IOS - 某驾宝典篇
首先挂上代理抓个登陆包,结果发现抓不到包,我们直接换个思路,采用vpn转发方式进行抓包;
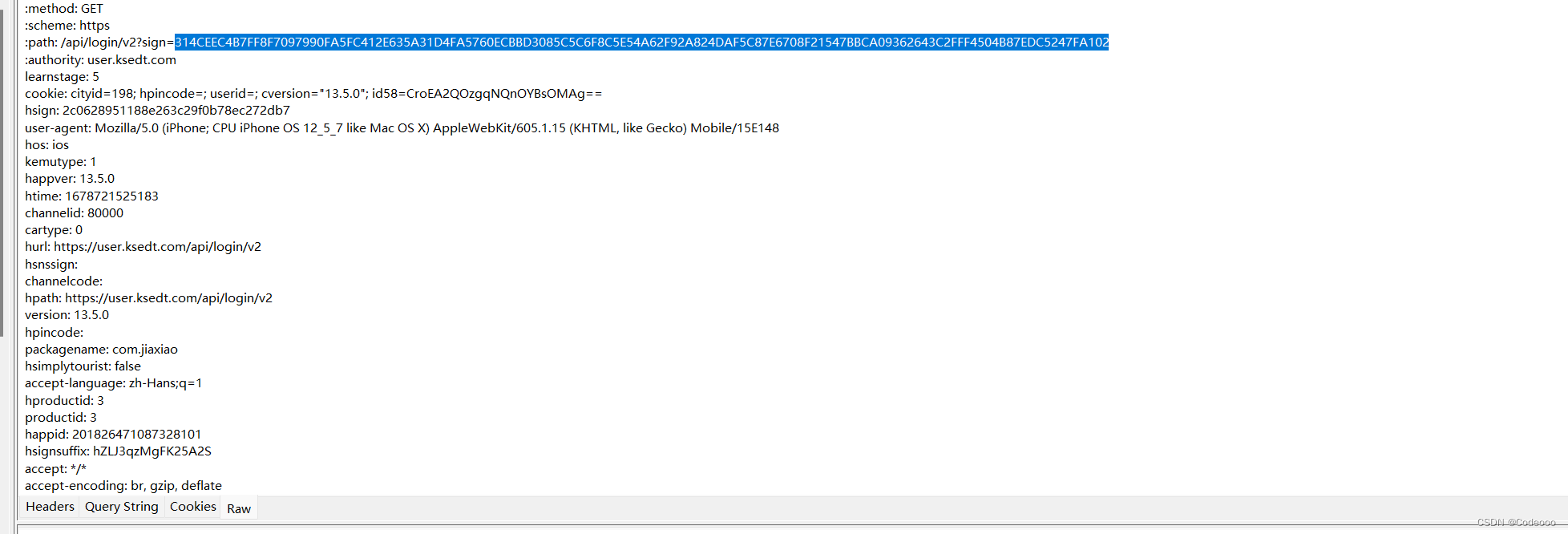
sign, hsign,hext-union 三个参数加密;
hsign长度为32,可能为MD5 , 其他两个未确定;
直接上我们的url定位:我直接附加吧
frida-trace -UF -m "+[NSURL URLWithString:]"
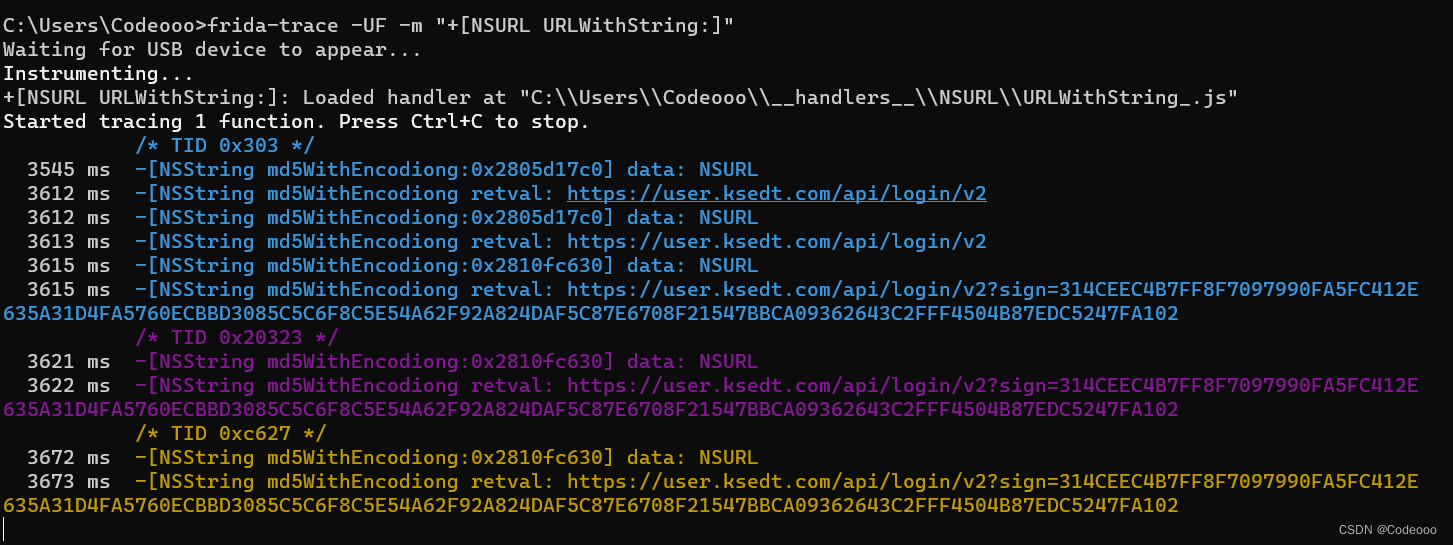
是搞出来点东西,看样子有这个MD5, 先个堆栈追踪;
打开提示目录中的,URLWithString_.js 文件
C:\Users\Codeooo\__handlers__
把咱们万能堆栈加上去;
log('堆栈 from:\n' +Thread.backtrace(this.context, Backtracer.ACCURATE).map(DebugSymbol.fromAddress).join('\n') + '\n');
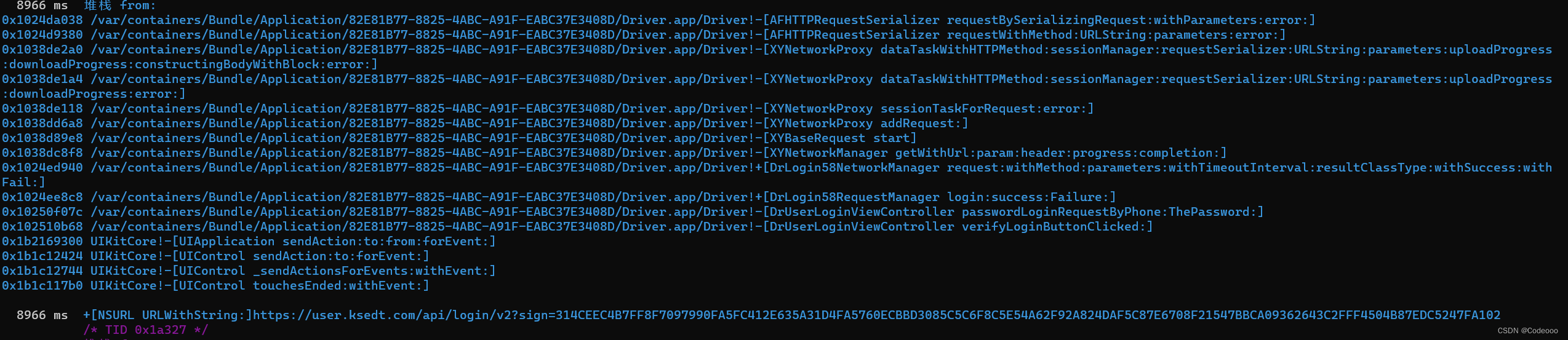
记录下堆栈,砸壳分析一波:
砸壳我这里用的是 CrackerXI ,https://blog.csdn.net/weixin_38927522/article/details/129497173
0x1024da038 /var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!-[AFHTTPRequestSerializer requestBySerializingRequest:withParameters:error:]
0x1024d9380 /var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!-[AFHTTPRequestSerializer requestWithMethod:URLString:parameters:error:]
0x1038de2a0 /var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!-[XYNetworkProxy dataTaskWithHTTPMethod:sessionManager:requestSerializer:URLString:parameters:uploadProgress:downloadProgress:constructingBodyWithBlock:error:]
0x1038de1a4 /var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!-[XYNetworkProxy dataTaskWithHTTPMethod:sessionManager:requestSerializer:URLString:parameters:uploadProgress:downloadProgress:error:]
0x1038de118 /var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!-[XYNetworkProxy sessionTaskForRequest:error:]
