GPG Overview
Overview
PGP目前支持的算法
- 非对称算法: RSA, ELG, DSA, ECDH, ECDSA, EDDSA
- 对称算法: IDEA, 3DES, CAST5, BLOWFISH, AES, AES192, AES256, TWOFISH, CAMELLIA128, CAMELLIA192, CAMELLIA256
- 哈希算法: SHA1, RIPEMD160, SHA256, SHA384, SHA512, SHA224
- 压缩算法: Uncompressed, ZIP, ZLIB, BZIP2
除非量子计算机落地,目前来说2048位的RSA加密是不可破解的。
GPG

生成密钥
gpg --gen-key
# or
gpg --full-generate-key
output
gpg (GnuPG) 2.2.4; Copyright (C) 2017 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
Your selection?
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (3072)
Requested keysize is 3072 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0)
Key does not expire at all
Is this correct? (y/N) y
GnuPG needs to construct a user ID to identify your key.
Real name: Gavin Gao
Email address: cggos@outlook.com
Comment:
You selected this USER-ID:
"Gavin Gao <cggos@outlook.com>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? o
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
gpg: key 94FB606ACFB828F6 marked as ultimately trusted
gpg: directory '/home/cg/.gnupg/openpgp-revocs.d' created
gpg: revocation certificate stored as '/home/cg/.gnupg/openpgp-revocs.d/D06142ABCC08402AFCDB2FAF94FB606ACFB828F6.rev'
public and secret key created and signed.
pub rsa3072 2022-04-28 [SC]
D06142ABCC08402AFCDB2FAF94FB606ACFB828F6
uid Gavin Gao <cggos@outlook.com>
sub rsa3072 2022-04-28 [E]
其中,Key ID
94FB606ACFB828F6
私钥的密码为
xxxx gpg
生成子密钥
你日常使用应该使用子密钥,主密钥除了签发新的子密钥不要使用。
建议为不同环境,不同用途都单独生成子密钥,互不干扰。
gpg --edit-key cggos@outlook.com
output
gpg (GnuPG) 2.2.4; Copyright (C) 2017 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Secret key is available.
sec rsa3072/94FB606ACFB828F6
created: 2022-04-28 expires: never usage: SC
trust: ultimate validity: ultimate
ssb rsa3072/BB0088AB554CF92D
created: 2022-04-28 expires: never usage: E
[ultimate] (1). Gavin Gao <cggos@outlook.com>
gpg> addkey
Please select what kind of key you want:
(3) DSA (sign only)
(4) RSA (sign only)
(5) Elgamal (encrypt only)
(6) RSA (encrypt only)
Your selection? 4
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (3072)
Requested keysize is 3072 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0)
Key does not expire at all
Is this correct? (y/N) y
Really create? (y/N) y
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
sec rsa3072/94FB606ACFB828F6
created: 2022-04-28 expires: never usage: SC
trust: ultimate validity: ultimate
ssb rsa3072/BB0088AB554CF92D
created: 2022-04-28 expires: never usage: E
ssb rsa3072/3384DE02354CC62E
created: 2022-04-28 expires: never usage: S
[ultimate] (1). Gavin Gao <cggos@outlook.com>
gpg> save
撤销证书
生成一张"撤销证书",以备以后密钥作废时,可以请求外部的公钥服务器撤销你的公钥
gpg --gen-revoke 94FB606ACFB828F6
output
sec rsa3072/94FB606ACFB828F6 2022-04-28 Gavin Gao <cggos@outlook.com>
Create a revocation certificate for this key? (y/N) y
Please select the reason for the revocation:
0 = No reason specified
1 = Key has been compromised
2 = Key is superseded
3 = Key is no longer used
Q = Cancel
(Probably you want to select 1 here)
Your decision?
Enter an optional description; end it with an empty line:
>
Reason for revocation: Key has been compromised
(No description given)
Is this okay? (y/N) y
ASCII armored output forced.
