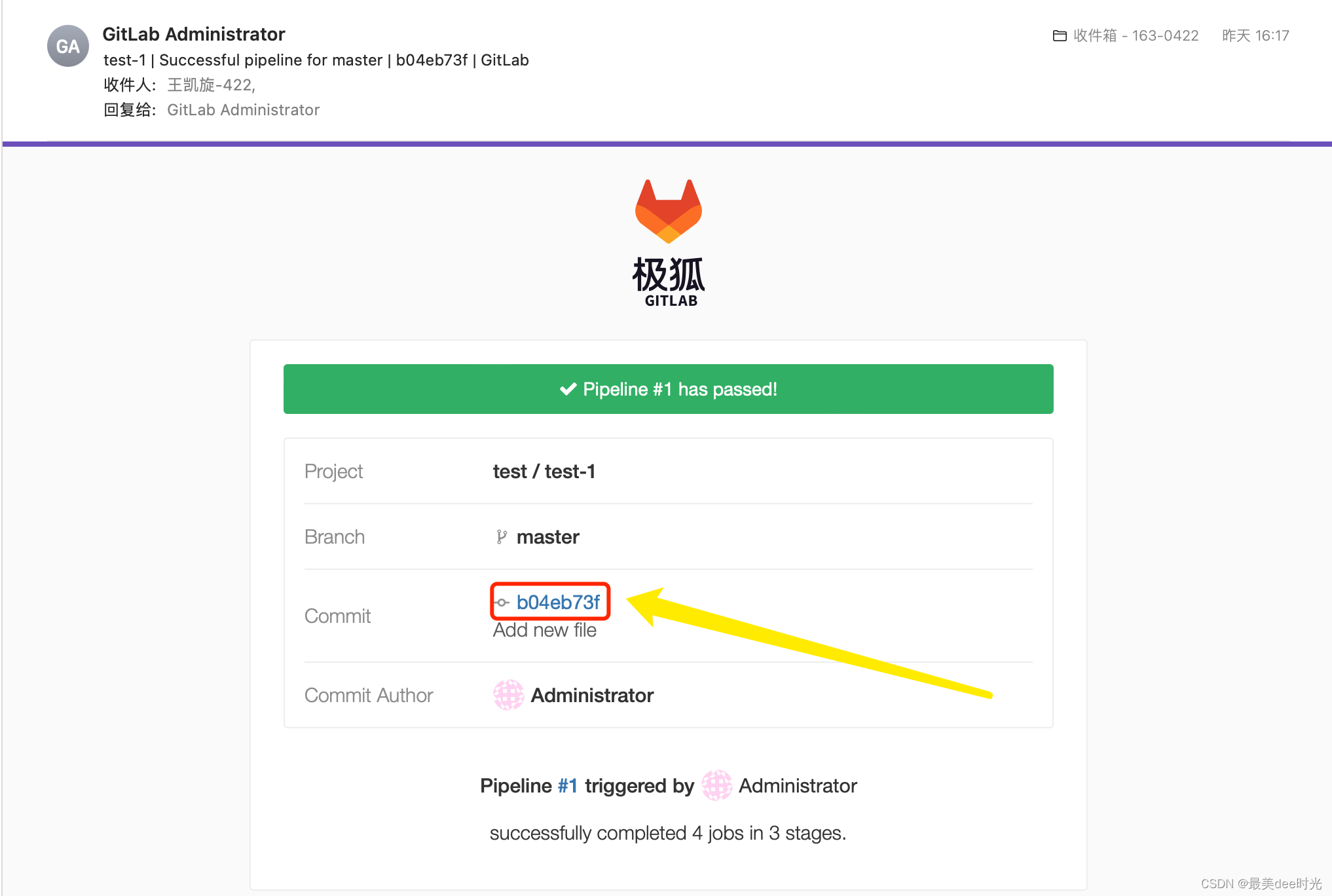
邮箱查看
8. minio功能验证
查看artifacts
9. ldap功能验证
查看用户属性