0x1038dd6a8 /var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!-[XYNetworkProxy addRequest:]
0x1038d89e8 /var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!-[XYBaseRequest start]
0x1038dc8f8 /var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!-[XYNetworkManager getWithUrl:param:header:progress:completion:]
0x1024ed940 /var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!+[DrLogin58NetworkManager request:withMethod:parameters:withTimeoutInterval:resultClassType:withSuccess:withFail:]
0x1024ee8c8 /var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!+[DrLogin58RequestManager login:success:Failure:]
0x10250f07c /var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!-[DrUserLoginViewController passwordLoginRequestByPhone:ThePassword:]
0x102510b68 /var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!-[DrUserLoginViewController verifyLoginButtonClicked:]
0x1b2169300 UIKitCore!-[UIApplication sendAction:to:from:forEvent:]
0x1b1c12424 UIKitCore!-[UIControl sendAction:to:forEvent:]
0x1b1c12744 UIKitCore!-[UIControl _sendActionsForEvents:withEvent:]
0x1b1c117b0 UIKitCore!-[UIControl touchesEnded:withEvent:]
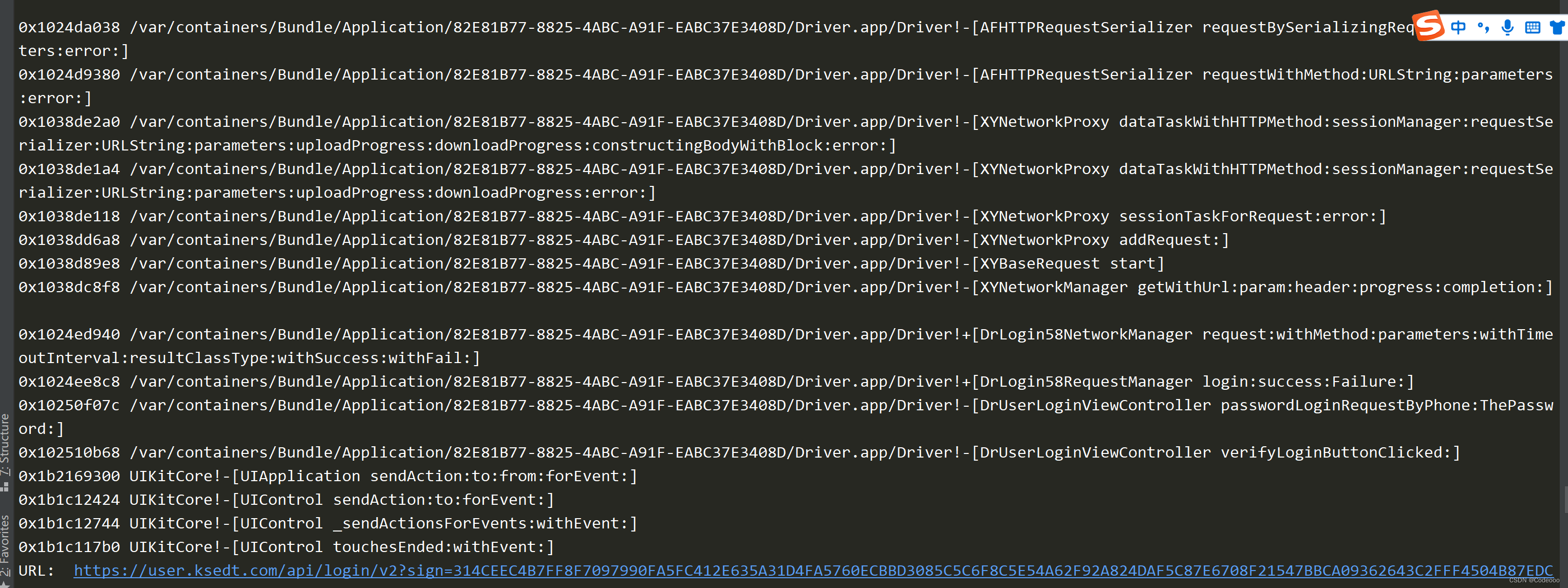
8966 ms +[NSURL URLWithString:]https://user.ksedt.com/api/login/v2?sign=314CEEC4B7FF8F7097990FA5FC412E635A31D4FA5760ECBBD3085C5C6F8C5E54A62F92A824DAF5C87E6708F21547BBCA09362643C2FFF4504B87EDC5247FA102