-----BEGIN PGP PUBLIC KEY BLOCK-----
Comment: This is a revocation certificate
iQG2BCABCgAgFiEE0GFCq8wIQCr82y+vlPtgas+4KPYFAmJqewwCHQIACgkQlPtg
as+4KPYkDgv9FsNmqApXiu/p9y/M9pLQHgnQwmRbmjCEhZ+qpfQX2s5+zhpWQOtj
WqtL9EwM12Wld/aLsFnsjd1cU8hE5FpaPIt3slSNPIjqF5n1JKZqHkK850XKj2Z7
MMBsA6t3P7p7VSpP2oS0/d3q5bio9z37HePlp67gGYMHINsiVfHlrNBCNhhQ8K1q
yZmAORtbr0X2WS+ljG8aqqFg5dlG7WAhK/MugbKIFzdkc5Xugu5oQUgq3uogXGZg
o30/GS4a5KyTNSSWbO1vMA/tfYlhDsN+ywqqrStCGWCjO/JJk9Am6eG16zf9wyCW
PtXjc67X5WiOR+t2SWkbVcGZFJMlAdQwRF/D64qskGvap96qj8+I3U9hNaqG8W5A
5dO+vPEocDhPs0AqGzytFVmG88EyOIenhvVc8xtO9JrkFFUN0XBdsQoA162RH2tv
XH25wy3ZSzkdCXKYlQHFM7SIg6Lhfxl/j3ucueWlVciECEKnqixTw6Uq/Px/T+8h
Fv1vvK63BrJy
=BuV4
-----END PGP PUBLIC KEY BLOCK-----
Revocation certificate created.
Please move it to a medium which you can hide away; if Mallory gets
access to this certificate he can use it to make your key unusable.
It is smart to print this certificate and store it away, just in case
your media become unreadable. But have some caution: The print system of
your machine might store the data and make it available to others!
列出本地密钥
gpg --list-keys
# or
gpg --list-secret-keys
output
/home/cg/.gnupg/pubring.kbx
---------------------------
pub rsa3072 2022-04-28 [SC]
D06142ABCC08402AFCDB2FAF94FB606ACFB828F6
uid [ultimate] Gavin Gao <cggos@outlook.com>
sub rsa3072 2022-04-28 [E]
gpg --list-secret-keys --fingerprint --keyid-format long
gpg --fingerprint -K --keyid-format long
/home/cg/.gnupg/pubring.kbx
---------------------------
sec rsa3072/94FB606ACFB828F6 2022-04-28 [SC]
Key fingerprint = D061 42AB CC08 402A FCDB 2FAF 94FB 606A CFB8 28F6
uid [ultimate] Gavin Gao <cggos@outlook.com>
ssb rsa3072/BB0088AB554CF92D 2022-04-28 [E]
ssb rsa3072/3384DE02354CC62E 2022-04-28 [S]
导出密钥
public key
gpg -ao public-key.txt --export [用户ID]
gpg --armor --output public-key.txt --export 94FB606ACFB828F6
Private Key
你日常使用应该使用子密钥,主密钥除了签发新的子密钥不要使用。
建议为不同环境,不同用途都单独生成子密钥,互不干扰。
gpg --armor --output private-key.txt --export-secret-keys 94FB606ACFB828F6
# keybase
gpg --export-secret-keys -a 94FB606ACFB828F6
# 注意这里最后 要带上“!”, 不然会导出全部子密钥
gpg -ao secret-key.txt --export-secret-key 94FB606ACFB828F6! # 导出主私钥,建议secret-key 替换为你的加密设备备份文件的路径,直接导入到设备中
gpg -ao subkey-s.txt --export-secret-subkeys 3384DE02354CC62E! # 导出有[S]标识、签名用子私钥
gpg -ao subkey-e.txt --export-secret-subkeys BB0088AB554CF92D! # 导出有[E]标识、加密用子私钥 ,这里的ID替换为你的子密钥ID
# 别忘了同时将你刚刚生成的撤销凭证也备份起来
删除本地密钥