我们通过frida hook也是一样的:
var ClassName = "NSURL";
var MethodName = "+ URLWithString:";
var func = ObjC.classes[ClassName][MethodName];
Interceptor.attach(func.implementation, {
onEnter: function (args) {
console.log(Thread.backtrace(this.context, Backtracer.ACCURATE).map(DebugSymbol.fromAddress).join("\n"));
console.log("URL: ", ObjC.Object(args[2]), "\n");
}, onLeave: function (retval) {
}
});
hook第一个堆栈函数,看一下:
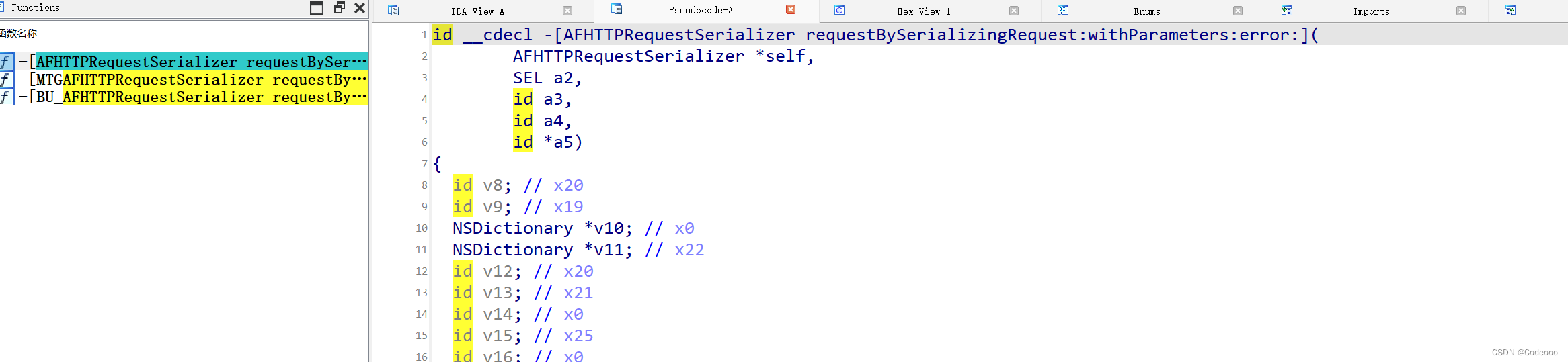
var requestBySerializingRequest = ObjC.classes.AFHTTPRequestSerializer['- requestBySerializingRequest:withParameters:error:'];
Interceptor.attach(requestBySerializingRequest.implementation, {
onEnter: function (args) {
console.log("args[2]: ", ObjC.Object(args[2]));
console.log("args[3]: ", ObjC.Object(args[3]));
console.log("args[4]: ", ObjC.Object(args[4]));
this.arg4 = args[4];
}, onLeave: function (retval) {
console.log("args[4]: ", ObjC.Object(this.arg4.readPointer()));
}
});
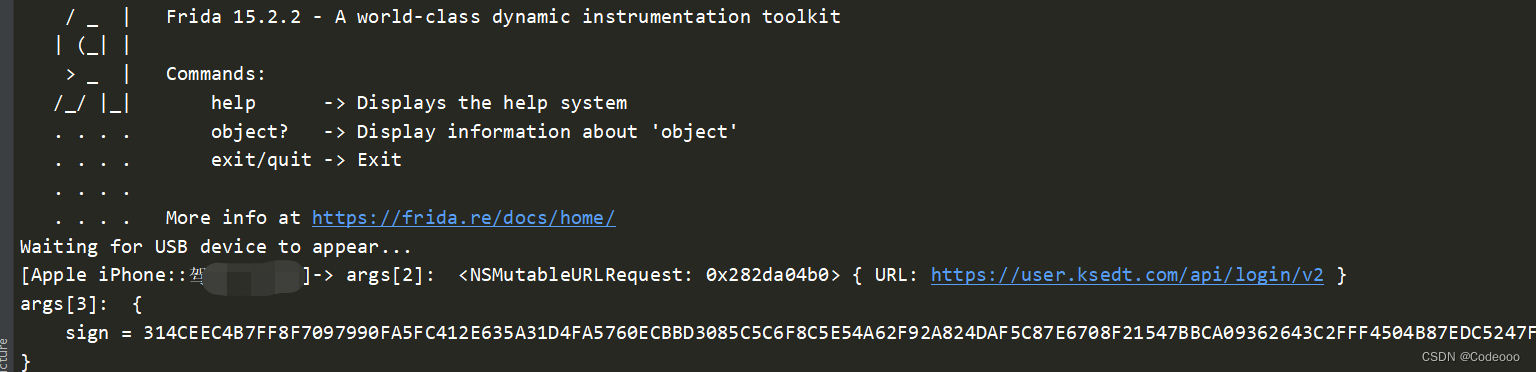
继续往上找吧;
找到这个堆栈:
// 0x1038dc8f8
/var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!-[XYNetworkManager
getWithUrl:param:header:progress:completion:]


var initWithMethod = ObjC.classes.XYHTTPRequest['+ initWithMethod:requestURL:requestParam:requestHeaderField:'];
Interceptor.attach(initWithMethod.implementation, {
onEnter: function (args) {
console.log('initWithMethod called from:\n' +