gpg --delete-secret-keys [用户ID] # 删除私钥, UID 也可以替换成子密钥ID, 主密钥Key ID
gpg --delete-keys [用户ID] # 删除公钥
gpg --delete-key [用户ID]
# 如果想全部删除推荐直接删文件夹,即删除 $HOME/.gnupg
gpg (GnuPG) 2.2.4; Copyright (C) 2017 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
sec rsa3072/94FB606ACFB828F6 2022-04-28 Gavin Gao <cggos@outlook.com>
Delete this key from the keyring? (y/N) y
This is a secret key! - really delete? (y/N) y
pub rsa3072/94FB606ACFB828F6 2022-04-28 Gavin Gao <cggos@outlook.com>
Delete this key from the keyring? (y/N) y
公钥服务器
keyserver
- keys.openpgp.org
- keyserver.ubuntu.com
- pgp.mit.edu
- subkeys.pgp.net
- www.gpg-keyserver.de
配置 默认
# ~/.gnupg/gpg.conf
keyserver hkps://keys.openpgp.org
keyid-format 0xlong
with-fingerprint
上传
gpg --keyserver hkps://keys.openpgp.org --send-keys 94FB606ACFB828F6
验证邮箱
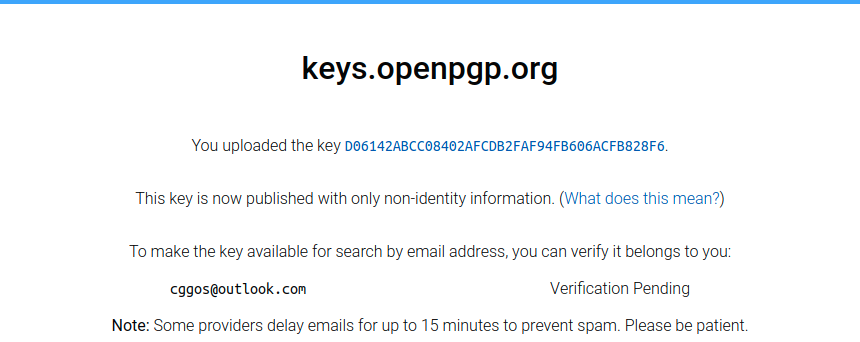
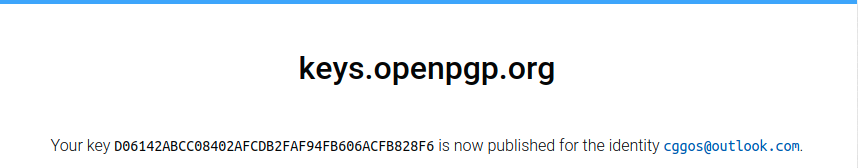
浏览器搜索查询
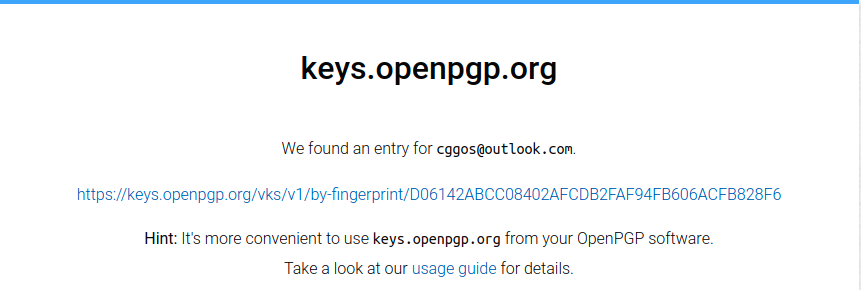
搜索
gpg --keyserver hkps://keys.openpgp.org --search-keys 94FB606ACFB828F6
# or
gpg --keyserver hkps://keys.openpgp.org --search-keys cggos@outlook.com
output
gpg: data source: https://keys.openpgp.org:443
(1) Gavin Gao <cggos@outlook.com>
3072 bit RSA key 94FB606ACFB828F6, created: 2022-04-28
Keys 1-1 of 1 for "94FB606ACFB828F6". Enter number(s), N)ext, or Q)uit > N
公钥指纹
由于公钥服务器没有检查机制,任何人都可以用你的名义上传公钥,所以没有办法保证服务器上的公钥的可靠性。通常,你可以在网站上公布一个公钥指纹,让其他人核对下载到的公钥是否为真。fingerprint参数生成公钥指纹。
gpg --fingerprint 94FB606ACFB828F6
gpg --fingerprint -K --keyid-format long
output
pub rsa3072 2022-04-28 [SC]
D061 42AB CC08 402A FCDB 2FAF 94FB 606A CFB8 28F6
uid [ultimate] Gavin Gao <cggos@outlook.com>
sub rsa3072 2022-04-28 [E]
导入密钥
从文件import
gpg --import [密钥文件] # 刚刚备份的子密钥文件, 或者其他人的公钥
gpg --import subkey-s.txt
gpg: key 94FB606ACFB828F6: "Gavin Gao <cggos@outlook.com>" not changed
gpg: To migrate 'secring.gpg', with each smartcard, run: gpg --card-status
gpg: key 94FB606ACFB828F6: secret key imported
gpg: Total number processed: 1
gpg: unchanged: 1
gpg: secret keys read: 1
gpg: secret keys imported: 1
从公钥服务器上获取公钥:
gpg --keyserver keys.openpgp.org --recv-keys 94FB606ACFB828F6
output
gpg: key 94FB606ACFB828F6: public key "Gavin Gao <cggos@outlook.com>" imported
gpg: Total number processed: 1
gpg: imported: 1
Keybase
keybase pgp select
You are selecting a PGP key from your local GnuPG keychain, and
will publish a statement signed with this key to make it part of
your Keybase.io identity.