Thread.backtrace(this.context, Backtracer.ACCURATE)
.map(DebugSymbol.fromAddress).join('\n') + '\n');
//console.log("args[2]: ", (args[2]));
console.log("args[3]: ", ObjC.Object(args[3]));
console.log("args[4]: ", ObjC.Object(args[4]));
console.log("args[5]: ", ObjC.Object(args[5]));
}, onLeave: function (retval) {
}
});
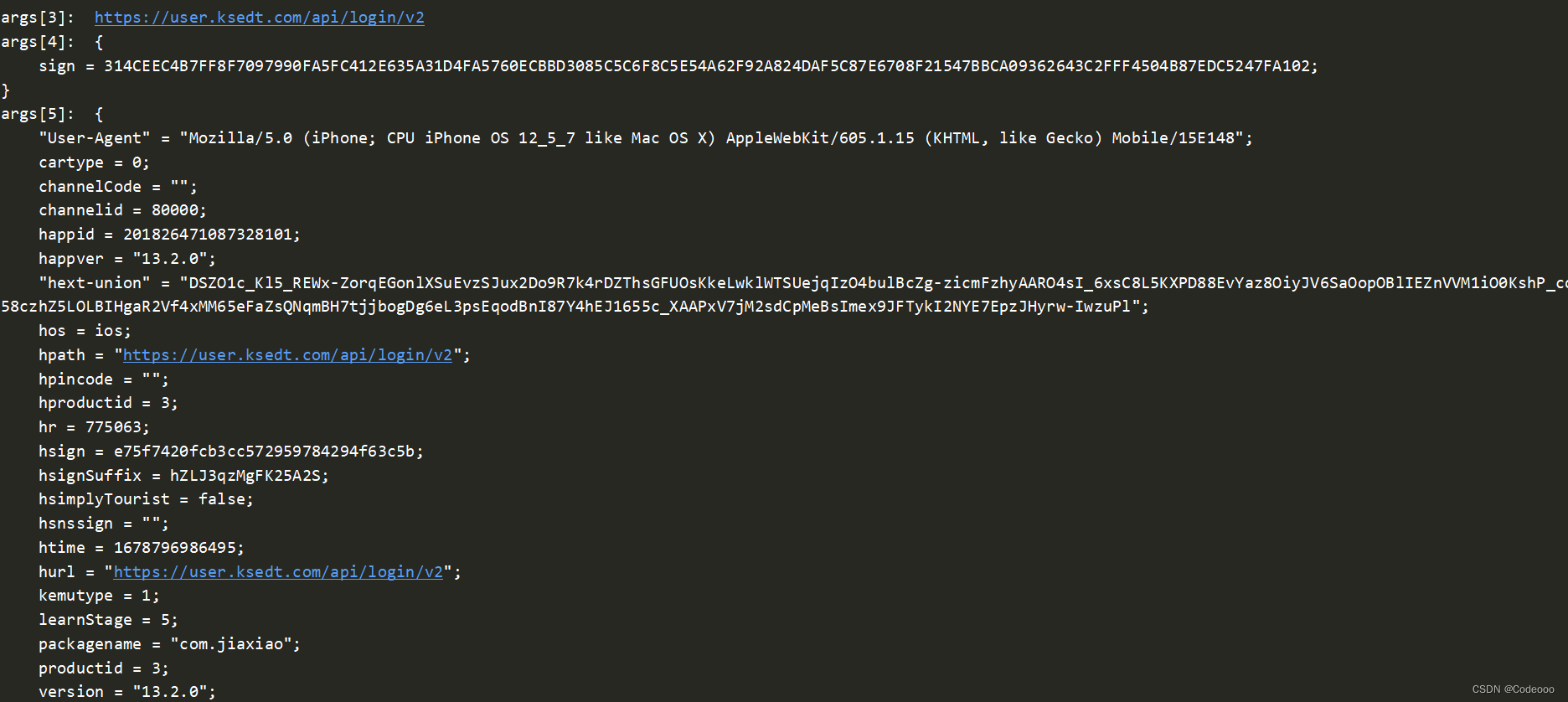
看来还是不对,再继续往上找:
找到: // 0x1024ed940
/var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!+[DrLogin58NetworkManager
request:withMethod:parameters:withTimeoutInterval:resultClassType:withSuccess:withFail:]

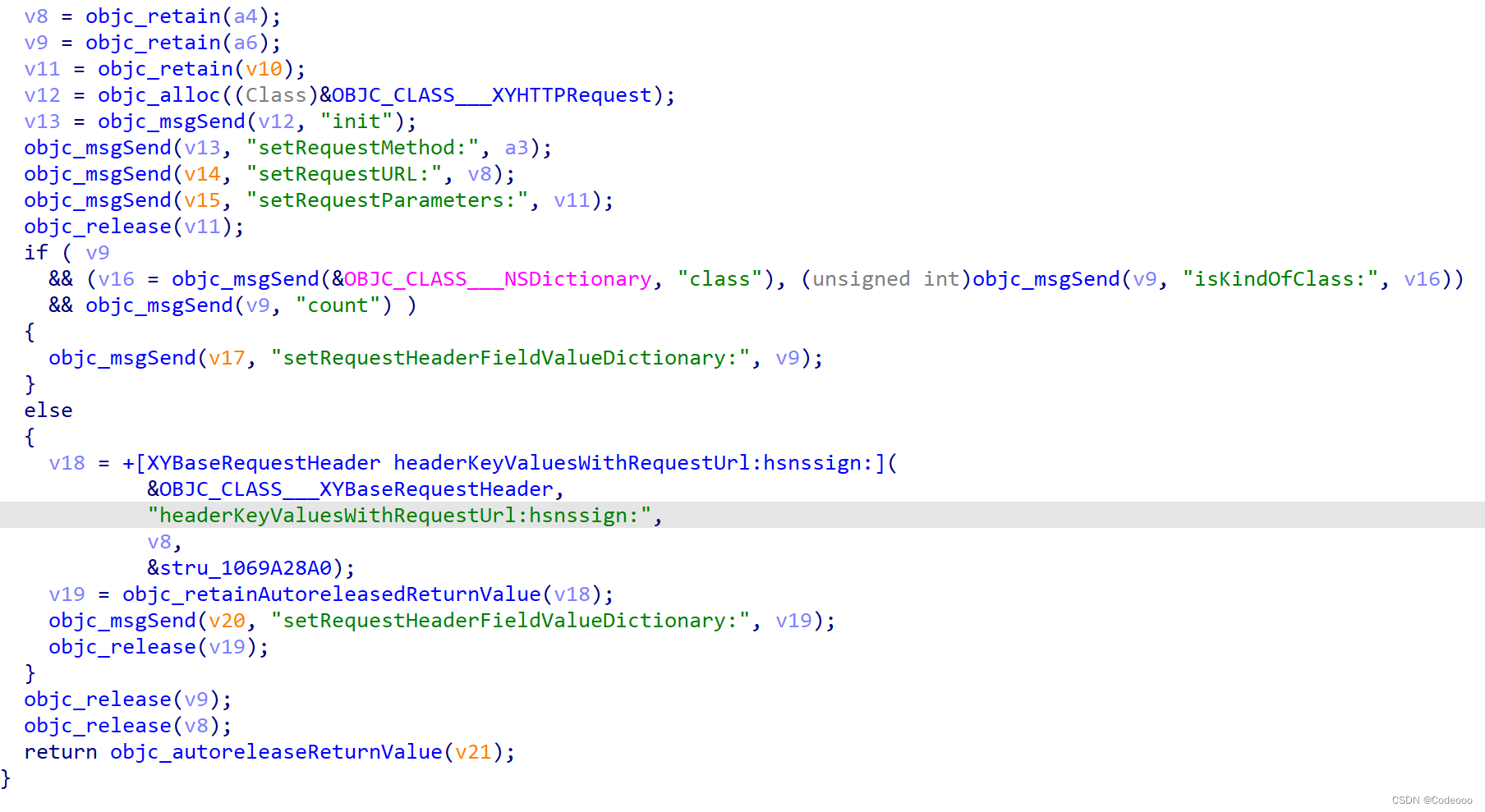
这里有个方法比较特殊 记录下:
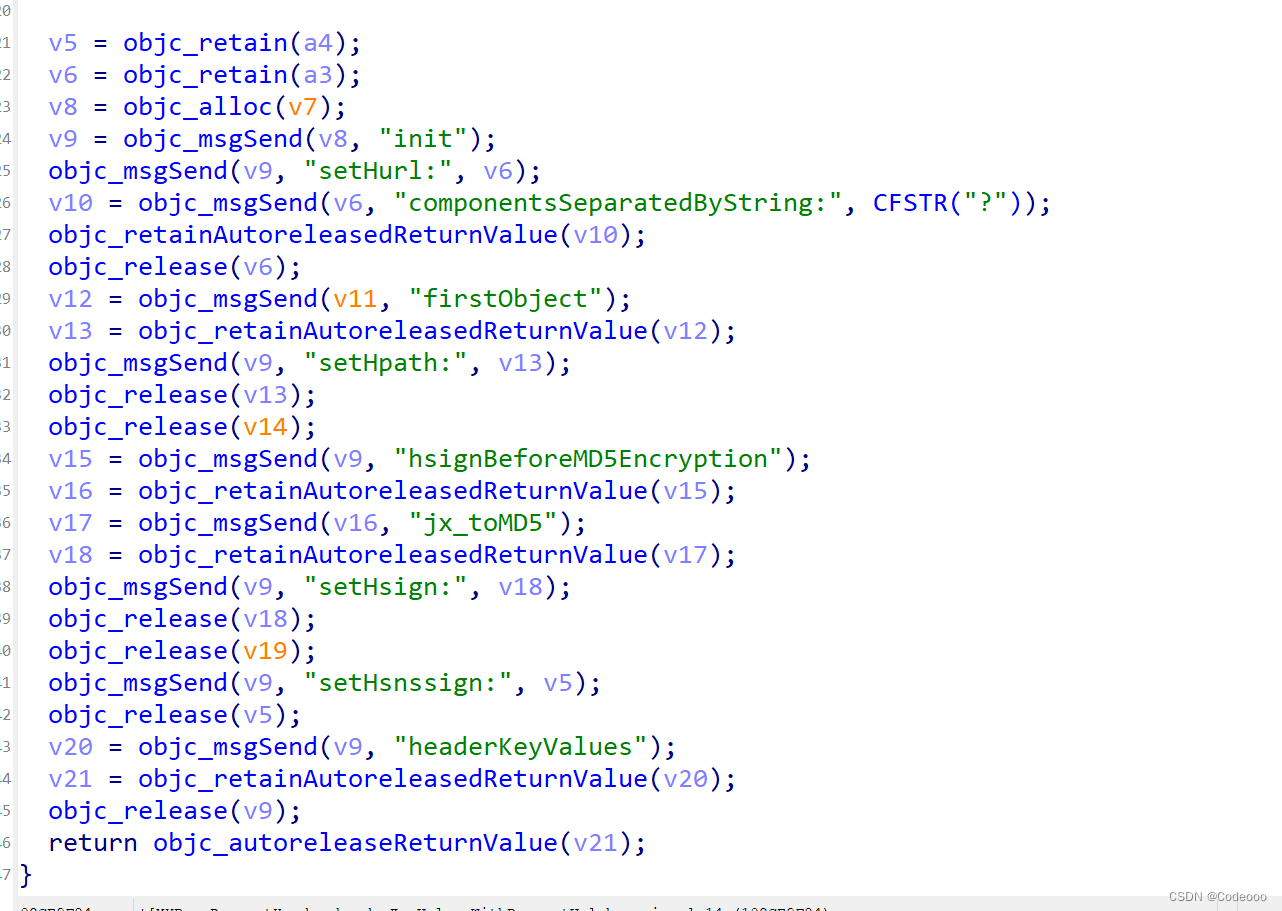
有个类似于MD5的调用,再点进去看看
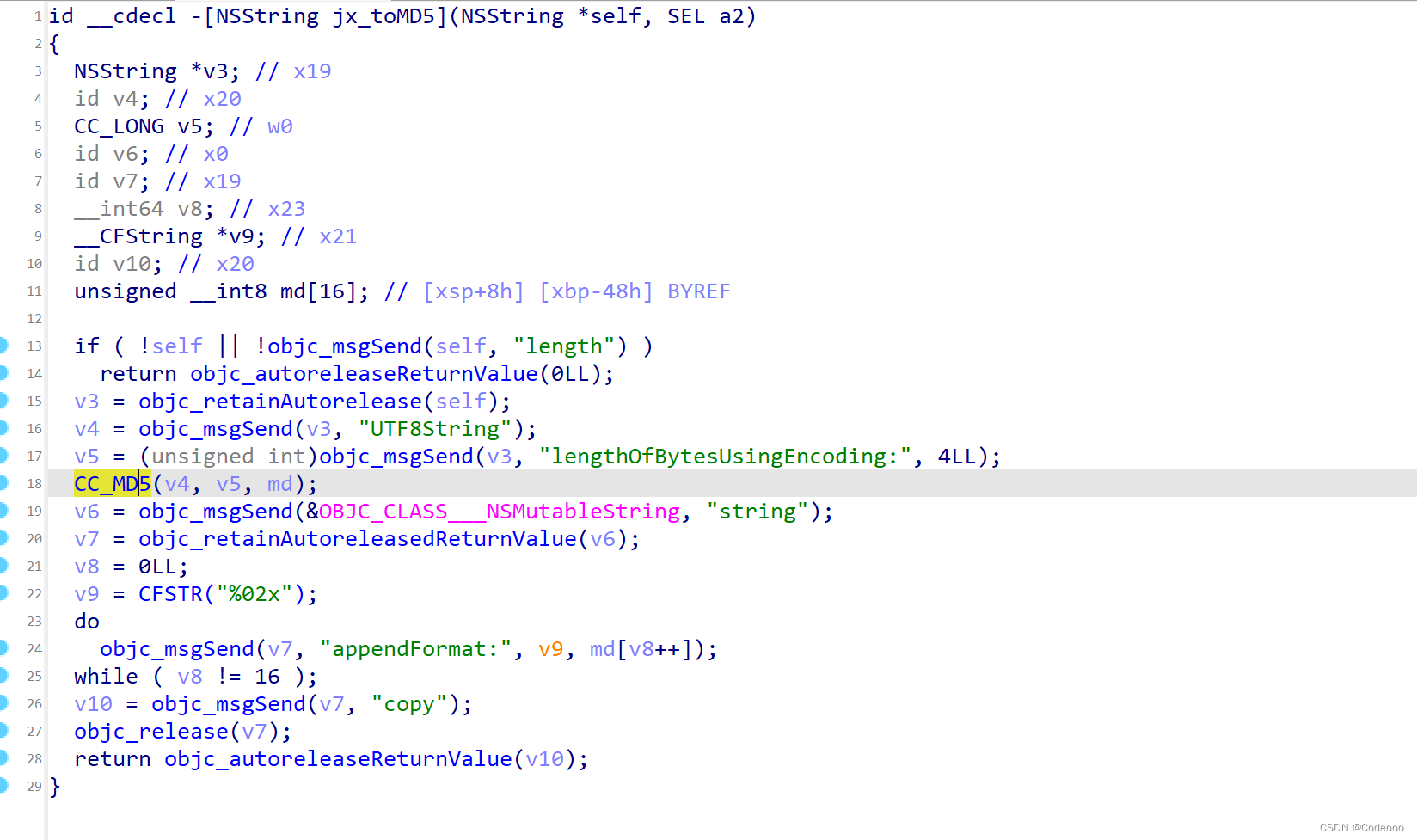
也是个cc_md5;
再往上找:
// 0x10250f07c
/var/containers/Bundle/Application/82E81B77-8825-4ABC-A91F-EABC37E3408D/Driver.app/Driver!-[DrUserLoginViewController
passwordLoginRequestByPhone:ThePassword:]
看到这个函数,我们搞一下:
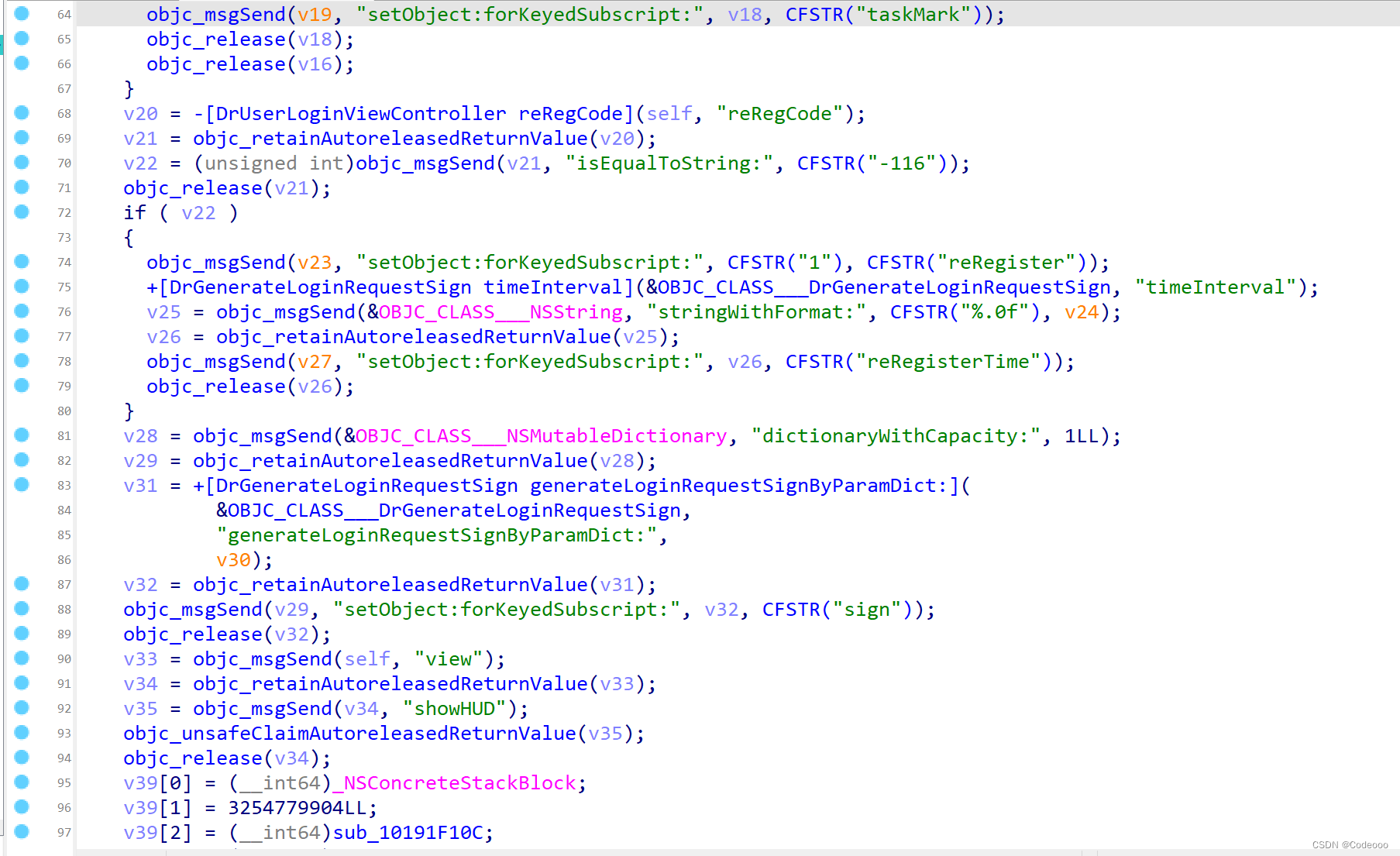
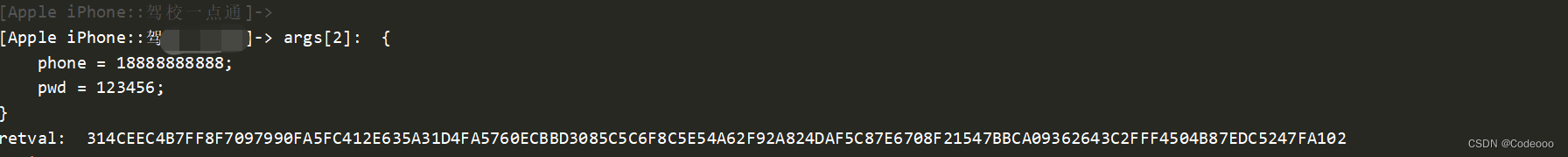
+[DrGenerateLoginRequestSign generateLoginRequestSignByParamDict:]
var initWithMethod = ObjC.classes.DrGenerateLoginRequestSign['+ generateLoginRequestSignByParamDict:'];
Interceptor.attach(initWithMethod.implementation, {
onEnter: function (args) {
console.log("args[2]: ", ObjC.Object(args[2]));
}, onLeave: function (retval) {
console.log("retval: ", ObjC.Object(retval));
}
});
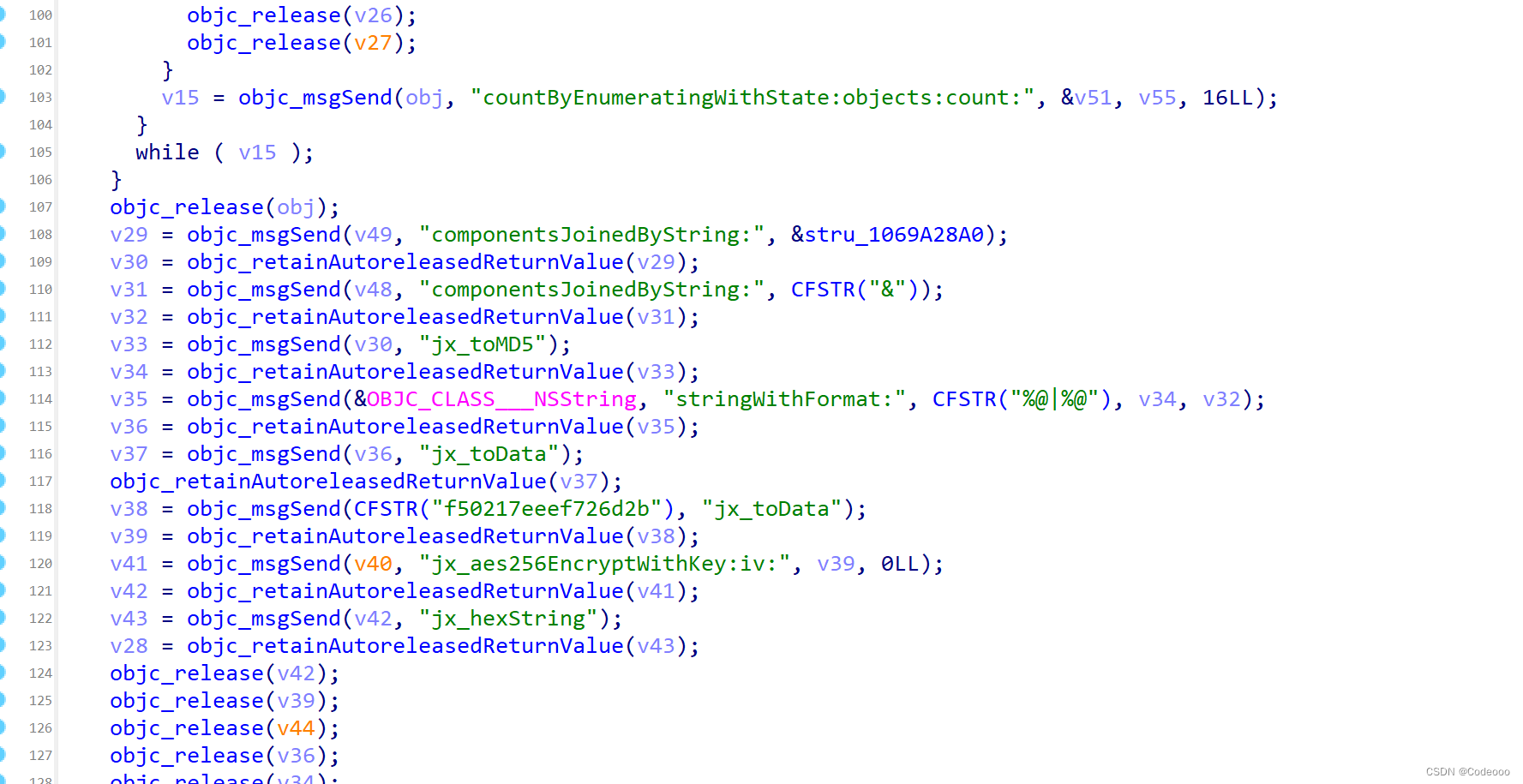
这里面东西不少;
var initWithMethod = ObjC.classes.NSData['- jx_aes256EncryptWithKey:iv:'];
Interceptor.attach(initWithMethod.implementation, {
onEnter: function (args) {
console.log("args[0]: ", ObjC.Object(args[0]));
console.log("args[2]: ", ObjC.Object(args[2]));
console.log("args[3]: ", ObjC.Object(args[3]));
}, onLeave: function (retval) {
console.log("retval: ", ObjC.Object(retval));
}
});
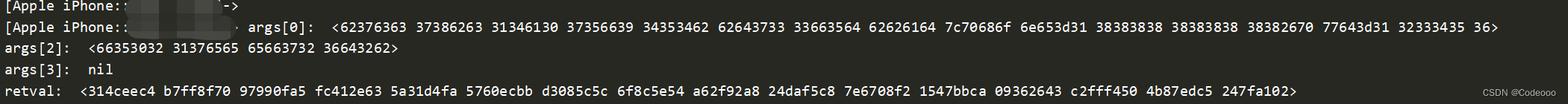
retval:则是 314CEEC4B7FF8F7097990FA5FC412E635A31D4FA5760ECBBD3085C5C6F8C5E54A62F92A824DAF5C87E6708F21547BBCA09362643C2FFF4504B87EDC5247FA102
那我们aes的key找到了 , iv是 nil,那就是ecb模式,无需iv;
再看下data明文,62376363 37386263 31346130 37356639 34353462 62643733 33663564 62626164 7c70686f 6e653d31 38383838 38383838 38382670 77643d31 32333435 36
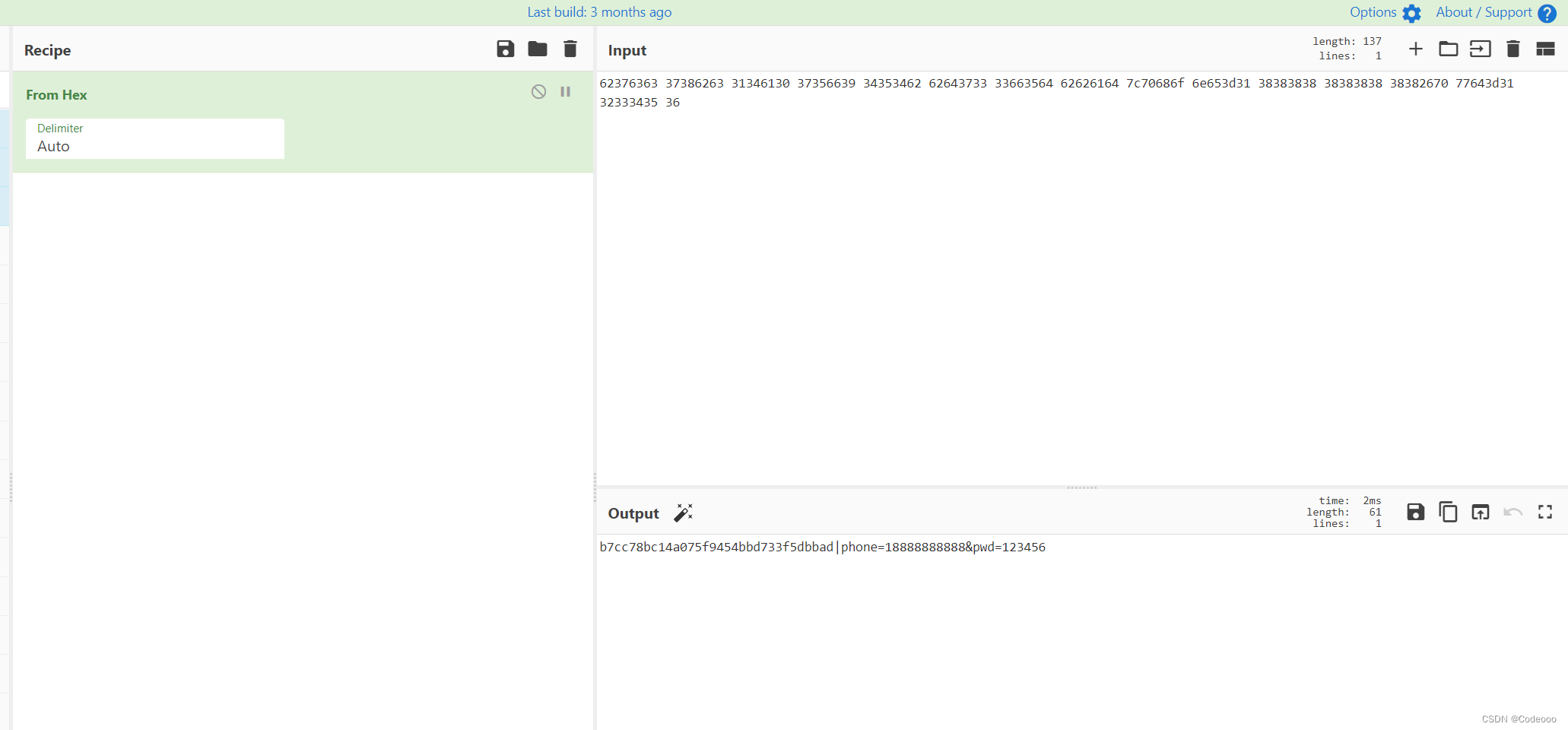
b7cc78bc14a075f9454bbd733f5dbbad|phone=18888888888&pwd=123456
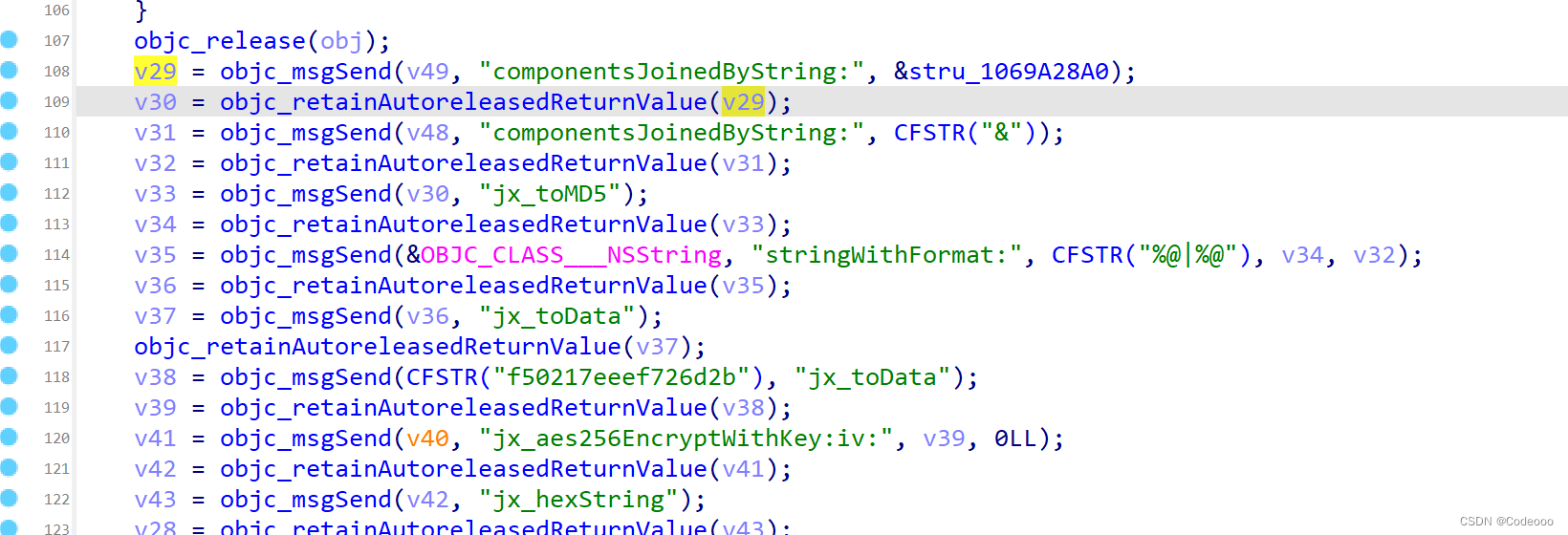
b7cc78bc14a075f9454bbd733f5dbbad 哪里来?
var jx_toMD5 = ObjC.classes.NSString['- jx_toMD5'];
Interceptor.attach(jx_toMD5.implementation, {
onEnter: function (args) {
console.log("args[0]: ", ObjC.Object(args[0]));
}, onLeave: function (retval) {
console.log("retval: ", ObjC.Object(retval));
}
});
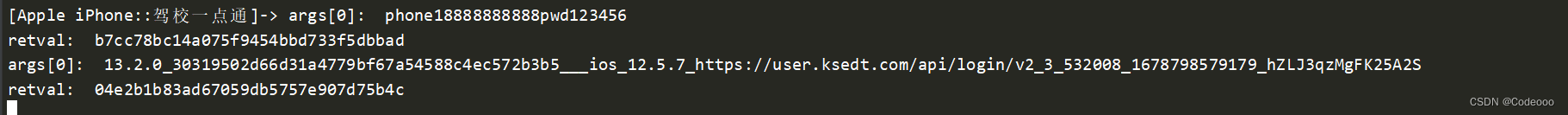
这里就说看出来 b7cc78bc14a075f9454bbd733f5dbbad 这里来;
sign逆向完毕!
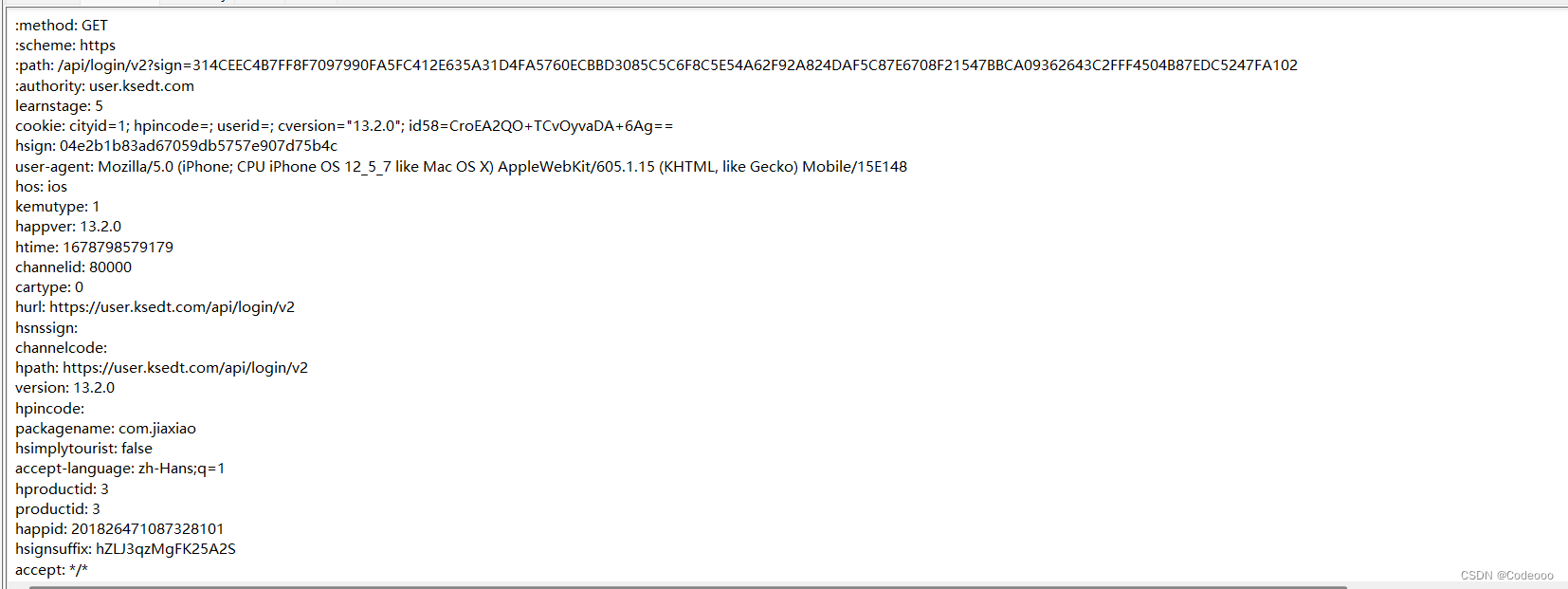
hsign值得到了,其他参数都在请求里,30319502d66d31a4779bf67a54588c4ec572b3b5 这个值哪里来的:固定的吗?固定盐?