Note that GnuPG will prompt you to perform this signature.
You can also import the secret key to *local*, *encrypted* Keybase
keyring, enabling decryption and signing with the Keybase client.
To do that, use "--import" flag.
Learn more: keybase pgp help select
# Algo Key Id Created UserId
= ==== ====== ======= ======
1 3072R 94FB606ACFB828F6 Gavin Gao <cggos@outlook.com>
Choose a key: 1
▶ INFO Generated new PGP key:
▶ INFO user: Gavin Gao <cggos@outlook.com>
▶ INFO 3072-bit RSA key, ID 94FB606ACFB828F6, created 2022-04-28
应用
文件验证
签名
gpg --detach-sign demo.txt
验证
gpg --verify demo.txt.sig demo.txt
gpg: Signature made Thu 28 Apr 2022 08:14:27 PM CST
gpg: using RSA key C8BA9D0647339A178B7545F03384DE02354CC62E
gpg: Good signature from "Gavin Gao <cggos@outlook.com>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: D061 42AB CC08 402A FCDB 2FAF 94FB 606A CFB8 28F6
Subkey fingerprint: C8BA 9D06 4733 9A17 8B75 45F0 3384 DE02 354C C62E
信任
gpg --edit-key cggos@outlook.com
gpg (GnuPG) 2.2.4; Copyright (C) 2017 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
pub rsa3072/94FB606ACFB828F6
created: 2022-04-28 expires: never usage: SC
trust: unknown validity: unknown
sub rsa3072/3384DE02354CC62E
created: 2022-04-28 expires: never usage: S
sub rsa3072/BB0088AB554CF92D
created: 2022-04-28 expires: never usage: E
[ unknown] (1). Gavin Gao <cggos@outlook.com>
gpg> trust
pub rsa3072/94FB606ACFB828F6
created: 2022-04-28 expires: never usage: SC
trust: unknown validity: unknown
sub rsa3072/3384DE02354CC62E
created: 2022-04-28 expires: never usage: S
sub rsa3072/BB0088AB554CF92D
created: 2022-04-28 expires: never usage: E
[ unknown] (1). Gavin Gao <cggos@outlook.com>
Please decide how far you trust this user to correctly verify other users' keys
(by looking at passports, checking fingerprints from different sources, etc.)
1 = I don't know or won't say
2 = I do NOT trust
3 = I trust marginally
4 = I trust fully
5 = I trust ultimately
m = back to the main menu
Your decision? 5
Do you really want to set this key to ultimate trust? (y/N) y
pub rsa3072/94FB606ACFB828F6
created: 2022-04-28 expires: never usage: SC
trust: ultimate validity: unknown
sub rsa3072/3384DE02354CC62E
created: 2022-04-28 expires: never usage: S
sub rsa3072/BB0088AB554CF92D
created: 2022-04-28 expires: never usage: E
[ unknown] (1). Gavin Gao <cggos@outlook.com>
Please note that the shown key validity is not necessarily correct
unless you restart the program.
gpg>
gpg: signal Interrupt caught ... exiting
git
https://docs.github.com/cn/authentication/managing-commit-signature-verification
**能用来放在博客简介里作为身份的象征 增加联系你的安全方式
用来代替SSH
涌有了自己pgp key之后,就可以用 gpg-agent 来代替 OpenSSH Agent来进行 SSH操作了。不过替换了之后并不会增加SSH的安全性,额, 折腾精神不死嘛。
硬要说好处的话,大概就可以更方便地使用Yubikey(一种硬件加密智能卡)来SSH。
apt-get
apt-get update 或者aptitude update出现以下错误:
The following signatures couldn’t be verified because the public key is not available: : NO_PUBKEY B5B7720097BB3B58
解决方法:
# 从任何一个key server获得缺失的公钥B5B7720097BB3B58。
gpg --keyserver subkeys.pgp.net --recv-keys B5B7720097BB3B58
# 导入公钥B5B7720097BB3B58。
gpg -a --export B5B7720097BB3B58 | sudo apt-key add -
curl -s https://raw.githubusercontent.com/ros/rosdistro/master/ros.asc | sudo apt-key add -