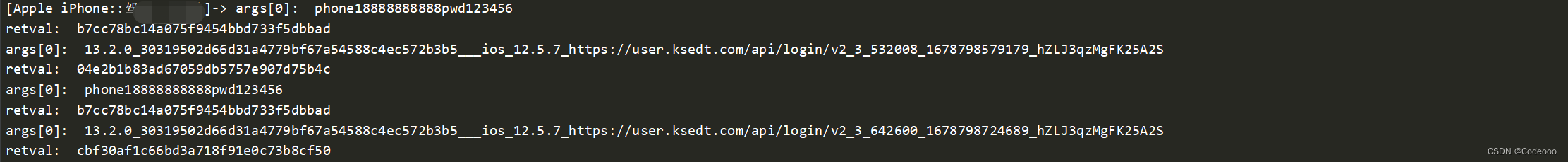
MD5的时候,同时又把 hsign 直接给勾出来了;
hsign 逆向完毕!
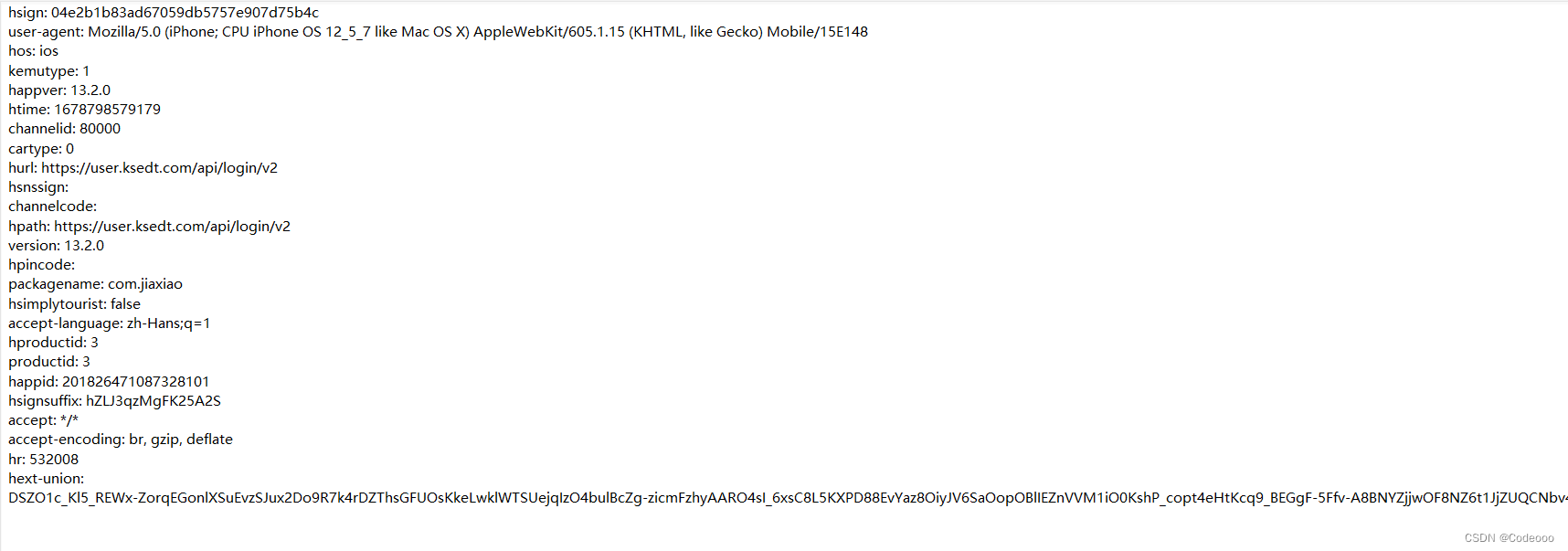
继续看下,hext-union,直接shift + F12, 老话说的好,直接ida搜字符串;
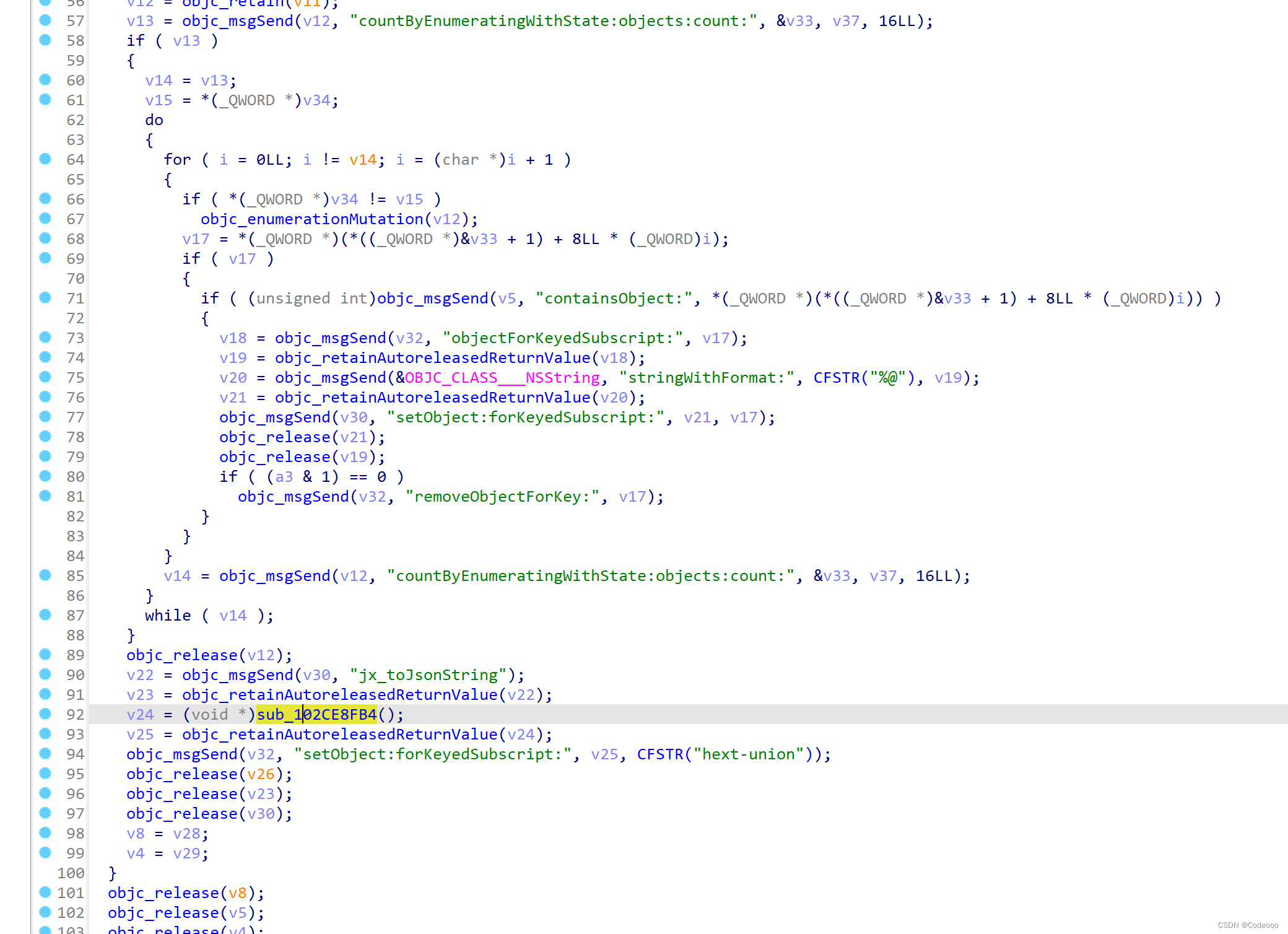
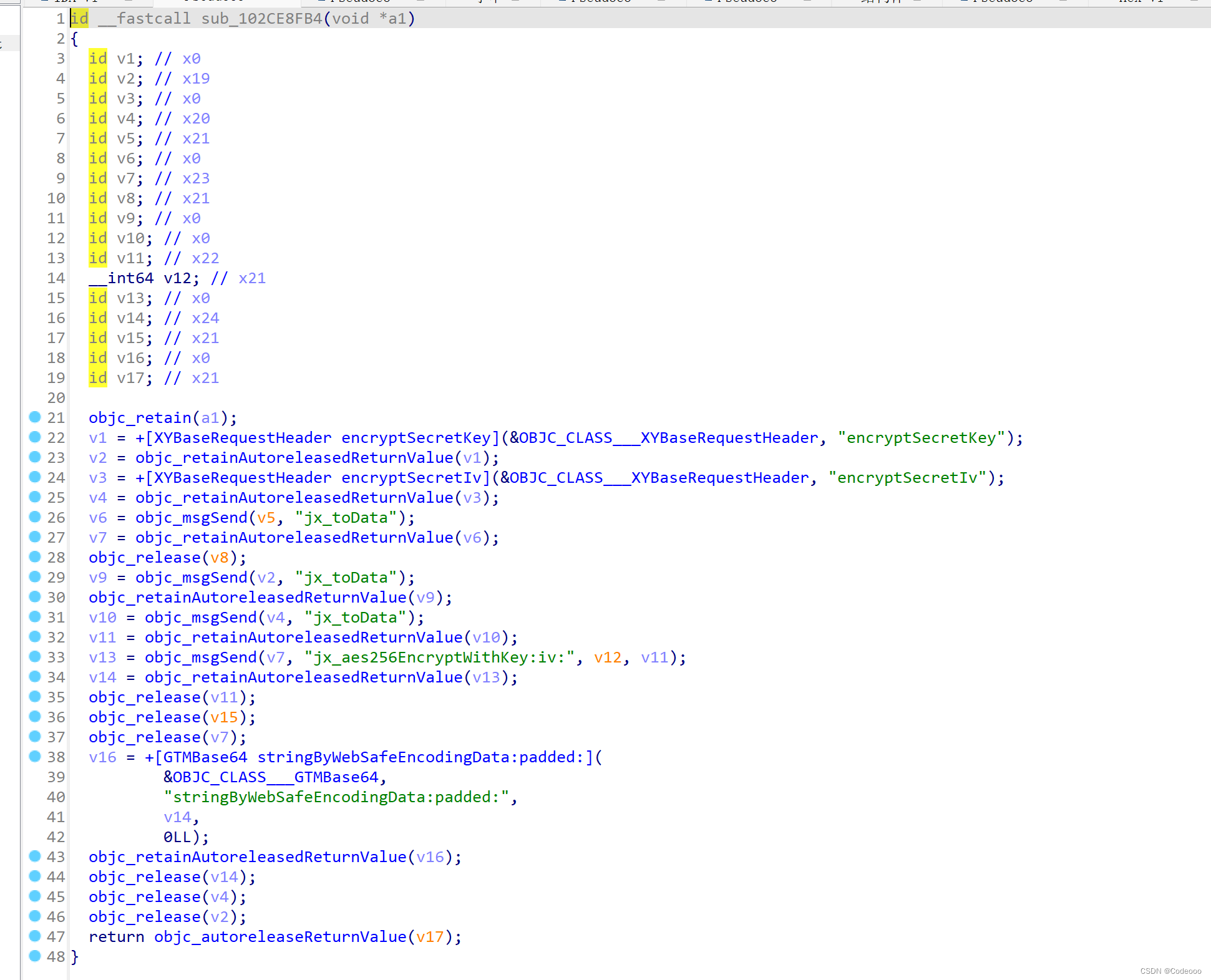
再通过上面hook aes脚本,仔细观察看下:
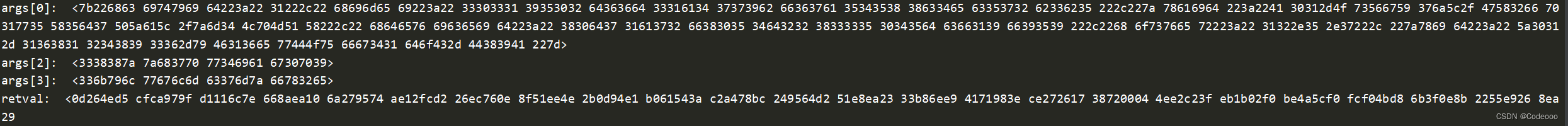
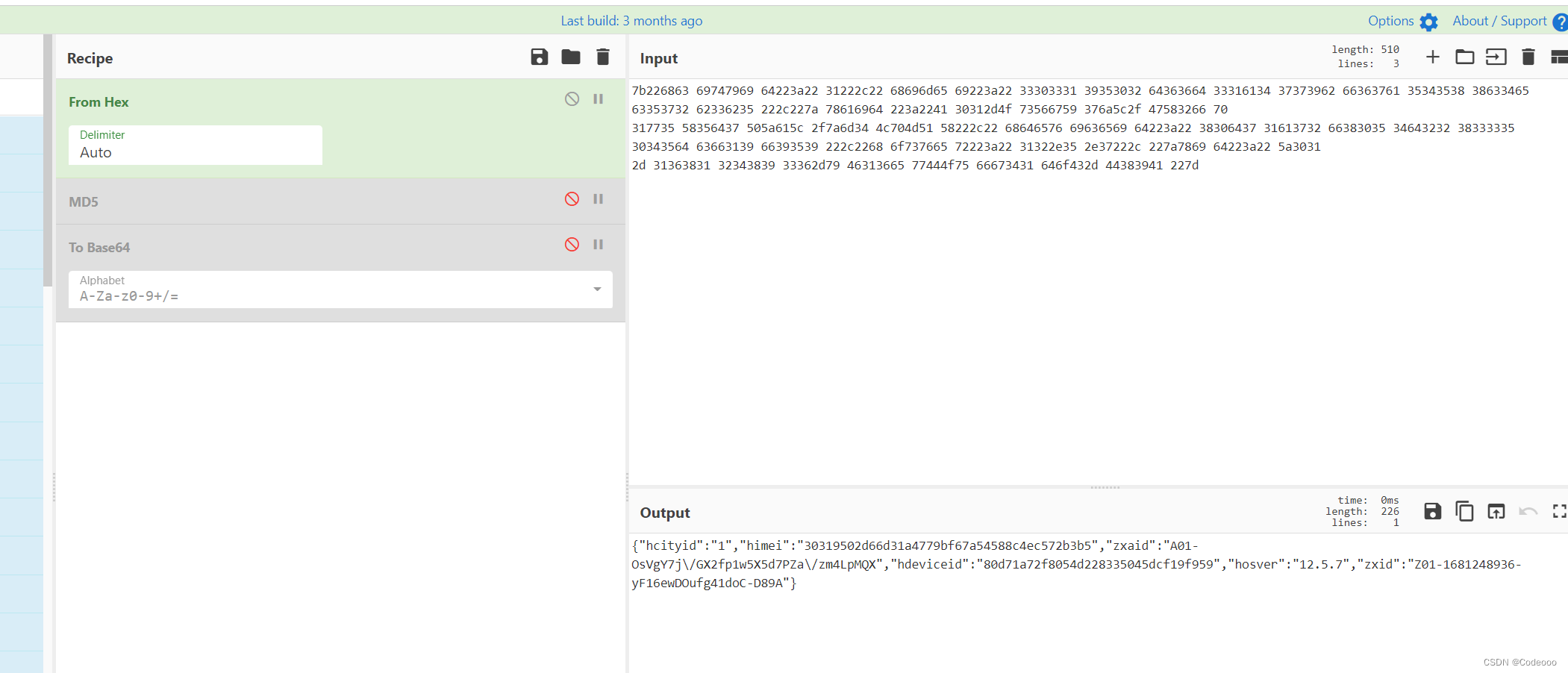
这个是跟设备一些关联;
args[2]: <3338387a 7a683770 77346961 67307039>
args[3]: <336b796c 77676c6d 63376d7a 66783265>
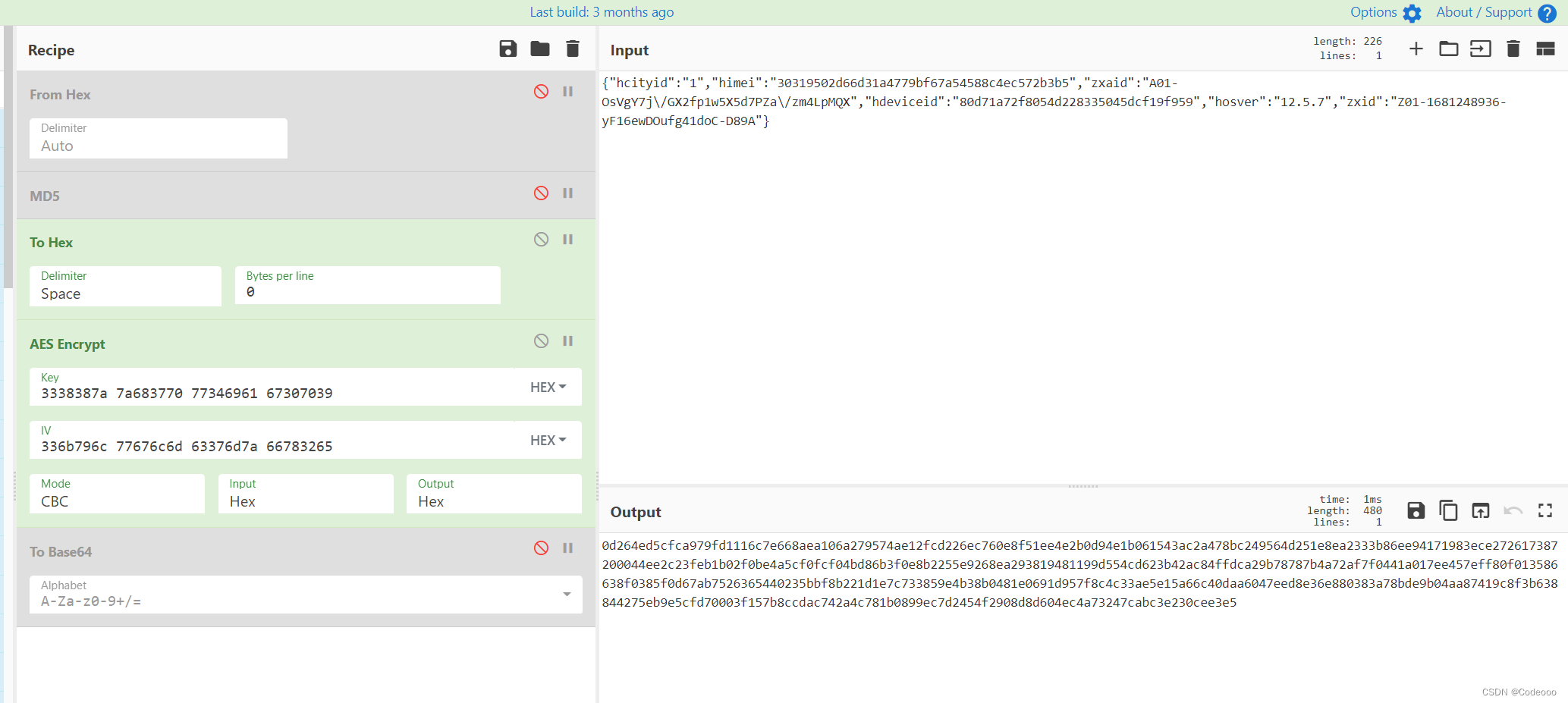
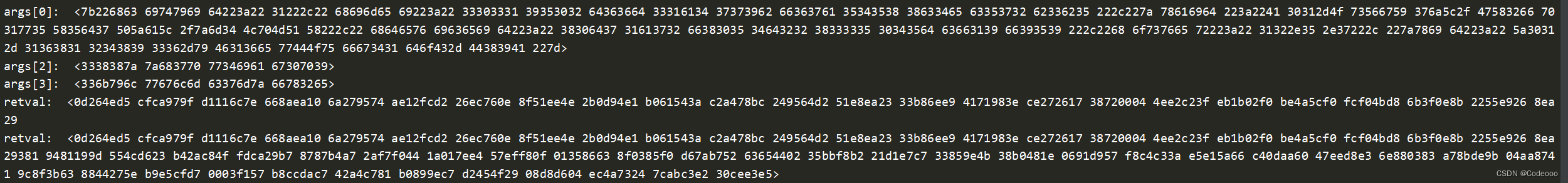
说明秘钥没问题;
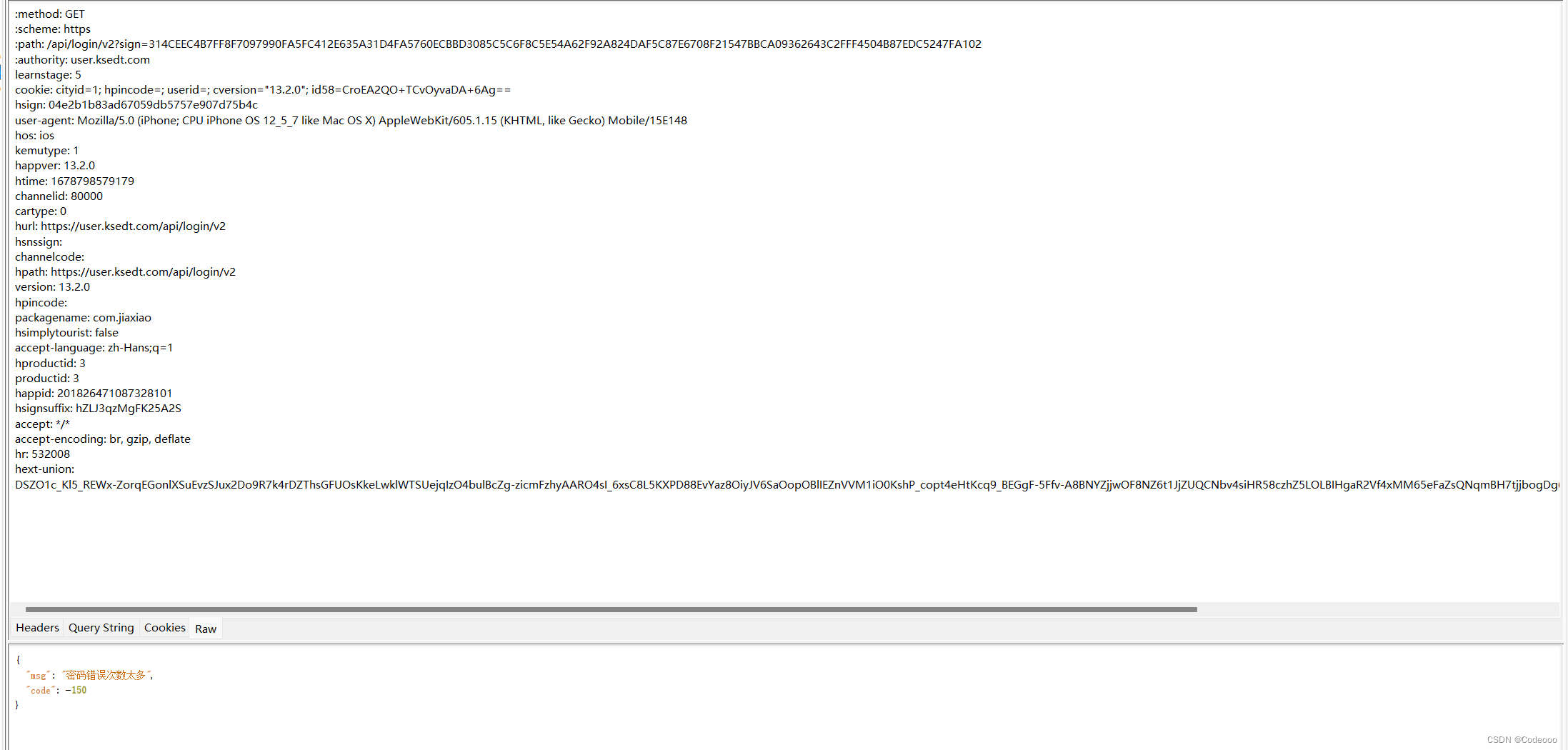
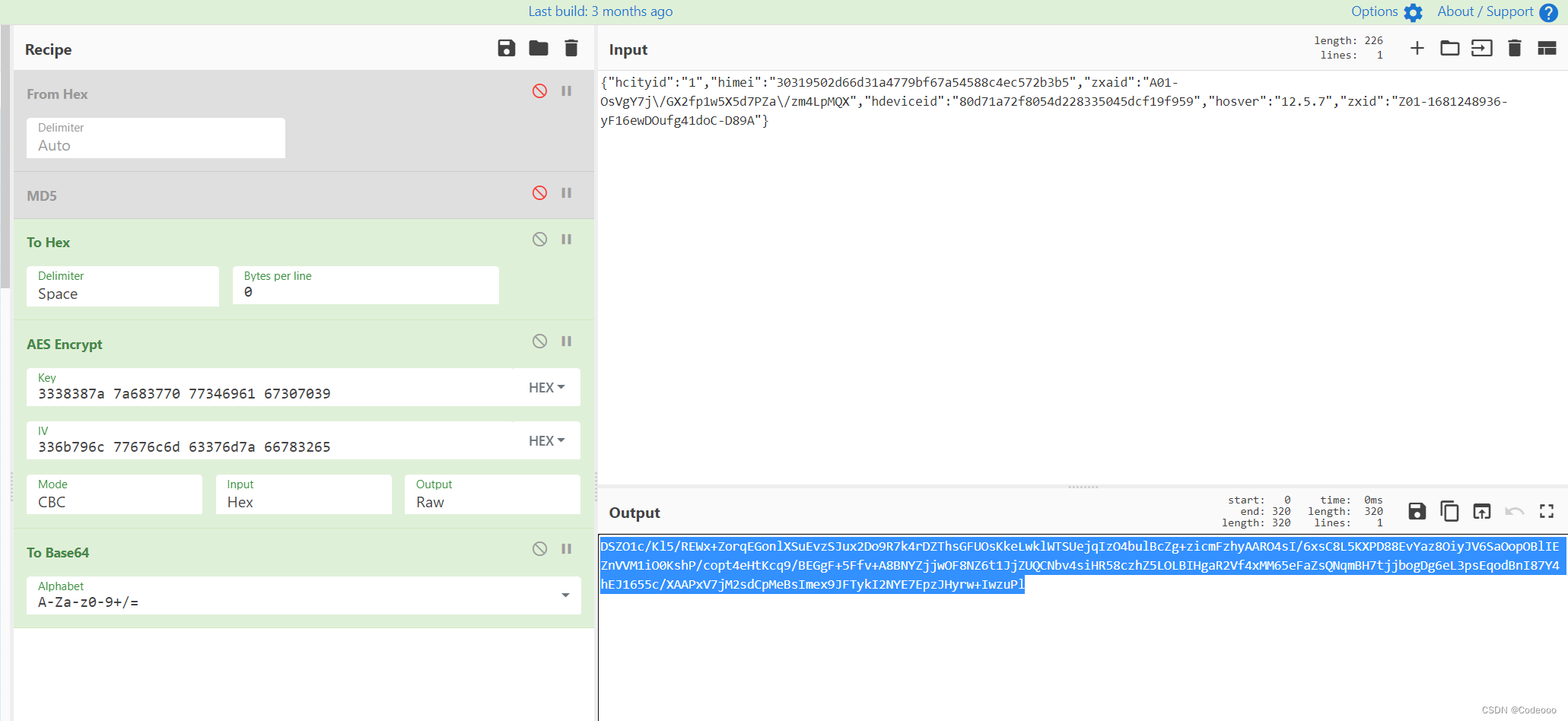
对比下确实是没问题,只不过他的base64将/ + 号等都做了替换;
我们去ida看下是不是码表也有变化,方便我们在页面调整:
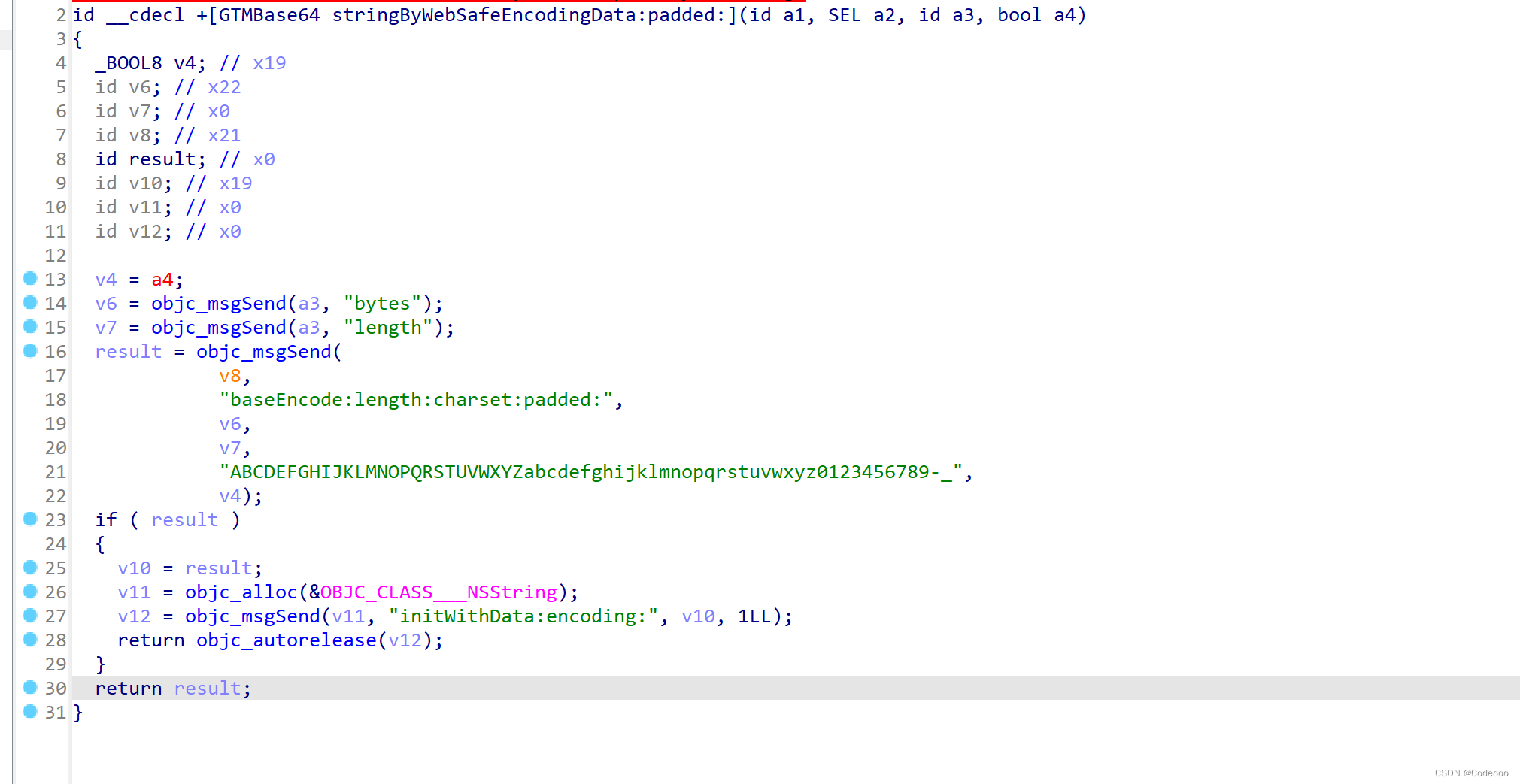
码表搞出来,替换上来:

对比完美结束。
hext-union完毕!
所以说这个CyberChef是真的好用!!!

https://gchq.github.io/CyberChef/#recipe=To_Hex(‘Space’,0)AES_Encrypt(%7B’option’:‘Hex’,‘string’:‘3338387a%207a683770%2077346961%2067307039’%7D,%7B’option’:‘Hex’,‘string’:‘336b796c%2077676c6d%2063376d7a%2066783265’%7D,‘CBC’,‘Hex’,‘Raw’,%7B’option’:‘Hex’,‘string’:‘’%7D)To_Base64(‘A-Za-z0-9-_’)&input=eyJoY2l0eWlkIjoiMSIsImhpbWVpIjoiMzAzMTk1MDJkNjZkMzFhNDc3OWJmNjdhNTQ1ODhjNGVjNTcyYjNiNSIsInp4YWlkIjoiQTAxLU9zVmdZN2pcL0dYMmZwMXc1WDVkN1BaYVwvem00THBNUVgiLCJoZGV2aWNlaWQiOiI4MGQ3MWE3MmY4MDU0ZDIyODMzNTA0NWRjZjE5Zjk1OSIsImhvc3ZlciI6IjEyLjUuNyIsInp4aWQiOiJaMDEtMTY4MTI0ODkzNi15RjE2ZXdET3VmZzQxZG9DLUQ4OUEifQ